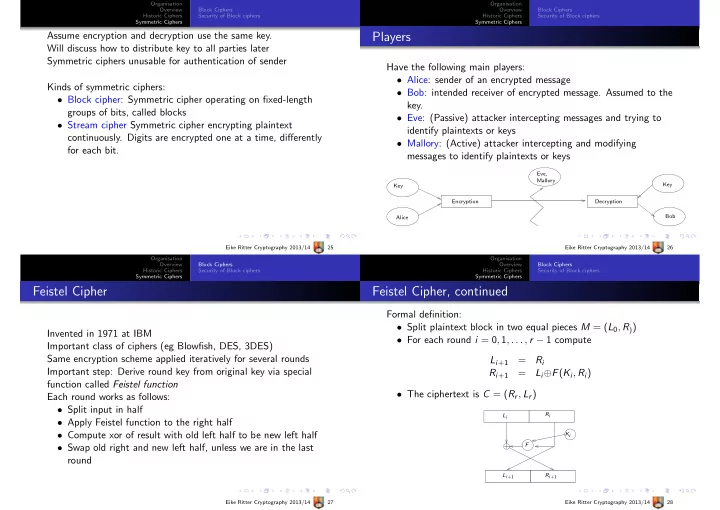

Organisation Organisation Overview Block Ciphers Overview Block Ciphers Historic Ciphers Security of Block ciphers Historic Ciphers Security of Block ciphers Symmetric Ciphers Symmetric Ciphers Assume encryption and decryption use the same key. Players Will discuss how to distribute key to all parties later Symmetric ciphers unusable for authentication of sender Have the following main players: • Alice: sender of an encrypted message Kinds of symmetric ciphers: • Bob: intended receiver of encrypted message. Assumed to the • Block cipher: Symmetric cipher operating on fixed-length key. groups of bits, called blocks • Eve: (Passive) attacker intercepting messages and trying to • Stream cipher Symmetric cipher encrypting plaintext identify plaintexts or keys continuously. Digits are encrypted one at a time, differently • Mallory: (Active) attacker intercepting and modifying for each bit. messages to identify plaintexts or keys Eve, Mallory Key Key Encryption Decryption Bob Alice Eike Ritter Cryptography 2013/14 25 Eike Ritter Cryptography 2013/14 26 Organisation Organisation Overview Block Ciphers Overview Block Ciphers Historic Ciphers Security of Block ciphers Historic Ciphers Security of Block ciphers Symmetric Ciphers Symmetric Ciphers Feistel Cipher Feistel Cipher, continued Formal definition: • Split plaintext block in two equal pieces M = ( L 0 , R ) ) Invented in 1971 at IBM • For each round i = 0 , 1 , . . . , r − 1 compute Important class of ciphers (eg Blowfish, DES, 3DES) Same encryption scheme applied iteratively for several rounds = L i +1 R i Important step: Derive round key from original key via special = L i ⊕ F ( K i , R i ) R i +1 function called Feistel function • The ciphertext is C = ( R r , L r ) Each round works as follows: • Split input in half R i L i • Apply Feistel function to the right half • Compute xor of result with old left half to be new left half K i F • Swap old right and new left half, unless we are in the last round L i +1 R i +1 Eike Ritter Cryptography 2013/14 27 Eike Ritter Cryptography 2013/14 28
Organisation Organisation Overview Block Ciphers Overview Block Ciphers Historic Ciphers Security of Block ciphers Historic Ciphers Security of Block ciphers Symmetric Ciphers Symmetric Ciphers Decryption DES Works as encryption, but with a reversed order of keys • Split ciphertext block in two equal pieces C = ( R r , L R ) Data Encryption Standard (DES) adopted in 1976 • For each round i = r , r − 1 , . . . , 1 compute Key size too small for today’s computers (can be broken within 10 hours) R i − 1 = L i Variants still provide good security L i − 1 = R i ⊕ F ( K i − 1 , L i ) • Plaintext is M = ( L 0 , R 0 ) Eike Ritter Cryptography 2013/14 29 Eike Ritter Cryptography 2013/14 30 Organisation Organisation Overview Block Ciphers Overview Block Ciphers Historic Ciphers Security of Block ciphers Historic Ciphers Security of Block ciphers Symmetric Ciphers Symmetric Ciphers Overview of DES Design parameters R i Plaintext Block L i K i Initial Permutation IP F • Block length is 64 bits • Number of rounds R is 16 R 0 L 0 • Key length is is 56 bits L i +1 R i +1 • Round key length is 48 bit for each subkey K 0 , . . . , K 15 . Subkeys are derived from 56 bit key via special key schedule. L 16 R 16 Final Permutation IP − 1 Ciphertext block Eike Ritter Cryptography 2013/14 31 Eike Ritter Cryptography 2013/14 32
Organisation Organisation Overview Block Ciphers Overview Block Ciphers Historic Ciphers Security of Block ciphers Historic Ciphers Security of Block ciphers Symmetric Ciphers Symmetric Ciphers DES Feistel function DES Feistel function, continued Four stage procedure: • Expansion permutation: Expand 32-bit message half block to 48 bit block by doubling 16 bits and permuting them • Round key addition: Compute xor of this 48 bit block with round key K i • S-Box: Split 48 bit into eight 6-bit blocks. Each of them is given as input to eight substitution boxes, which substitute 6-bit block by 4-bit block. • P-Box: Combine these eight 4-bit blocks to 32-bit block and apply another permutation. Source: Wikipedia Eike Ritter Cryptography 2013/14 33 Eike Ritter Cryptography 2013/14 34 Organisation Organisation Overview Block Ciphers Overview Block Ciphers Historic Ciphers Security of Block ciphers Historic Ciphers Security of Block ciphers Symmetric Ciphers Symmetric Ciphers DES-operations S-boxes Have three special operations: • Cyclic shifts on bitstring blocks: Will denote by b <<< n the move of the bits of block b by n to the left. Bits that would • S-boxes: An S-box substitution is a table lookup. Input is 6 have fallen out are added at the right side of the b . b >>> n bit, output is 4 bit. Works as follows: is defined similarly • Strip out outer bits of input and join them. This two-bit • Permutations: Note: might duplicate or drop bits. Written number is the row index. down as output order of the input bits. • Four inner bits indicate column number. Example: the permutation 4 1 2 3 means that • Output is corresponding entry in table • the fourth input bit becomes the first output bit, • the first input bit becomes the second output bit, • the second input bit becomes the third output bit, and • the third input bit becomes the fourth output bit. Eike Ritter Cryptography 2013/14 35 Eike Ritter Cryptography 2013/14 36
Organisation Organisation Overview Block Ciphers Overview Block Ciphers Historic Ciphers Security of Block ciphers Historic Ciphers Security of Block ciphers Symmetric Ciphers Symmetric Ciphers Key schedule Have different keys for each round, computed by so-called Key schedule 64-bit key is actually 56-bit key plus 8 parity bits Definition • Apply permutation to the 56-bit and split result into half to A function ǫ : N → R + is called negligible if for all d there exists a obtain ( C 0 , D 0 ) λ d such that for all λ ≥ λ d , • For each round we compute ǫ ( λ ) ≤ 1 C i = C i − 1 <<< p i λ d = D i D i − 1 <<< p i where � 1 if i = 1 , 2 , 9 , 16 p i = 2 otherwise • C i and D i are joined together and permuted again. Eike Ritter Cryptography 2013/14 37 Eike Ritter Cryptography 2013/14 38 Organisation Organisation Overview Block Ciphers Overview Block Ciphers Historic Ciphers Security of Block ciphers Historic Ciphers Security of Block ciphers Symmetric Ciphers Symmetric Ciphers Definition Let F be the set of all permutations on X , and E an efficient Definition permutation over ( K , X ) and let b ∈ { 0 , 1 } . Define EXP ( b ) to be A efficient permutation over ( K , X ) is a function the following game between the attacker and the challenger: If b = 0, the challenger chooses a k ∈ K at random, and if E : K × X → X b = 1, the challenger chooses a permutation f on X at random. such that The attacker does arbitrary computations. there exists an efficient deterministic algorithm to compute E ( k , x ) for any k and x ; The attacker has access to a black box, which is a function from X to X operated by the challenger. He can ask the The function E ( k , ) is one-to-one for each k challenger for the values g ( x 1 ) , . . . , g ( x n ) during his There exists a function D : K × X → X which is efficiently computation. computable, and D ( k , E ( k , x )) = x for all k and x . If b = 0, the challenger answers the query g ( x i ) by returning E ( k , x i ), and if b = 1, the answer is f ( x i ). Eventually the attacker outputs a bit b ′ ∈ { 0 , 1 } . Eike Ritter Cryptography 2013/14 39 Eike Ritter Cryptography 2013/14 40
Organisation Overview Block Ciphers Historic Ciphers Security of Block ciphers Symmetric Ciphers Definition An efficient permutation E : K × X → X is secure if for all efficient attackers A , Adv [ A , E ] = | Pr k ∈ K [ EXP (0) = 1] − Pr f ∈F [ EXP (1) = 1] | is negligible. Eike Ritter Cryptography 2013/14 41
Recommend
More recommend