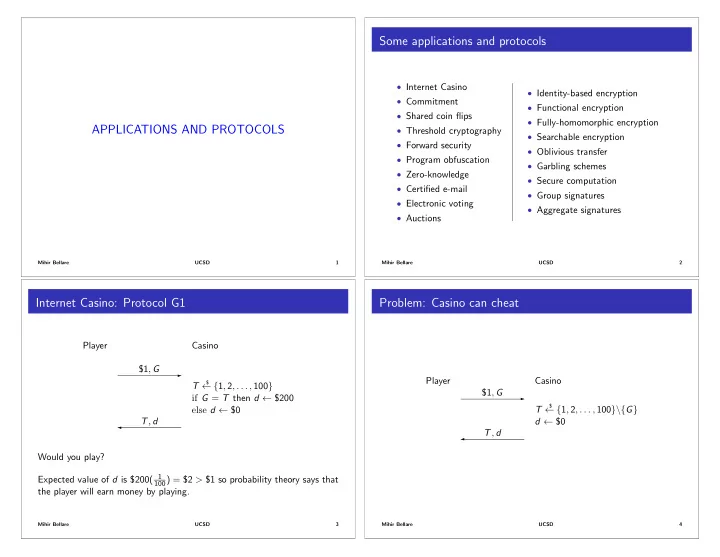

Some applications and protocols • Internet Casino • Identity-based encryption • Commitment • Functional encryption • Shared coin flips • Fully-homomorphic encryption APPLICATIONS AND PROTOCOLS • Threshold cryptography • Searchable encryption • Forward security • Oblivious transfer • Program obfuscation • Garbling schemes • Zero-knowledge • Secure computation • Certified e-mail • Group signatures • Electronic voting • Aggregate signatures • Auctions Mihir Bellare UCSD 1 Mihir Bellare UCSD 2 Internet Casino: Protocol G1 Problem: Casino can cheat Player Casino $1 , G - Player Casino $ T { 1 , 2 , . . . , 100 } $1 , G if G = T then d $200 - $ { 1 , 2 , . . . , 100 }\{ G } else d $0 T T , d d $0 � T , d � Would you play? Expected value of d is $200( 1 100 ) = $2 > $1 so probability theory says that the player will earn money by playing. Mihir Bellare UCSD 3 Mihir Bellare UCSD 4
Internet Casino: Protocol G2 Internet Casino problem Player Casino $1 - $ T { 1 , 2 , . . . , 100 } Player and Casino need to exchange G , T so that T • Casino cannot choose T as a function of G . � G • Player cannot choose G as a function of T . - if G = T then d $200 How do we resolve this Catch-22 situation? else d $0 d � But now player can always win by setting G = T . No casino would do this! Mihir Bellare UCSD 5 Mihir Bellare UCSD 6 ”Internet” Casino: Protocol G3 “Internet” Casino: Protocol G3 Player Casino Player Casino G $1, G $1, $ { 1 , 2 , . . . , 100 } T $ T { 1 , 2 , . . . , 100 } T T G G G G if G = T then d $200 if G = T then d $200 d else d $0 d else d $0 is a locked safe containing a piece of paper with G • Casino cannot choose T as a function of G because, without the key, written on it. it cannot see G . • Player cannot choose G as a function of T because, by putting it in is a key to open the safe. the safe, she is committed to it in the first move. Mihir Bellare UCSD 7 Mihir Bellare UCSD 8
Internet Casino Protocol using cryptography Commitment Schemes A commitment scheme CS = ( P , C , V ) is a triple of algorithms Player Casino P π { 0 , 1 } 128 $ K M C C C C H ( K k G ) - $ T { 1 , 2 , . . . , 100 } K T V 0/1 � G , K - if ( H ( K k G ) = C and G = T ) Parameter generation algorithm P is run once by a trusted party to then d $99 else d $0 produce public parameters π . d � In Internet Casino M Data being commited G Here H is a cryptographic hash function. More generally one can use a C Commital primitive called a committment scheme . K Decommital key Mihir Bellare UCSD 9 Mihir Bellare UCSD 10 Security properties Internet Casino Protocol using a commitment scheme $ • Hiding: A commital C generated via ( C , K ) C ( π , M ) should not reveal information about M. = C does not reveal M. Player Casino C $ ( C , K ) C ( π , G ) - $ { 1 , 2 , . . . , 100 } T • Binding: It should be hard to find C , M 0 , M 1 , K 0 , K 1 such that T M 0 6 = M 1 but V ( π , C , M 0 , K 0 ) = V ( π , C , M 1 , K 1 ) = 1. � G , K - if ( V ( π , C , G , K ) = 1 and G = T ) K 0 C then d $99 M 0 else d $0 d � M 1 K 1 C Mihir Bellare UCSD 11 Mihir Bellare UCSD 12
Hiding Formally Binding Formally Let CS = ( P , C , V ) be a commitment scheme and A an adversary. Let CS = ( P , C , V ) be a commitment scheme and A an adversary. procedure LR ( M 0 , M 1 ) Game BIND CS procedure Finalize ( C , M 0 , M 1 , K 0 , K 1 ) Game HIDE CS $ ( C , K ) C ( π , M b ) v 0 V ( π , C , M 0 , K 0 ) procedure Initialize procedure Initialize return C v 1 V ( π , C , M 1 , K 1 ) $ P $ $ P ; b { 0 , 1 } π π procedure Finalize ( b 0 ) return ( v 0 = v 1 = 1 and M 0 6 = M 1 ) return π return π return ( b = b 0 ) The binding-advantage of A is The hiding-advantage of A is h i Adv bind BIND A CS ( A ) = Pr CS ) true . h i Adv hide HIDE A CS ( A ) = 2 · Pr CS ) true � 1 . Mihir Bellare UCSD 13 Mihir Bellare UCSD 14 Commitment from symmetric encryption Commitment from symmetric encryption Let SE = ( K , E , D ) be an IND-CPA-secure symmetric encryption scheme Let SE = ( K , E , D ) be an IND-CPA-secure symmetric encryption scheme and let CS = ( P , C , V ) be the commitment scheme where P returns π = ε and let CS = ( P , C , V ) be the commitment scheme where P returns π = ε and and Alg C ( π , M ) Alg C ( π , M ) Alg V ( π , C , M , K ) Alg V ( π , C , M , K ) $ $ $ $ if D K ( C ) = M then return 1 if D K ( C ) = M then return 1 K ; C E K ( M ) K ; C E K ( M ) K K return ( C , K ) else return 0 return ( C , K ) else return 0 Is this secure? Is this secure? • Certainly hiding since SE is IND-CPA. Mihir Bellare UCSD 15 Mihir Bellare UCSD 16
Commitment from symmetric encryption Surfacing randomness in asymmetric encryption Let AE = ( K , E , D ) be an asymmetric encryption scheme. Then Let SE = ( K , E , D ) be an IND-CPA-secure symmetric encryption scheme and let CS = ( P , C , V ) be the commitment scheme where P returns π = ε E pk ( M ; K ) is the result of encrypting M with coins (randomness) set to K . and Thus, the following processes return the same thing: $ $ Alg C ( π , M ) E pk ( M ) Coins ( pk ) ; C E pk ( M ; K ) Alg V ( π , C , M , K ) C K Return C Return C $ $ if D K ( C ) = M then return 1 K ; C E K ( M ) K return ( C , K ) else return 0 Here Coins ( pk ) is the space from which the randomness (coins) are drawn. Example: With the SRSA scheme, Coins (( N , e )) = Z ⇤ N and Is this secure? Alg E N , e ( M ) • Certainly hiding since SE is IND-CPA. Alg E N , e ( M ; K ) C a K e mod N $ • But need not be binding: it may be possible to find C , M 0 , M 1 , K 0 , K 1 K Z ⇤ N C a K e mod N such that D K 0 ( C ) = M 0 and D K 1 ( C ) = M 1 . C s H ( K ) � M return ( C a , C s ) C s H ( K ) � M Exercise: Show such a binding-violating attack when SE is the CBC$ return ( C a , C s ) scheme. Mihir Bellare UCSD 17 Mihir Bellare UCSD 18 Commitment from public key encryption Commitment from public key encryption Let AE = ( K , E , D ) be an IND-CPA-secure asymmetric encryption scheme Let AE = ( K , E , D ) be an IND-CPA-secure asymmetric encryption scheme and let CS = ( P , C , V ) be the commitment scheme where and let CS = ( P , C , V ) be the commitment scheme where Alg P Alg C ( pk , M ) Alg V ( pk , C , M , K ) Alg P Alg C ( pk , M ) Alg V ( pk , C , M , K ) $ $ $ $ if K 62 Coins ( pk ) then return 0 if K 62 Coins ( pk ) then return 0 ( pk , sk ) K Coins ( pk ) ( pk , sk ) K Coins ( pk ) K K π pk C E pk ( M ; K ) if E pk ( M ; K ) = C then return 1 π pk C E pk ( M ; K ) if E pk ( M ; K ) = C then return 1 return ( C , K ) else return 0 return ( C , K ) else return 0 return π return π Is this secure? Is this secure? • Certainly hiding since AE is IND-CPA. Mihir Bellare UCSD 19 Mihir Bellare UCSD 20
Commitment from public key encryption Commitment from hashing Let H be a hash function and CS = ( P , C , V ) the commitment scheme Let AE = ( K , E , D ) be an IND-CPA-secure asymmetric encryption scheme where P returns π = ε and and let CS = ( P , C , V ) be the commitment scheme where Alg C ( π , M ) Alg V ( π , C , M , K ) Alg P Alg C ( pk , M ) Alg V ( pk , C , M , K ) C H ( M ); K M return ( C = H ( M ) and M = K ) $ $ if K 62 Coins ( pk ) then return 0 ( pk , sk ) K Coins ( pk ) K return ( C , K ) π pk C E pk ( M ; K ) if E pk ( M ; K ) = C then return 1 return ( C , K ) else return 0 This is return π Is this secure? • Certainly hiding since AE is IND-CPA. • Binding too since C has only one decryption relative to pk , namely M = D sk ( C ). Mihir Bellare UCSD 21 Mihir Bellare UCSD 22 Commitment from hashing Commitment from hashing Let H be a hash function and CS = ( P , C , V ) the commitment scheme Let H be a hash function and CS = ( P , C , V ) the commitment scheme where P returns π = ε and where P returns π = ε and Alg C ( π , M ) Alg C ( π , M ) Alg V ( π , C , M , K ) Alg V ( π , C , M , K ) C H ( M ); K M C H ( M ); K M return ( C = H ( M ) and M = K ) return ( C = H ( M ) and M = K ) return ( C , K ) return ( C , K ) This is This is • Binding if H is collision-resistant. • Binding if H is collision-resistant. • But not hiding. For example in the Internet Casino M = G 2 { 1 , ..., 100 } so given C = H ( M ) the casino can recover M via for i = 1 , ..., 100 do if H ( i ) = C then return i Mihir Bellare UCSD 23 Mihir Bellare UCSD 24
Commitment from hashing Commitment schemes usage A better scheme is CS = ( P , C , V ) where P returns π = ε and Alg C ( π , M ) Commitment schemes are very broadly and widely used across all kinds of Alg V H ( π , C , M , K ) { 0 , 1 } 128 $ protocol design and in particular to construct zero-knowledge proofs. K return ( H ( K || M ) = C ) C H ( K || M ) return ( C , K ) Mihir Bellare UCSD 25 Mihir Bellare UCSD 26 Flipping a common coin Flipping a common coin • Alice and Bob are getting divorced • Alice and Bob are getting divorced • They want to decide who keeps the Lexus • They want to decide who keeps the Lexus • They aggree to flip a coin, but • They aggree to flip a coin, but • Alice is in NY and Bob is in LA • Alice is in NY and Bob is in LA Protocol CF1: Protocol CF1: Alice Bob Alice Bob c c $ $ c { 0 , 1 } c { 0 , 1 } - - Bob is not too smart but he doesn’t like it... Can you help them out? Mihir Bellare UCSD 27 Mihir Bellare UCSD 28
Recommend
More recommend