
LoRaWAN Architecture IoT Devices need LoRa Chips • Sensors or Actuators • (mostly) battery powered • 9
LoRaWAN Architecture Gateways are connected to multiple • devices only forward packets between • device and server are transparent • 10
LoRaWAN Architecture Network Server Only one per network • connected to all gateways • Knows all devices in the • network Handles traffic from and • to the applications 11
LoRaWAN Architecture 12
LoRaWAN Architecture LoRa IP Network 13
14
The Protocol • Protocol Header • Device Classes • Duty Cycle 15
Security • Encryption on Network Level • Encryption on Application Level 16
Learning Goals The Following Learning Goals are Covered in the Lecture PreLab Lab Understand the LoRaWAN Architecture + Components X X Learn about the LoRaWAN MAC layer protocol X Understand how LoRaWAN is used in the real world X Understand LoRaWAN device classes X X Understand important LoRaWAN mechanisms such as OTA X X Activation and Duty Cycle Setup an own complete LoRaWAN Network X 17
Teaser Practical Part Network Server Gateway 18
Structure PreLab • Understand LoRaWAN Architecture Components in depth • Aspects of LoRaWAN: • Class A/B/C • Activation Methods: OTAA / ABP • Duty Cycle (with calculations) • Introduction to Tools: loraserver.io (Open Source software components) 19
Structure Lab • Setup an own LoRa Network with one / multiple devices using loraserver.io • Send data over the network and see how it is routed to the application • Play around with OTAA and the device classes learned in the PreLab 20
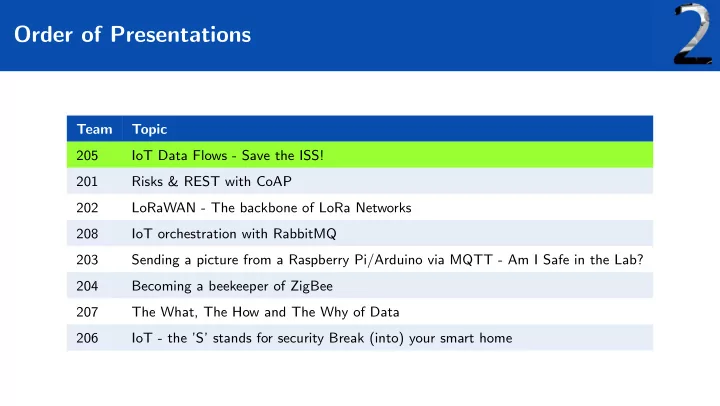
Order of Presentations Team Topic 205 IoT Data Flows - Save the ISS! 201 Risks & REST with CoAP 202 LoRaWAN - The backbone of LoRa Networks 208 IoT orchestration with RabbitMQ 203 Sending a picture from a Raspberry Pi/Arduino via MQTT - Am I Safe in the Lab? 204 Becoming a beekeeper of ZigBee 207 The What, The How and The Why of Data 206 IoT - the ’S’ stands for security Break (into) your smart home
iLab2 - Your own exercise IoT orchestration with RabbitMQ 208 — Victor Oancea — Jurek Olden
Motivation Purpose Middleware is the glue of any IoT system IoT systems are dynamic, devices might fail High performance network applications are fun How to organize the smart city of the future: Get to iLab5 by bus without delays
Reasons for Middleware Hetereogeneous System Message congestion Failures [https://www.noction.com/]
What will you learn? The following learning goals are covered in the Lecture PreLab Lab What is Middleware in an IoT context x Understand why Middleware is needed x x Introduce the publisher-subscriber queueing model and RabbitMQ x x Learn about IoT communication protocols (MQTT, AMQP, STOMP) x x x Understand the RabbitMQ architecture x x Simulate some IoT devices x Configure RabbitMQ and set up an IoT system x Manage an IoT system x
RabbitMQ From rabbitmq.com
MQTT: For a traffic light Lightweight: few message types Minimum overhead: 2 byte header All necessary semantics for publish/subscribe
AMQP: on a bus/autonomous vehicle Not for lightweight devices Supports a lot more metadata More sophisticated semantics
STOMP: for web apps Similar to HTTP Text-based stream protocol Very simple, web socket compatible All necessary semantics for publish/subscribe
Teaser practical part: Munich 2222 a.d.
Structure PreLab Deepen knowledge about the publish/subscribe model Work out differences and characteristics of IoT protocols Gain knowledge about the RabbitMQ architecture
Structure Lab Set up mock devices Set up RabbitMQ Program smart traffic software (Python) Program mock MVG nextgen mobile app (Python) Play around/gather metrics (RabbitMQ web UI)
Order of Presentations Team Topic 205 IoT Data Flows - Save the ISS! 201 Risks & REST with CoAP 202 LoRaWAN - The backbone of LoRa Networks 208 IoT orchestration with RabbitMQ 203 Sending a picture from a Raspberry Pi/Arduino via MQTT - Am I Safe in the Lab? 204 Becoming a beekeeper of ZigBee 207 The What, The How and The Why of Data 206 IoT - the ’S’ stands for security Break (into) your smart home
create your own exercise Mariano Hernandez & Birtan Gültekin Team 203 SENDING A PICTURE FROM A RASPBERRY PI/ARDUINO VIA MQTT - AM I SAFE IN THE LAB? 1
Motivation • IoT sensors and actuators are becoming more and more popular not just in industry sectors but also in smart home commercial sector. In this lab we intend to show some of the most important elements to consider when creating a smart space: – Brief introduction to middleware. – Show and create one of the most popular patterns “publish-subscribe” model using MQTT. 2
Summary/ Learning Goals The Following Learning Goals are Covered in the Lecture PreLab Lab Understand the evolution of IoT middleware X X Understand the middleware architectures X X Understand how MQTT works X X X Understand the MQTT header X Configure a Raspberry Pi, an ESP32, a MQTT broker and a X X Subscriber Send different types of messages X 3
Middleware Origin Term first used in 1968, in the NATO science • committee, during the “Software Crisis”. “This sensitivity of software can be understood • if we liken it to what I will call the inverted pyramid”… “At the bottom are the control programs, then the various service routines. Further up we have what I call middleware.” (Naur, P., & Randell, B., 1969) 4
Middleware • “...we roughly characterize middleware as those services found above the transport (i.e., over TCP/IP) layer set of services but below the application environment (i.e., below application-level APIs).” (RFC 2768) 5
Middleware Key Objectives • Interoperability – Complete interface design – Allow to work with other systems – Allow backwards compatibility • Interchangeability – Using different brands of components 6
Middleware types • RPC (Remote Procedure Call) – Client – server architecture – Distributed functionality • MOM (Message oriented middleware) – Publish/Subscribe – Allows for asynchronous communication 7
8
MQTT • It is created by IBM engineers in 1999 to control a pipeline system • Lightweight publish/subscribe messaging protocol – Fixed length header is 2 bytes • It works on top of TCP/IP protocol 9
How MQTT works? • Broker: receives/sends messages • Client: publisher/subscriber – persistent/transient • Topic: endpoint that clients connect – e.g. lab/sensor/temperature – e.g. subscribe to lab/sensor/# 10
MQTT Cont‘d • Message Types: 14 messages – CONNECT, PUBLISH, SUBSCRIBE, CONNACK, PUBACK, … • Security: 8883 secure port – TLS Encryption – Username & password authentication • QoS: – At most once – At least once – Exactly once 11
Teaser Practical Part This is your playground: 6x Quad Core fast PC with 3-4 usable LAN interfaces per machine. 2x Cisco 881 Router 2x Ethernet switch 2x Work Place with KVM 12
Structure PreLab • Take a deeper look into the interoperability and interchangeability problem in real time systems. – Read about the joint committees that standardized the first protocols, that are still used today. • Present different kind patterns present in IoT environments. • Explain how MQTT works – Explain the MQTT header • Introduce the tools (Mosquitto MQTT, etc.) • Introduce the programming languages that are used in the lab 13
Structure Lab • Setup – Setup a PIR sensor with an ESP32 – Setup a camera with a Raspberry Pi – Setup MQTT broker and clients • Create a publish-subscribe architecture • Send messages between the clients 14
References Naur, P., & Randell, B. (1969). Software Engineering: Report of a conference sponsored by the NATO • Science Committee, Garmisch, Germany, 7-11 Oct. 1968, Brussels, Scientific Affairs Division, NATO. https://www.ietf.org/rfc/rfc2768.txt • MQTT V3.1Protocol Specification. (2010). Retrieved from • http://public.dhe.ibm.com/software/dw/webservices/ws-mqtt/MQTT_V3.1_Protocol_Specific.pdf (2019). Retrieved from • https://www.ibm.com/podcasts/software/websphere/connectivity/piper_diaz_nipper_mq_tt_11182011.p df Interchangeable parts. (2019). Retrieved from https://en.wikipedia.org/wiki/Interchangeable_parts • Interoperability. (2019). Retrieved from https://en.wikipedia.org/wiki/Interoperability • What is middleware? (2019). Retrieved from • https://www.ibm.com/podcasts/software/websphere/connectivity/piper_diaz_nipper_mq_tt_11182011.p df 15
Order of Presentations Team Topic 205 IoT Data Flows - Save the ISS! 201 Risks & REST with CoAP 202 LoRaWAN - The backbone of LoRa Networks 208 IoT orchestration with RabbitMQ 203 Sending a picture from a Raspberry Pi/Arduino via MQTT - Am I Safe in the Lab? 204 Becoming a beekeeper of ZigBee 207 The What, The How and The Why of Data 206 IoT - the ’S’ stands for security Break (into) your smart home
iLab2 Becoming a beekeeper of ZigBee Kaushik, and Cheng-Lun team 204
Motivation Make a wish! What do we need? Communication between a lot of end devices, sensors
Motivation Make a wish! What do we need? Communication between a lot of end devices, sensors Low data rate is sufficient
Motivation Make a wish! What do we need? Communication between a lot of end devices, sensors Low data rate is sufficient Limited battery size on sensors
Motivation Make a wish! What do we need? Communication between a lot of end devices, sensors Low data rate is sufficient Limited battery size on sensors Scalable to large cluster of devices for industrial use
Motivation Yes! ZigBee! Wireless network standard with low-speed, low-power and low-cost 250kb/s, 1mW, 1/10 of the Bluetooth’s price Very popular for smart home gadgets Amazon Echo, Philips Hue, power meters Offers different topology setup enables scalability Star, Tree, Cluster Tree, and Mesh
Lecture Overview ZigBee Alliance Comparing of WiFi, Bluetooth, and ZigBee Application Profiles Protocol layers Device Roles Different topologies Security
ZigBee Alliance The name ZigBee refers to the way honey bees use to communicate. Bees dance in a zig-zag pattern. Is established in 2002 with 100 member companies Announced ZigBee Specification 1.0 on June 13, 2005 Announced ZigBee 3.0 on 2015 (ZigBee PRO 2015) Over 400 member companies (Amazon, Telekom, Samsung,...)
Comparing WiFi, Bluetooth, and ZigBee WiFi 4 (802.11n) Bluetooth 4.0 ZigBee 3.0 Data Rate 72-600 Mb/s 25Mb/s 20-250 kb/s Battery Life Hours 1 week 18 months 868 MHz (Europe) 900- Frequency 2.4 GHz 2.4 GHz 928 MHz (NA) 2.4 GHz (Worldwide) Transmission Distance 100M 10M 10-100M Network Architecture Star Star Star, Tree, Mesh Application Focus Internet Personal gadgets Monitoring & Control
Application Profiles Home Automation Industrial Monitoring Smart Home Hubs + Devices (Amazon Echo, Philips Hue) Predictive Maintenance Security Systems Environment Monitoring HVAC Systems (Nest Asset Tracking Thermostast)
Protocol Layers IEEE 802.15.4 standard defines the PHY and MAC Layers. Zigbee provides Network Layer and Application Layer Framework.
Protocol Layers Application Framework consists of Application Support (APS) Sub-Layer, Zigbee Device Object (ZDO) and Application Objects Service Access Points (SAPs) bind the layers isolating their working from each other.
Device Roles IEEE 802.15.4 standard Full Function Devices (FFD) Reduced Function Devices (RFD) Zigbee standard Zigbee Coordinator Zigbee Router Zigbee End Devices
Different Topologies Star topology One Coordinator, n End Devices End Devices connect to Coordinator End Devices are isolated Mesh topology Peer-to-Peer topology One Coordinator, n Routers, n End Devices End Devices join network through Routers or Coordinators End Devices configured as a FFD or a RFD.
Security Zigbee offers robust security features Frame counter to stop replay attack 128-bit AES-based encryption Key secrecy is the sole foundation of Zigbee Security Architecture Initial key exchange is suseptible to being attacked Key sniffing attack
Lab’s Learning Goals The following learning goals are covered in the Lecture PreLab Lab Understand basics and usages of ZigBee x Comparing ZigBee with other wireless technologies x x Understand ZigBee device roles x x x Understand topology settings x x x Examine security aspects x x x Configure ZigBee devices x Configure a complex topology x Measure performance x
Recommend
More recommend