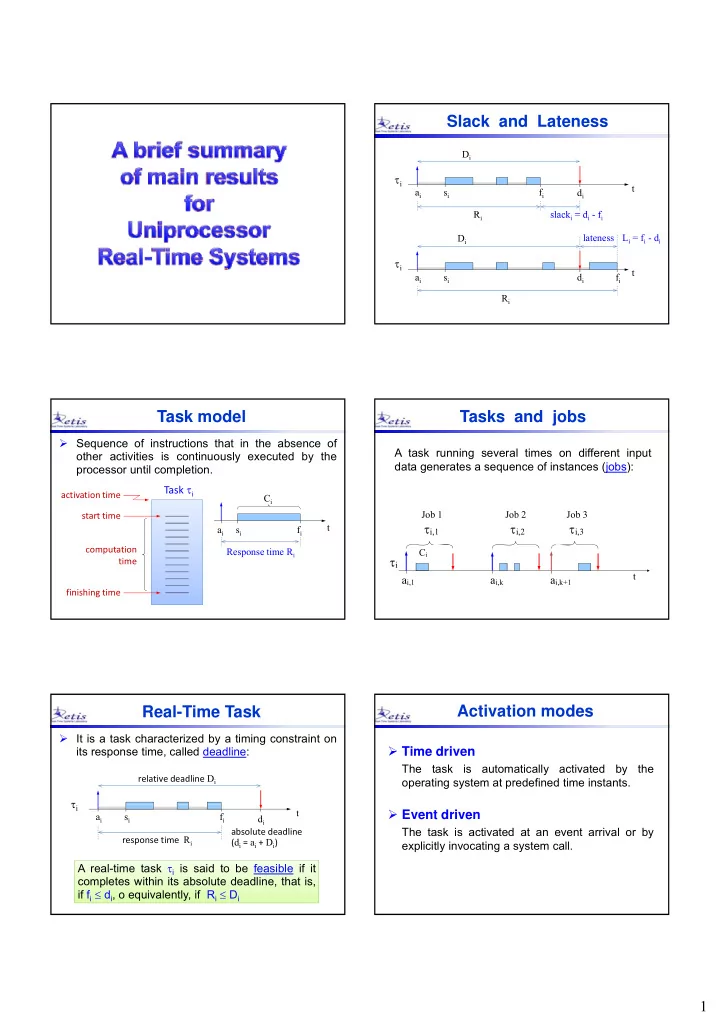

Slack and Lateness D i i t a i s i f i d i R R i slack = d slack i = d i - f i f D i lateness L i = f i - d i i t a i s i d i f i R i Task model Tasks and jobs Sequence of instructions that in the absence of A task running several times on different input other activities is continuously executed by the data generates a sequence of instances (jobs): processor until completion. Task i activation time C i Job 1 Job 2 Job 3 start time i,1 i,2 i,3 t a i s i f i computation Response time R i C i i time t a i,1 a i,k a i,k+1 finishing time Real-Time Task Activation modes It is a task characterized by a timing constraint on Time driven its response time, called deadline: The task is automatically activated by the relative deadline D i operating system at predefined time instants. i t Event driven a i s i f i d i The task is activated at an event arrival or by absolute deadline response time R i ( d i = a i + D i ) explicitly invocating a system call. A real-time task i is said to be feasible if it completes within its absolute deadline, that is, if f i d i , o equivalently, if R i D i 1
Types of tasks Assumptions Aperiodic Implicit deadlines Activated by events. Task activation times are i D i = T i unknown and unbounded. Sporadic Constrained deadlines Activated by events Activated by events. Task activation times are Task activation times are i unknown and bounded: consecutive activations are D i ≤ T i separated by a minimum interarrival time. Arbitrary deadlines Periodic Activated by a timer. Task activation times are Deadlines can be less than, known and bounded: Consecutive jobs are greater than, or equal to periods separated by a constant interval (period). Analysis under fixed priority Aperiodic/Sporadic task interrupt Let = { 1 , …, n } be a set of n periodic tasks. computation time C i Implicit deadlines job ik n C i C i C i … … Utilization-based test i only only U U n 2 / 2 / 1 1 n n 1 1 [Liu & Layland, 1973] i sufficient t a i,1 a i,k a i,k+1 i 1 Aperiodic: (C i , D i ) a i,k+1 > a i,k n Hyperbolic Bound only U 1 2 a i,k+1 a i,k + T i [Bini - Buttazzo 2 , 2001] i (C i , D i , T i ) sufficient Sporadic: i 1 minimum interarrival time 11 Analysis under fixed priority Periodic task input Constrained deadlines C i computation time C i U i = T i Response Time Analysis necessary i R i D i output and [Audsley et al., 1993] timer ( period T i ) utilization factor sufficient sync job ik j T i T i ik Iterative solution: C i i i ( 0 ) R C a i,1 = i a i,k a i,k+1 t i k iterate while k 1 ( s 1 ) task phase i 1 R ( s ) ( s 1 ) R R ( s ) R C i C a i,k = i + (k 1) T i i i i i k T i ( i , C i , T i , D i ) k 1 k d i,k = a i,k + D i 12 2
Analysis under EDF Workload Analysis under FP Constrained deadlines Arbitrary deadlines necessary necessary Processor Demand t D dbf ( t ) t Workload Analysis and i t A i W i ( t ) t and [Baruah et al., 1990] sufficient [Lehoczky et al., 1989] sufficient dbf ( t ) is called demand bound function and denotes the W i ( t ) is called workload in (0, t ] at priority level P i and computation time of tasks with deadlines ≤ t computation time of tasks with deadlines ≤ t denotes the computation time requested in (0 t ] by tasks denotes the computation time requested in (0, t ] by tasks with priority higher than or equal to P i n t + T i D i Σ dbf ( t ) = C k T i i –1 t Σ i = 1 C k W i ( t ) = C i + T k D is the set of points where the test has to be performed k =1 D = { d k | d k L b } L b = max { D max , min (H, L * ) } A i is the set of points where the test has to be performed, equal to the activation times ≤ D i , including D i n ( T D ) U i i i H = lcm(T 1 , … , T n ) L * i 1 1 U 13 16 EDF example Workload Analysis under FP 1 1 task C i T i D i T i - D i U i 1 1 1 25 A task i is feasible iff: U 1 1 4 2 2 1/4 4 2 7 28 2 5 t ≤ D i : W i (t) ≤ t 2 3 6 5 1 1/2 H = 4 3 7 = 84 3 2 14 9 5 1/7 W 2 (t) 18 2 1 5 16 n ( T D ) U 14 12 28 4 2 7 i i i * L i 1 16 12 3 1 U 7 3 10 28 8 6 L b = max ( 9, min (84,16) ) = 16 D max = 9 4 2 0 D = { d k | d k L b } = {2, 5, 6, 9, 10, 11, 14} 0 2 4 6 8 10 12 14 16 18 20 14 17 EDF example Workload Analysis under FP 1 1 1 1 A task i is feasible iff: 2 3 2 7 t ≤ D i : W i (t) ≤ t 3 2 W 2 (t) 9 14 23 18 dbf(t) ( ) 16 16 14 14 12 12 10 10 8 8 6 6 4 4 2 2 0 0 0 2 4 6 8 10 12 14 16 18 20 22 24 0 2 4 6 8 10 12 14 16 18 20 L b 15 18 3
Workload Analysis under FP Workload Analysis under FP 1 1 3 1 A task i is feasible iff: 2 2 t ≤ D i : W i (t) ≤ t 2 3 miss 3 2 W 2 (t) 9 14 23 18 W 3 (t) 3 ( ) 16 16 14 14 12 12 10 10 8 8 6 6 4 4 2 2 0 0 0 2 4 6 8 10 12 14 16 18 20 0 2 4 6 8 10 12 14 16 18 20 A 3 = {4, 6, 8, 9} 19 22 Workload Analysis under FP Workload Analysis under FP Theorem [Bini-Buttazzo, 2002] AND OR 1 1 2 3 A task set is feasible under fixed priorities iff: miss W i ( t ) ≤ t 3 2 t P i–1 (D i ) i = 1...n 9 14 23 W 3 (t) 3 ( ) 16 14 Where P i (t) is defined by: 12 10 8 P 0 (t) = { t } In an unfeasible schedule: 6 t ≤ D i : W i (t) ≤ t t 4 P i (t) = P i-1 U P i-1 (t) T i 2 T i 0 0 2 4 6 8 10 12 14 16 18 20 20 23 Workload Analysis under FP Example 1 Theorem [Lehoczky-Sha-Ding, 1989] 3 6 9 12 15 18 21 2 A task set is feasible under fixed priorities iff: 8 16 24 3 i = 1… n t ≤ D i : W i ( t ) ≤ t 20 1 P (t) = { t } P 0 (t) = { t } Problem Problem t How many points need to be tested? P i (t) = P i-1 T i U P i-1 (t) T i 1 : P 0 (D 1 ) = P 0 (3) = {3} When checking i feasibility, we need to verify W ( t ) ≤ t for D i and for all release times r hk ≤ D i of jobs hk with priority P h ≥ P i , 2 : P 1 (D 2 ) = P 0 (6) U P 0 (8) = {6, 8} that is, for all t in A i : 3 : P 2 (D 3 ) = P 1 (16) U P 1 (20) T i A i = r hk r hk = kT h , h = 1 ... i , k = 1 ... U D i = [ P 0 (15) U P 0 (16)] U [ P 0 (18) U P 0 (20)] T h = {15, 16, 18, 20} 21 24 4
Example Example 1 1 3 6 9 12 15 18 21 2 2 8 16 24 3 3 20 2 P (t) = { t } P 0 (t) = { t } N N N N N N Y Y t P i (t) = P i-1 T i U P i-1 (t) 1 T i 1 : P 0 (D 1 ) = P 0 (3) = {3} 2 2 : P 1 (D 2 ) = P 0 (6) U P 0 (8) = {6, 8} 3 3 : P 2 (D 3 ) = P 1 (16) U P 1 (20) = [ P 0 (15) U P 0 (16)] U [ P 0 (18) U P 0 (20)] N N N Y = {15, 16, 18, 20} 25 28 Example Example 1 1 3 6 9 12 15 18 21 2 2 8 16 24 3 3 20 3 P 0 (t) = { t } P (t) = { t } N N N N N N Y Y t P i (t) = P i-1 T i U P i-1 (t) 1 T i 1 : P 0 (D 1 ) = P 0 (3) = {3} 2 2 : P 1 (D 2 ) = P 0 (6) U P 0 (8) = {6, 8} 3 3 : P 2 (D 3 ) = P 1 (16) U P 1 (20) = [ P 0 (15) U P 0 (16)] U [ P 0 (18) U P 0 (20)] N N N Y = {15, 16, 18, 20} 26 29 Workload Analysis under FP Workload Analysis under FP 1 1 2 2 t 1 t 2 3 W i (t) ≤ t i ( ) t P i–1 (D i ) i = 1...n P 2 (D 3 ) i = 1 C 1 ≤ T 1 P i-1 (D i ) is the minimum set of points t 1 C 2 + C 1 ≤ t 1 for checking the feasibility of i . C 2 + 2C 1 ≤ 2 T 1 T 1 i = 2 t 2 C 2 + 3C 1 ≤ T 2 C 2 + C 1 ≤ t 2 T 1 27 30 5
Workload Analysis under FP C 2 C 2 + 3C 1 ≤ T 2 T 2 FT 1 C 2 + 2C 1 ≤ 2T 1 C 1 T 2 – FT 1 T 2 T 1 F+1 31 Workload Analysis under FP C 2 C 2 + (F+1)C 1 ≤ T 2 T 2 OR FT 1 C 2 + FC 1 ≤ FT 1 C 1 T 2 – FT 1 T 2 T 1 F+1 32 Analysis summary Under EDF (Processor Demand Criterion): t D dbf ( t ) t n t + T i D i Σ dbf ( t ) = C k T T i i = 1 Under Fixed Priorities (Workload Analysis): i 1 ,..., n t A : W i ( t ) t i t i –1 Σ W i ( t ) = C i + C k T k k =1 6
Recommend
More recommend