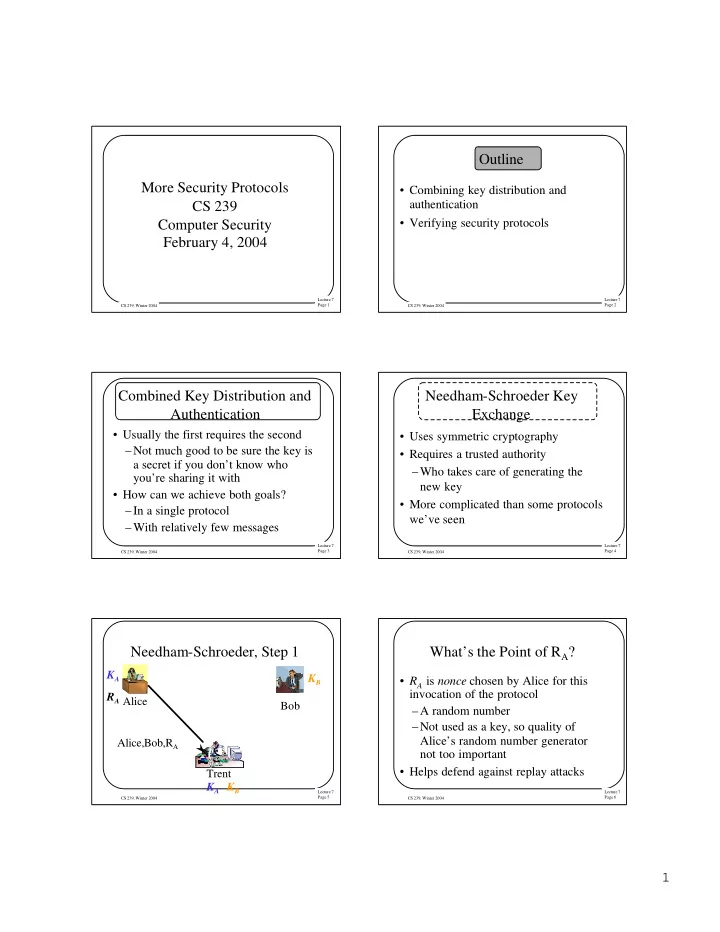

Outline More Security Protocols • Combining key distribution and authentication CS 239 • Verifying security protocols Computer Security February 4, 2004 Lecture 7 Lecture 7 Page 1 Page 2 CS 239, Winter 2004 CS 239, Winter 2004 Combined Key Distribution and Needham-Schroeder Key Authentication Exchange • Usually the first requires the second • Uses symmetric cryptography –Not much good to be sure the key is • Requires a trusted authority a secret if you don’t know who –Who takes care of generating the you’re sharing it with new key • How can we achieve both goals? • More complicated than some protocols –In a single protocol we’ve seen –With relatively few messages Lecture 7 Lecture 7 Page 3 Page 4 CS 239, Winter 2004 CS 239, Winter 2004 Needham-Schroeder, Step 1 What’s the Point of R A ? K A K B • R A is nonce chosen by Alice for this invocation of the protocol R A Alice Bob –A random number –Not used as a key, so quality of Alice’s random number generator Alice,Bob,R A not too important • Helps defend against replay attacks Trent K A K B Lecture 7 Lecture 7 CS 239, Winter 2004 Page 5 CS 239, Winter 2004 Page 6 1
Needham-Schroeder, Step 2 Needham-Schroeder, Step 3 E KB (K S ,Alice) Including R A prevents replay K A K A K B K B Including Bob prevents K S R A attacker from replacing Alice Alice So we’re done, right? K S Bob Bob Bob’s identity Wrong! Including the E KA (R A ,Bob,K S , encrypted message for Bob ensures E KB (K S ,Alice)) that message can’t Trent Trent be replaced K S What’s all this K A K B K A K B stuff for? Lecture 7 Lecture 7 Page 7 Page 8 CS 239, Winter 2004 CS 239, Winter 2004 Needham-Schroeder, Step 4 Needham-Schroeder, Step 5 E KS (R B ) K B E KS (R B -1) K B K A K A K S K S K S K S Alice R B Alice R B Bob Bob R B R B Now we’re done! R B -1 Trent Trent K A K B K A K B Lecture 7 Lecture 7 Page 9 Page 10 CS 239, Winter 2004 CS 239, Winter 2004 What’s All This Extra Stuff For? What’s All This Extra Stuff For? E KB (K S ,Alice) K A K A Alice knows she’s K B K B talking to Bob K S ? s r e Alice Alice b m u Bob Bob Trent said she was n m o d n a Can Mallory Can Mallory Trent said he was r e s o h t t Bob knows u o jump in later? jump in later? b a E KA (R A ,Bob,K S , t a h W he’s talking No, all later No, only Bob to Alice E KB (K S ,Alice)) messages will use could read the Trent K S , which Mallory Trent key package K S K A K B doesn’t know K A K B Trent created Lecture 7 Lecture 7 CS 239, Winter 2004 Page 11 CS 239, Winter 2004 Page 12 2
Mallory Causes Problems Mallory Waits For His Chance E KA (Bob,K S , K B K A • Alice and Bob do something Mallory likes E KB (K S ,Alice)) • Mallory watches the messages they send to Alice do so Mallory Bob • Mallory wants to make them do it again • Can Mallory replay the conversation? – Let’s try it without the random numbers Alice,Bob Trent K A K B Lecture 7 Lecture 7 Page 13 Page 14 CS 239, Winter 2004 CS 239, Winter 2004 What Will Alice Do Now? The Protocol Continues E KB (K S ,Alice) K B K A • The message could only have been created by Trent K S K S Alice Mallory Bob • It properly indicates she wants to talk to Bob Mallory steps With no aside for a bit • It contains a perfectly plausible key random keys, • Alice will probably go ahead with the we’re done protocol Trent K A K B Lecture 7 Lecture 7 Page 15 Page 16 CS 239, Winter 2004 CS 239, Winter 2004 Mallory Steps Back Into the Picture So What’s the Problem E KS (Old message 1) E KS (Old message 2) K B K A • Alice and Bob agree K S is their key K S –They both know the key K S Alice Mallory Bob –Trent definitely created the key for Mallory can It’s using the them replay Alice and current key, so –Nobody else has the key Bob’s old Alice and Bob • But . . . conversation will accept it Trent K A K B Lecture 7 Lecture 7 CS 239, Winter 2004 Page 17 CS 239, Winter 2004 Page 18 3
How Do the Random Numbers Why Bob Also Needs a Random Help? Number K B K A E KB (K S ,Alice) • Alice’s random number assures her that the reply from Trent is fresh K S Alice Mallory Bob • But why does Bob need another Let’s say Alice But Mallory random number? doesn’t want to wants Bob to talk to Bob think Alice wants to talk Trent K A K B Lecture 7 Lecture 7 Page 19 Page 20 CS 239, Winter 2004 CS 239, Winter 2004 So What? So, Everything’s Fine, Right? K B E KS (Old message 1) • Not if any key K S ever gets divulged K S • Once K S is divulged, Mallory can forge Mallory Bob Alice’s response to Bob’s challenge Mallory can now play back an old message from Alice to Bob • And convince Bob that he’s talking to And Bob will have no reason to be Alice when he’s really talking to suspicious Mallory Bob’s random number exchange assured him that Alice really wanted to talk Lecture 7 Lecture 7 Page 21 Page 22 CS 239, Winter 2004 CS 239, Winter 2004 Mallory Cracks an Old Key Timestamps in Security Protocols E KS ( R B ) • One method of handling this kind of K B K S E KB (K S ,Alice) E KS (R B - 1) problem is timestamps R B K S • Proper use of timestamps can limit the Mallory Bob time during which an exposed key is R B - 1 Mallory enlists 10,000 computers belonging dangerous to 10,000 grandmothers to crack K S • But timestamps have their own Unfortunately, Mallory knows K S problems So Mallory can answer Bob’s challenge Lecture 7 Lecture 7 CS 239, Winter 2004 Page 23 CS 239, Winter 2004 Page 24 4
Using Timestamps in the Using Timestamps to Defeat Needham-Schroeder Protocol Mallory K B E KB (K S ,Alice,T X ) • The trusted authority includes K S K S timestamps in his encrypted messages Mallory Bob T X to Alice and Bob T X << T now E KB (K S ,Alice,T X ) • Based on a global clock T now Now Bob checks T X against his clock • When Alice or Bob decrypts, if the timestamp is too old, abort the protocol So Bob, fearing replay, discards K S And Mallory’s attack is foiled Lecture 7 Lecture 7 Page 25 Page 26 CS 239, Winter 2004 CS 239, Winter 2004 Problems With Using The Suppress-Replay Attack Timestamps • Assume two participants in a security • They require a globally synchronized protocol set of clocks – Using timestamps to avoid replay problems –Hard to obtain, often • If the sender’s clock is ahead of the –Attacks on clocks become important receiver’s, attacker can intercept message • They leave a window of vulnerability – And replay later, when receiver’s clock still allows it Lecture 7 Lecture 7 Page 27 Page 28 CS 239, Winter 2004 CS 239, Winter 2004 Neuman-Stubblebine Protocol, Handling Clock Problems Step 1 R A K A Alice, R A K B 1). Rely on clocks that are fairly synchronized and hard to tamper R A Alice Bob –Perhaps GPS signals What does Bob 2). Make all comparisons against the know? same clock Someone –So no two clocks need to be claiming to be synchronized Trent Alice wants to K A K B talk securely Lecture 7 Lecture 7 CS 239, Winter 2004 Page 29 CS 239, Winter 2004 Page 30 5
Neuman-Stubblebine Protocol, Neuman-Stubblebine Protocol, Step 2 Step 3 R A K A K A Bob,R A , K S ,T B K B K B R A Bob,R B , R B R A R B E KA (Bob,R A ,K S ,T B ), Alice Alice Bob Bob T B T B E KB (Alice,R A ,T B ) E KB (Alice,K S ,T B ),R B Alice knows: 1. Bob heard Trent knows Bob her message thinks Alice wants K S to talk to him 2. Trent created Trent Trent But does she a new key Alice,R A ,T B Alice,R A ,T B K A K B K A K B really? Lecture 7 Lecture 7 Page 31 Page 32 CS 239, Winter 2004 CS 239, Winter 2004 Neuman-Stubblebine Protocol, What Has the Protocol K B Step 4 Achieved? K S K A • Alice and Bob share a key E KB (Alice,K S ,T B ), E KS (R B ) R B • They know the key was generated by Alice Bob Trent E KB (Alice,K S ,T B ),R B K S R B • Alice knows this key matches her T B R B guarantees Alice recent request for a key Bob checks knows K S • Bob knows this key matches Alice’s R B and T B T B T B guarantees it’s a recent request and Bob’s agreement Trent fresh session K A K B Lecture 7 Lecture 7 Page 33 Page 34 CS 239, Winter 2004 CS 239, Winter 2004 What Has the Timestamp Done What Else Can You Do With For Bob and Alice? Security Protocols? • Bob knows that the whole agreement is • Secret splitting and secret sharing timely • Fair coin flips and other games • Since the only timestamp originated • Simultaneous contract signing with his clock, no danger of suppress- • Secure elections replay attacks • Zero knowledge proofs off-line • Lots of other neat stuff Lecture 7 Lecture 7 CS 239, Winter 2004 Page 35 CS 239, Winter 2004 Page 36 6
Recommend
More recommend