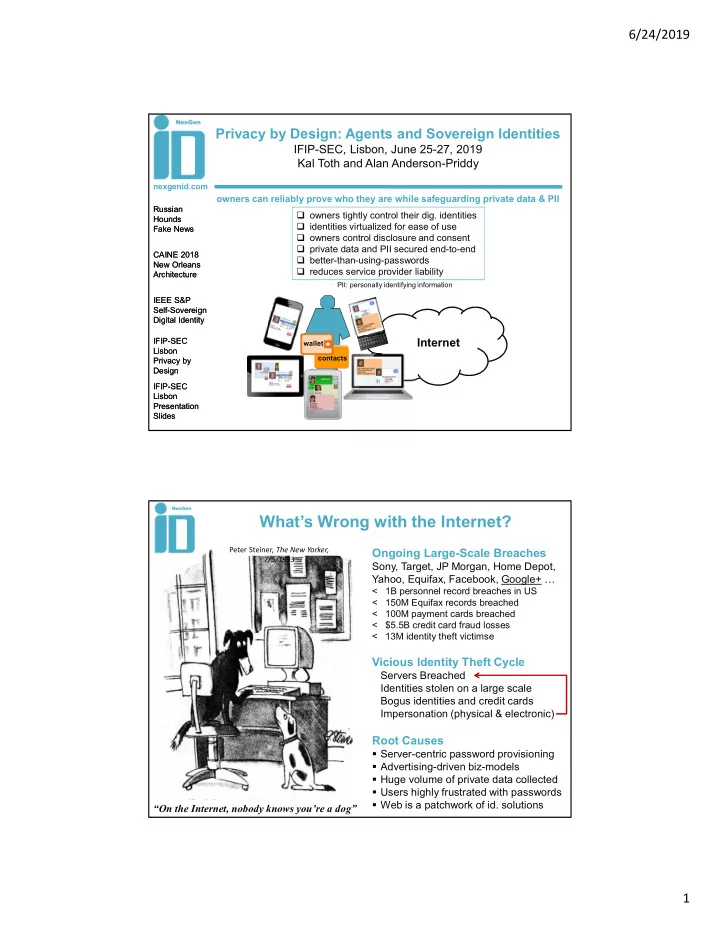

6/24/2019 Privacy by Design: Agents and Sovereign Identities IFIP-SEC, Lisbon, June 25-27, 2019 Kal Toth and Alan Anderson-Priddy nexgenid.com owners can reliably prove who they are while safeguarding private data & PII Russian Russian owners tightly control their dig. identities Hounds Hounds identities virtualized for ease of use Fake News Fake News owners control disclosure and consent private data and PII secured end-to-end CAINE 2018 CAINE 2018 better-than-using-passwords New Orleans New Orleans reduces service provider liability Architecture Architecture PII: personally identifying information IEEE S&P IEEE S&P Self-Sovereign Self-Sovereign Digital Identity Digital Identity IFIP-SEC IFIP-SEC Internet wallet Lisbon Lisbon contacts Privacy by Privacy by Design Design IFIP-SEC IFIP-SEC Lisbon Lisbon Presentation Presentation Slides Slides What’s Wrong with the Internet? Peter Steiner, The New Yorker, Ongoing Large-Scale Breaches 7/5/1993 Sony, Target, JP Morgan, Home Depot, Yahoo, Equifax, Facebook, Google+ … < 1B personnel record breaches in US < 150M Equifax records breached < 100M payment cards breached < $5.5B credit card fraud losses < 13M identity theft victimse Vicious Identity Theft Cycle Servers Breached Identities stolen on a large scale Bogus identities and credit cards Impersonation (physical & electronic) Root Causes Server-centric password provisioning Advertising-driven biz-models Huge volume of private data collected Users highly frustrated with passwords Web is a patchwork of id. solutions “On the Internet, nobody knows you’re a dog” 1
6/24/2019 Diverging Trends … Narrowing the Gap server-centric solutions: - too dependent on web passwords - massive collection of private + PII data - vulnerable to large scale hacks risk Our Goal strength Identity Solution Landscape What User Holds Personal Devices What User Knows Passwords PINs Peer-to-Peer Tools Threema SSB Signal OpenID PGP Telegram WhatsApp Prof. Nets Social Nets SSO Federated Id IAM SecureID SecureKey Centrify FIDO Cogent Yubico Okta NexGenID Nok Nok Enterprise Banking Safran Solutions Systems What User Is Biometrics Identifying pers. W3C Documents ident. VCWG info. What Others Assert What User Asserts Proofing, Attestation Claims, Credentials 2
6/24/2019 Privacy by Design Privacy by Design Privacy System Requirements Design Design Validation A. Users have digital identities used to B. Trusted agents work on behalf of prove who they are; their private, personally owners to safeguard and deploy digital identifying information and transactions are identities, and protect their private and reliably protected and secured. personally identifying information. owner’s identities apps/ browsers consent wallet tokens Trusted Agent owner web services owner’s device contacts - user other owners - admin private data & PII identities of other owners Privacy by Design Privacy System Requirements Design Design Validation A. Users’ have digital identities proving who B. Users’ have devices and trusted agents they are while protecting their private data. safeguarding dig. identities and private data. <a> digital identities intuitive, easy to use User Interface Design View users authenticated by multiple factors <b> protect identities & identifying info. data and crypto key protection <c> selectively disclose identifying info. dig. identities virtualized (ease-of-use) dig. identity proofing, attestation <d> encrypt priv. data locally, remotely Interoperability Design View <e> exchange identities reliably, securely integrate with collab. applications <f> collab. securely using dig. identities secure private data/transactions E2E secure digital identity exchange <g> prevent surveillance and tampering Attestation / Verification Design View <h> detect counterfeits, prev. imperson’n identities attested, digitally sealed <i> proof, attest, seal digital identities proof of existence identity registry proof of possession/custody <j> verify acquired digital identities Delegated Consent Design View <k> request consent to access priv. data tokens granted, expired, revoked <l> grant access to private data stakeholders dig. seal consent tokens events logged to enable accountability <m> hold stakeholders accountable 3
6/24/2019 User Interface Design View owner’s digital identities (sovereign images: attributes, images, public/private keys) digital seals identity engine PII other owners owner collaboration AD service providers authenticator (e.g.) password / PIN authentication finger print data facial recognition hand geometry digital identities of others iris recognition (public copies: attributes, voice recognition images, public keys only) geolocation (GPS) Interoperability Design View device device application services authenticator application authenticator application layer services services wallet wallet authentication authentication data (AD) self-sovereign self-sovereign data (AD) digital identities digital identities identity identity identity layer engine contacts contacts engine identity services identity services event log event log and protocols and protocols transport transport transport layer layer layer services services Internet 4
6/24/2019 Digital Identity Exchange Service owner 2 owner 1 privkeys1 pubkeys1 pubkeys2 privkeys2 id1 id2 use hash of id1 to store use hash of id2 to store owner 1’s public keys Phase 1 owner 2’s public keys use hash of id2 to retrieve Phase 2 use hash of id1 to retrieve owner 2’s public keys owner 1’s public keys Phase 3 symmetrickeys symmetrickeys DH(privkeys1, pubkeys2) DH(privkeys2, pubkeys1) encrypt and transfer owner 1’s digital identity to owner 2 Phase 4 encrypt and transfer owner 2’s digital identity to owner 1 Attestation and Verification identity registry Design View issuers: proof, attest, seal verify digital identity exchange service exchange relying party public copy sovereign present digital identity image verify dig. identities (PoP + PoC) owner secure transactions (encrypt/sign) identity identity engine engine proof, attest, seal dig. identities public keys: key-pairs private keys: 5
6/24/2019 Scenario 1: User Collaboration (P2P) identity registry Exchange Digital Jane Alan Identities (options) identity identity engine engine In-the-Clear Legacy Passwords Exchange Service DH* In-Person Secure Transactions / Messages signed and encrypted end-to-end Elevate Identity Assurances proof, attest, digitally seal Verify Identities (options) proof-of-existence proof-of-possession identity proof-of-custody registry verify digital seals Delegate Consent digitally sealed consent tokens Scenario 2: Online Collaboration identity USB USB USB USB registry Exchange Digital Jane Identities (options) identity identity admin engine engine In-the-Clear Legacy Passwords USB USB Exchange Service DH* In-Person Secure Transactions / Messages signed and encrypted end-to-end Elevate Identity Assurances proof, attest, digitally seal Verify Identities (options) proof-of-existence proof-of-possession identity proof-of-custody registry verify digital seals Delegate Consent digitally sealed consent tokens 6
6/24/2019 Delegated Consent Design View owner’s custodian resources identity engine 2. request wallet owner 3. accept consent 6. access handler event 4. grant log 5. request contacts 1. request relying party Concluding Remarks Our Solution: Shifts Control from Providers to Users enables users to reliably prove who they are and safeguard their private data and personally identifying reduces service provider liability since providers do not need to protect as much private and identifying information significantly reduces password dependency – both users and service providers benefit (win-win) much harder for hackers to compromise personally identifying information, one user device at a time Areas for Further Study adapt / adopt W3C Verifiable Credentials Data Model harden identity engine, formal methods, trust zones, TEE, TPM, Knox identity registry - leverage blockchain / distributed ledger technology strengthen transaction security: adapt Signal’s messaging protocol reference model, open source development 7
6/24/2019 Discussion /Q&A nexgenid.com Resources CAINE 2018, IEEE S&P May/June 2019, IFIP-SEC 2019 (paper + slides) commercialization roadmap, white papers, presentations, prototypes three approved patents, one patent pending 8
Recommend
More recommend