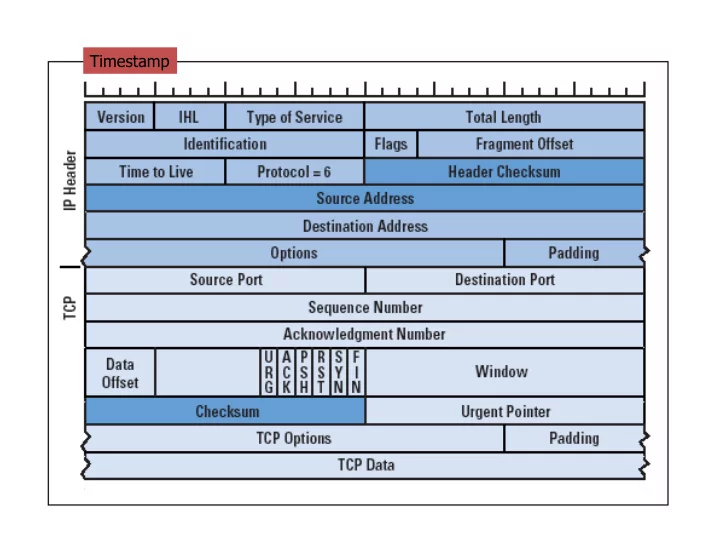

Timestamp
/16 at LBL, sampled 1-in-1K 2nd /16, sampled 1-in-1K
Number of relays 8000 6000 Relays 4000 Bridges 2000 0 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 The Tor Project − https://metrics.torproject.org/
Directly connecting users 6 000 000 4 000 000 2 000 000 0 2012 2013 2014 2015 2016 2017 The Tor Project − https://metrics.torproject.org/
Total relay bandwidth Advertised bandwidth Bandwidth history 200 150 Bandwidth (Gbit/s) 100 50 0 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 The Tor Project − https://metrics.torproject.org/
Time in seconds to complete 50 KiB request Measured times on all sources per day Median 1st to 3rd quartile 30 20 10 0 2010 2011 2012 2013 2014 2015 2016 2017 The Tor Project − https://metrics.torproject.org/
(from 2008)
Number of relays with relay flags assigned 8000 6000 Relay flags Running 4000 Exit 2000 0 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 The Tor Project − https://metrics.torproject.org/
Diffie-Hellman Exchange Well-known: g, p Secret: x, y A ⟶ E ⟶ B: g x mod p B ⟶ E ⟶ A: g y mod p Derived key: g xy
Tor DHE Well-known: g, p Secret: x, y A ⟶ M ⟶ B: E B (g x mod p) B ⟶ M ⟶ A: g y mod p, Hash(K=g xy ) Derived key: g xy
Tor DHE: Mallory Attacks? Well-known: g, p Secret: x, y A ⟶ M: E B (g x mod p) M ⟶ B: E B (g x' mod p) B ⟶ M: g y mod p, Hash(K=g x'y ) M ⟶ A: g y' mod p, Hash(K=g ? ) Derived key: g xy ? g x'y ? g xy' ? g x'y' ?
Tor DHE: Mallory Attacks! Well-known: g, p Secret: x, y; x' = y' = 0 A ⟶ M: E B (g x mod p) M ⟶ B: E B (g x' mod p) = E B (g 0 mod p) = E B (1 mod p) B ⟶ M: g y mod p, Hash(K=g x'y ) = Hash(g 0 ) = Hash(1) M ⟶ A: g y' mod p = 1 mod p, Hash(K=1) Derived key: g xy ? g x'y = g xy’ = g x'y’ = 1
Tor DHE Fixed Well-known: g, p Secret: x, y A ⟶ M ⟶ B: E B (g x mod p) B ⟶ M ⟶ A: g y mod p, Hash(g x || g y || K=g xy ) Derived key: g xy
Recommend
More recommend