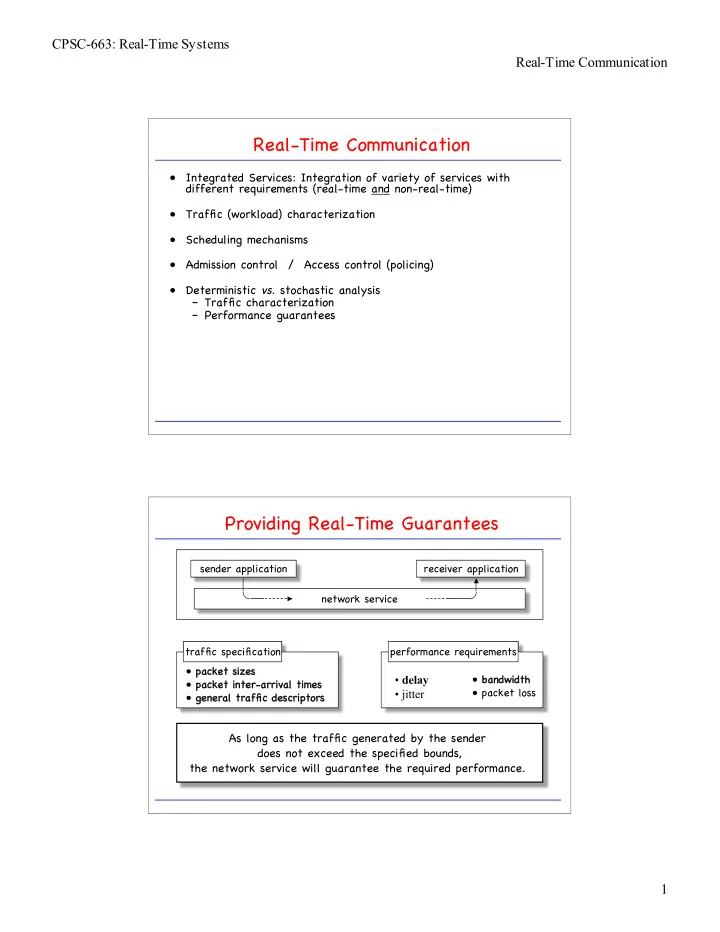

CPSC-663: Real-Time Systems Real-Time Communication Real-Time Communication • Integrated Services: Integration of variety of services with different requirements (real-time and non-real-time) • Traffic (workload) characterization • Scheduling mechanisms • Admission control / Access control (policing) • Deterministic vs. stochastic analysis – Traffic characterization – Performance guarantees Providing Real-Time Guarantees sender application receiver application network service traffic specification performance requirements • packet sizes • bandwidth • delay • packet inter-arrival times • packet loss • jitter • general traffi fic descriptors As long as the traffic generated by the sender does not exceed the specified bounds, the network service will guarantee the required performance. 1
CPSC-663: Real-Time Systems Real-Time Communication Real-Time Guarantees: Mechanisms sender application receiver application network service Enforcement: connection-oriented • policing service • traffic shaping deterministic packet scheduling in switches and routers rigorous (and robust) delay computation real-time-connection establishment Traffic Description: Traffic Bounding Functions a(t) rate [b/sec] t A(t) • Arrival as stochastic process A = {A(t), t ≥ 0} • A and a are poor traffic descriptors: – time dependent • Deterministic traffic arrival descriptors (time-independent) – Maximum Traffi fic Function b(I) ≥ max t>0 {A(t+I) – A(t)} – Maximum Rate Function b(I)/I ≥ max t>0 {A(t+I) – A(t)}/I 2
CPSC-663: Real-Time Systems Real-Time Communication Maximum Traffic Functions b(I)/I Peak Rate 140 b ( I ) / I max ( A ( t I ) A ( t )) / I = + − Max. Data Rate [Mb/sec] t 0 ≥ 120 100 80 60 40 observed max. rate function b(I)/I Average Rate 20 I 0 1 10 100 1,000 10,000 100,000 Time Interval [msec] Traffic Bounding Functions b(I)/I Peak Rate Peak-Rate 140 Max. Data Rate [Mb/sec] 120 100 80 60 Leaky Bucket Pair 40 observed max. rate function b(I)/I Average Rate 20 I 0 1 10 100 1,000 10,000 100,000 Time Interval [msec] 3
CPSC-663: Real-Time Systems Real-Time Communication Maximum Rate vs. Maximum Traffic Functions Maximum Rate Maximum Traffic Representation Representation b(I)/I b(I) I I b(I)/I b(I) I I I 1 I 2 I 1 I 2 Traffic Models Deterministic: 1. Periodic model: (e, p) 2. Deferred Server, Sporadic Server model: (e S , p S ) 3. ( σ , ρ ) model [Cruz] 4. Leaky bucket model [Turner, ...]: ( β , ρ ) 5. (x min , x ave , I, s max ) model [Ferrari & Verma] 6. D-BIND model (Deterministic Bounding Interval Length Dependent) [Knightly & Zhang] 7. Γ -functions [Zhao] Probabilistic: 1. S-BIND model (Stochastic Bounding Interval) [Knightly] 2. Markov-Modulated Poisson Processes 4
CPSC-663: Real-Time Systems Real-Time Communication Traffic Bounding Function b(.) • Let b(.) be a monotonically increasing function. • b(.) is a deterministic traffic constraint function of a connection if during any interval of length I , the number of bits arriving during the interval is no greater than b(I) . • Let A[t1,t2] be the number of packets arriving during interval [t1,t2] . Then, b(.) is a traffic constraint function if • Each model defines inherently a traffic constraint function. • The accuracy of models can be compared by comparing their constraint functions. Cruz’ ( σ , ρ ) Model • If the traffic is fed to a server that works at rate ρ while there is work to be done, the size of the backlog will never be larger than σ . • IOW: The number of jobs/cells released during any interval I does not exceed ρ I+ σ . • Graphical representation: worst case number b(.) of jobs/cells released ρ σ I 5
CPSC-663: Real-Time Systems Real-Time Communication The Leaky Bucket Model • Implementation: ρ – Maintain counter for each traffic stream. – Increment counter at rate ρ , β to maximum of β . – Each time a packet is offered, the counter is checked to be > 0. data – If so, decrement counter and forward packet; otherwise drop packet. worst case number of jobs/cells released ρ β I Concatenating Leaky Buckets • What about limiting the maximum cell rate? β 1 β 2 =1 ρ 1 ρ 2 data worst case number of jobs/cells released ρ 1 β 1 ρ 2 β 2 x 6
CPSC-663: Real-Time Systems Real-Time Communication (x min , x ave , I ave , s max ) model [Ferrari & Verma] • x min : minimum packet interarrival time • x ave : average packet interarrival time • I ave : averaging interval length • s max : maximum packet length t mod I I I b ( x , x , I , s )( I ) = min ave , ave + s min ave ave max max x x I min ave ave worst case number of jobs/cells released 1/ x ave 1/ x min I I ave D-BIND [Knightly & Zhang] • Other models do not accurately describe burstiness. • Rate-interval representation: 1.6 advertisements bounding rate [Mbps] lecture long-term average rate 0.5 1.0 interval length [sec] • Model traffic by multiple rate-interval pairs: (R k , I k ) , where rate R k is the worst-case rate over every interval of length I k . 7
CPSC-663: Real-Time Systems Real-Time Communication D-BIND (2) • Constraint function for D-BIND model with P rate-interval pairs: − R I R I b ( t ) = k k k − 1 k − 1 ( t − I ) + R I , I ≤ t ≤ I k k k k − 1 k I − I k k − 1 b ( 0 ) = 0 = − > b ( t ) b ( t t / I ) for t I P P • Comparison: x min , ... ( σ , ρ ) maximum bits D-BIND interval length Policing for the D-BIND Model • Lemma: If b(t) is piece-wise linear concave, then R k is strictly decreasing with increasing I k . • Lemma: If a piece-wise linear constraint function b(t) with P linear segments is concave, then the source may be fully policed with a cascade of P leaky buckets. concave hull link rate 8
CPSC-663: Real-Time Systems Real-Time Communication Delay Computation: Overview • Delay computation for FIFO server with deterministically constraint input traffic: d max ∑ b ( I ) RI / R = − FIFO i I 0 > i R b 1 (I)+b 2 (I) b 2 (I) b 1 (I) End-to-End Analysis F Y (I) F X (I) X Y • Traffic regulation: reshape traffic to adhere to traffic function. • Alternative: re-characterize by accounting for burstiness added by queueing delays F Y (I) = F X (I+d Y ) – where d Y is delay on Server Y . • Deterministic Case: 9
CPSC-663: Real-Time Systems Real-Time Communication Switch Scheduling • Work-conserving (greedy) vs. non-work-conserving (non-greedy) mechanisms. • Rate-allocating disciplines: Allow packets to be served at higher rates than the guaranteed rate. • Rate-controlled disciplines: Ensures each connection the guaranteed rate, but does not allow packets to be served above guaranteed rate. • Priority-based scheduling: • Weighted Round-Robin scheduling: – fair queuing – WRR – virtual clock – earliest due date (EDD) – rate-controlled static priority (RCSP) Bit-by-Bit Weighted Round-Robin • bit-by-bit round robin • each connection is given a weight • each queue served in FIFO order w i 10
CPSC-663: Real-Time Systems Real-Time Communication Fair Queueing [Demers, Keshav, Shenker] • Emulate Bit-by-Bit Round Robin by prioritizing packets. • Prioritize packets on basis of their finish time f j : – a j : arrival time of j -th packet – e j : length of packet – f j : finish time f max( f , a ) e / BW = + – BW : allocated fraction of link bandwidth j j j j 1 − • Example: 1 1 4 1.5 1 • Complications: – What if connections dynamically change? Virtual Clock Algorithm [L.Zhang] • Emulate time-division multiplex (TDM) mechanism • However: – TDM: when some connections idle, the slots assigned are idle – VC: idle slots are deleted from TDM frames • auxiliary virtual clock ( auxVC j ): finish time of j -th packet. • virtual tick ( Vtick j ) :time to complete transmission of ready j -th packet. Vtick j = e j /BW • Replace f j by Vtick j : VC becomes identical to WFQ algorithm! • Will analyze delay analysis later. 11
CPSC-663: Real-Time Systems Real-Time Communication Rate-Controlled Static Priority (RCSP) [Zhang&Ferrari] priority queues RCSP (2) rate controller priority queues 12
Recommend
More recommend