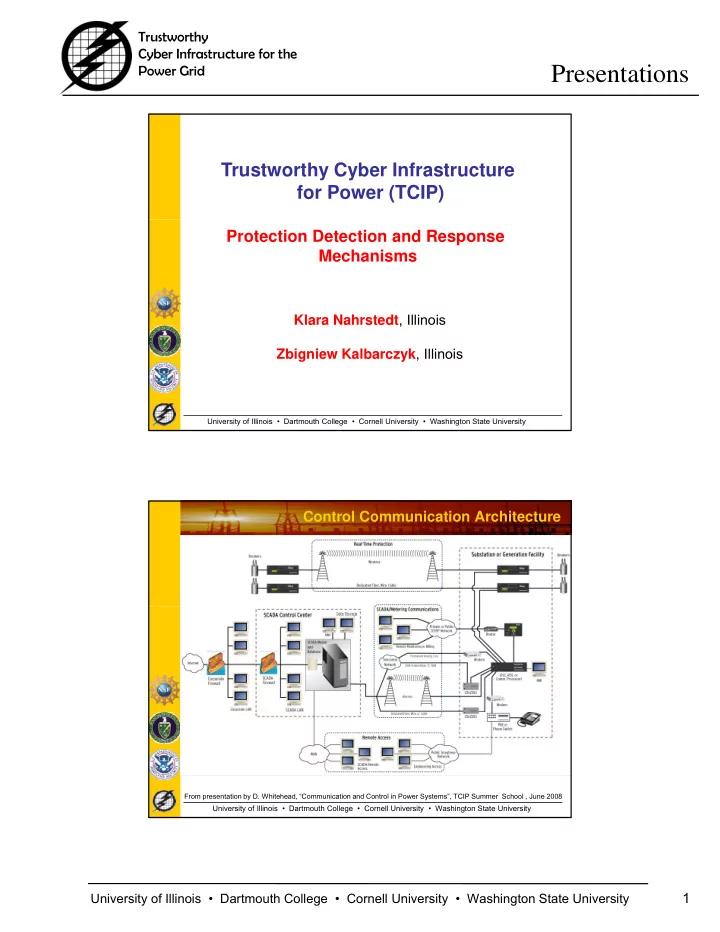

Trustworthy Cyber Infrastructure for the Power Grid Presentations Trustworthy Cyber Infrastructure for Power (TCIP) Protection Detection and Response Mechanisms Klara Nahrstedt , Illinois , Zbigniew Kalbarczyk , Illinois University of Illinois • Dartmouth College • Cornell University • Washington State University Control Communication Architecture From presentation by D. Whitehead, “Communication and Control in Power Systems”, TCIP Summer School , June 2008 University of Illinois • Dartmouth College • Cornell University • Washington State University 1 University of Illinois • Dartmouth College • Cornell University • Washington State University
Trustworthy Cyber Infrastructure for the Power Grid Presentations Presentation Methodology Power-Grid supporting Digital Networks and Distributed Systems (Presenter: Klara Nahrstedt) (Presenter: Klara Nahrstedt) Power-Grid supporting Computing Base (Presenter: Zbigniew Kalbarczyk) University of Illinois • Dartmouth College • Cornell University • Washington State University Characteristics and Goals for Control Networks and Devices • Characteristics – Mission-oriented – Stable • Goals Real-time availability to sustain the critical functions of the 1. power grid Integrity to trustworthy deliver correct commands and data 2. Confidentiality to safeguard trade secrets 3. • Trends – Update /replace existing devices, networks, software with low cost commodity infrastructure such as Linux, Windows, Intel-based processors, Mesh Networks, WiFi, Zigbee, Internet protocols (TCP/IP), … University of Illinois • Dartmouth College • Cornell University • Washington State University 2 University of Illinois • Dartmouth College • Cornell University • Washington State University
Trustworthy Cyber Infrastructure for the Power Grid Presentations Power-Grid supporting Digital Network: State of the Art • Network State of the Art IEC 61850 – No routable traffic in many cases between substations and control centers – Serial lines between sensors and RTUs in substations and RTUs in substations – One way digital communication from the substation to the control center, – Hierarchical organization between substations and control centers – No wireless or very little wireless network deployment • Real-Time State of the Art – Separate networks for real-time and management traffic • Network Security State of the Art – Security by obscurity or perimeter security University of Illinois • Dartmouth College • Cornell University • Washington State University The Problem Space • Real-Time Availability is not addressed adequately under new trends – Real-Time Problems: Service-oriented model instead of mission- oriented model, Low stability since software changes constantly (new patches) , Difficulties in maintaining configurations in real-time conditions conditions • Real-Time Management Problem • Cyber-Security is not addressed adequately – Security problems: Attacks on Integrity by polluting data, losing data • Key Management Problem • Authorization, Authentication, Access Control Problem • Attack Management Problem – Security problems: Attacks on Confidentiality by attacking Ethernet – Security problems: Attacks on Confidentiality by attacking Ethernet switches, IP traffic routers; end devices to get to data • Key Management Problem • Authorization, Authentication, Access Control Problem • Attack Management Problem University of Illinois • Dartmouth College • Cornell University • Washington State University 3 University of Illinois • Dartmouth College • Cornell University • Washington State University
Trustworthy Cyber Infrastructure for the Power Grid Presentations Approach: End-to-End Real-Time Trust Provisioning via Protection, Detection, Response Coordinator ISO Level Control Center Backup Ethernet / IP-Network (Secure, Real-time, Level Monitored) Ethernet / IP-Network (Secure, Real-time, Monitored) “Smart” Data Gateway/Hub Network Private IP-Based Level Network (Secure, Real-time, Private IP-Based Private IP-Based Monitored) Network Network (Secure, Real-time, (Secure, Real-time, Monitored) Monitored) Metering and Load Control “Smart” Gateway/Hub IED IED IED DFR Local HMI Substation Level Ethernet / IP-Network (Secure, Real-time, Monitored) IED IED IED IED Sensor/Actuator Level University of Illinois • Dartmouth College • Cornell University • Washington State University Approach Control Center • Protect, Detect, Respond Functions Functions Protection Detection Response Functions – Protect: Prevent (Plan, Admit, Reserve) violations, Enforce (Schedule, Encrypt, Sign) real- Data ti time availability, integrity and il bilit i t it d confidentiality Private IP-Based Network (Secure, Real-time, – Detect: Monitor, Assess and Monitored) Functions Functions Alert violations, threats, Protection Detection Response Functions vulnerabilities, misbehaviors, errors IEDIEDIED DFR Local HMI – Respond: Act against abnormal events , Issue reconfigurations, IED IED IED IED Functions Functions Protection Detection Response Bridge new and legacy entities Functions along the end-to-end path, Substation Contain misbehaved entities University of Illinois • Dartmouth College • Cornell University • Washington State University 4 University of Illinois • Dartmouth College • Cornell University • Washington State University
Trustworthy Cyber Infrastructure for the Power Grid Presentations Protect, Detect, Respond Framework Protect: Enforce & Prevent Detect Respond Power Grid Protocols: SCADA Data IEC 61850, DNP3, ICCP, MODBUS Detect Violation of Key Encryption/ Keys Setup Re-keying Keys Man. Decryption Protocols Confidentiality Password Change Per-Packet Authentication, AAA Detection of Access Privileges Role Authorization, Access Control AAA Violations Control Change Trust Negotiation Q alit Quality of of Real Real-time Delivery QoS Monitoring Service QoS Time Scheduling Detection of QoS Admission, Adaptation Degradation Man. Reservation Vulnerabilities/Attack Assessment, Monitoring, Attack Detection , Containment and Recovery Man. University of Illinois • Dartmouth College • Cornell University • Washington State University Current Research Thrusts (1): Key Management • Problem: – Allocate and distribute keys to heterogeneous devices in Power Grid over diverse networks Control Center/SCADA – Allow cryptographic functions for confidentiality and integrity y g y DNSSEC DNSSEC – Recover from attacks when keys are compromised • Idea: DomainCert – Simplified key management – Resource-efficient combinatorial public key management approach Gateway Gateway DNSSEC • Results so far: Cache SMOCK – Domain Cert: simplified PKI / DNSSEC certificate management – SMOCK: resource-efficient group key scheme for legacy devices Legacy New IED IED Devices Devices • In progress : – Integrated hierarchical key management with diverse key schemes University of Illinois • Dartmouth College • Cornell University • Washington State University 5 University of Illinois • Dartmouth College • Cornell University • Washington State University
Trustworthy Cyber Infrastructure for the Power Grid Presentations Current Research Thrusts (2): AAA Management • Problem: – Achieve confidentiality, integrity and availability in dynamic and evolvable fashion – Allow for robust, flexible and high performance authorization across organizations • Idea: – Data Plane Security Architecture – Authorization via trust negotiation • Results so far: Alice at Control Center 1 Control Center 2 – GridStat with transparent inter-changable security modules assigned on a per status variable granularity – Trustbuilder2 framework – Integrated Gridstat and TrustBuilder2 Access? – ABUSE: enabling human users to draw Employee at NERC- correct trust conclusions about “secure” email certified control center? (Validated against Aug 2003 transcripts) Audit policy? P • Audit policy In progress: Employee ID – Exploration of end-to-end AAA/Security Architectures Access granted Service University of Illinois • Dartmouth College • Cornell University • Washington State University (2) Trust Negotiation State Consistency Example Scenario The scenario: Alice can be either a power operator or an internal auditor in Control Center 1, though these roles are mutually exclusive. As an internal auditor, she can also act as an information classifier. Alice wishes to access a remote service available to power operators who are information classifiers, and forces the use of an inconsistent system state to accomplish this. Alice at Control Center 1 Alice at Control Center 1 Control Center 2 Control Center 2 X Inconsistent Alice requests access to the status database State! Certified power operator in NERC-certified control center? Information classifier? Power operator credential. Audit Policy? √ P Certified audit policy. √ √ Information classifier certificate. Access granted! Service University of Illinois • Dartmouth College • Cornell University • Washington State University 6 University of Illinois • Dartmouth College • Cornell University • Washington State University
Recommend
More recommend