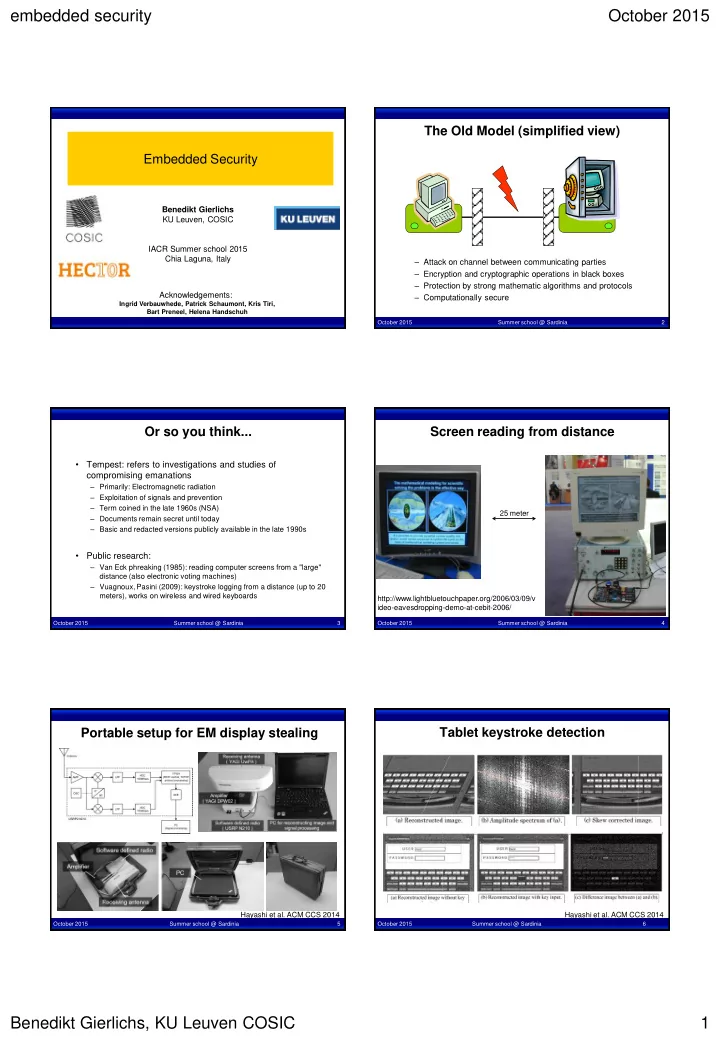

embedded security October 2015 The Old Model (simplified view) Embedded Security Benedikt Gierlichs KU Leuven, COSIC IACR Summer school 2015 Chia Laguna, Italy – Attack on channel between communicating parties – Encryption and cryptographic operations in black boxes – Protection by strong mathematic algorithms and protocols Acknowledgements: – Computationally secure Ingrid Verbauwhede, Patrick Schaumont, Kris Tiri, Bart Preneel, Helena Handschuh October 2015 Summer school @ Sardinia 2 Or so you think... Screen reading from distance • Tempest: refers to investigations and studies of compromising emanations – Primarily: Electromagnetic radiation – Exploitation of signals and prevention – Term coined in the late 1960s (NSA) 25 meter – Documents remain secret until today – Basic and redacted versions publicly available in the late 1990s • Public research: – Van Eck phreaking (1985): reading computer screens from a "large" distance (also electronic voting machines) – Vuagnoux, Pasini (2009): keystroke logging from a distance (up to 20 meters), works on wireless and wired keyboards http://www.lightbluetouchpaper.org/2006/03/09/v ideo-eavesdropping-demo-at-cebit-2006/ October 2015 Summer school @ Sardinia 3 October 2015 Summer school @ Sardinia 4 Portable setup for EM display stealing Tablet keystroke detection Hayashi et al. ACM CCS 2014 Hayashi et al. ACM CCS 2014 October 2015 Summer school @ Sardinia 5 October 2015 Summer school @ Sardinia 6 Benedikt Gierlichs, KU Leuven COSIC 1
embedded security October 2015 Embedded Cryptographic Devices How is Embedded Security affected? Firewall • • A cryptographic device is an electronic device that New Model (also simplified view): implements a cryptographic algorithm and stores a – Attack on channel and endpoints cryptographic key. It is capable of performing cryptographic – Encryption and cryptographic operations in gray boxes – Protection by strong mathematic algorithms and protocols operations using that key. – Protection by secure implementation • Embedded: it is exposed to adversaries in a hostile • Need secure implementations not only algorithms environment; full physical access, no time constraints – Note: the adversary might be a legitimate user! October 2015 Summer school @ Sardinia 7 October 2015 Summer school @ Sardinia 8 Internet of Things Cyber physical systems “A system of collaborating computational elements controlling physical entities” [1] “Networked embedded systems interacting with the environment” [2] [1] wikipedia [2] Ed Lee, after H. Gill NSF Network: controller area network (CAN) [Source photograph: J. Rabaey: A Brand New Wireless Day] October 2015 Summer school @ Sardinia 9 October 2015 Summer school @ Sardinia 10 Medical devices, typical scenario Interacting with the environment • Small embedded devices communicate over wireless Embedded cryptography? link for sensing and actuation • Goal: low energy (battery powered, temperature) • Security goal: attack resistant IMEC: NERF - brain stimulant Deep Brain stimulation [Sources: J. Rabaey, National Institutes of Health, Neurology journal] IMEC: Human++ project October 2015 Summer school @ Sardinia 11 October 2015 Summer school @ Sardinia 12 Benedikt Gierlichs, KU Leuven COSIC 2
embedded security October 2015 Always keep in mind Your system is as secure as its weakest link Your system is as secure as its weakest link Unknown source: seen on schneier.com October 2015 Summer school @ Sardinia 13 October 2015 Summer school @ Sardinia 14 Your system is as secure as its weakest link Your system is as secure as its weakest link • The adversary will go for the weakest entry point – Disable or go around security mechanisms – Guess / spy on passwords – Bribe the security guard • If you use good crypto, he will try to go around it – System designer: thinks of the "right" way to use the system – Adversary: does not play by the rules – Designer has to think like the adversary, anticipate attacks, protect against them – There is no way to protect against all attacks • Do you know all attacks? Source: P. Kocher October 2015 Summer school @ Sardinia 15 October 2015 Summer school @ Sardinia 16 Security for Embedded Systems Security for Embedded Systems “Researcher has a new attack for embedded devices • SecuStick: Vulnerability lies in ARM and XScale microprocessors” Computerworld – security – On plug-in: Windows program pops up and asks for password April 4, 2007 – Self-destructs if wrong password entered n-many times How: Use JTAG interface “Secustick gives false sense of security” April 12, 2007 http://tweakers.net/reviews/683 – Attempt counter stored in flash memory chip Security completely broken – Write-enable pin connected to GND: infinite number of attempts to guess the password – Password is checked in software routine on PC: changing return value from "0" to "1" gives full access April 12, 2007: http://tweakers.net/reviews/683 October 2015 Summer school @ Sardinia 17 October 2015 Summer school @ Sardinia 18 Benedikt Gierlichs, KU Leuven COSIC 3
embedded security October 2015 Physical security of Classification of Physical Attacks embedded cryptographic devices • Non-Invasive Active versus passive • Let us assume that the system is well designed – Active: Perturbate and conclude – Adversary cannot go around / disable security features – Passive: Observe and infer – Good cryptography is used • Invasive versus non-invasive active passive – Invasive: open package and contact chip • Embedded context, physical access – Semi-invasive: open package, no contact – Non-invasive: no modification • Invasive Side channel: passive and non-invasive – Adversary can "look" at the device under attack – • Measure physical quantities Very difficult to detect – Often cheap to set-up – Often: need lots of measurements automating – Adversary can manipulate the device under attack • • Expose it to physical stress and "see" how it behaves Circuit modification: active and invasive – Expensive to detect invasion (chip might be without power) – Very expensive equipment and expertise required October 2015 Summer school @ Sardinia 19 October 2015 Summer school @ Sardinia 20 Side-Channel Leakage Some Side-Channels (not exhaustive) • Physical attacks ≠ Cryptanalysis • Timing execution time – Overall or "local" execution time (gray box, physics) (black box, maths) time • Does not tackle the algorithm's math. security • Power, Electromagnetic radiation – Predominant: CMOS technology Input Output – Consumes power when it does something, transistors switch – Electric current induces and EM field Leakage • More exotic but shown to be practical – Light, Sound, Temperature • Observe physical quantities in the device's vincinity and use additional information during cryptanalysis October 2015 Summer school @ Sardinia 21 October 2015 Summer school @ Sardinia 22 Examples: measurement setups Side-Channel leakage • • Smart cards Side-channel leakage – Is not intended • FPGA, ASIC – Information leakage was not considered at design time • Phone, tablet – Leaked information is not supposed to be known • Set-top boxes – Can enable new kind of attack • Etc. • Often, optimizations enable leakage • source: langer-emv.de Device under attack is operated in normal conditions – Adversary is passive an solely observes October 2015 Summer school @ Sardinia 23 October 2015 Summer school @ Sardinia 24 Benedikt Gierlichs, KU Leuven COSIC 4
Recommend
More recommend