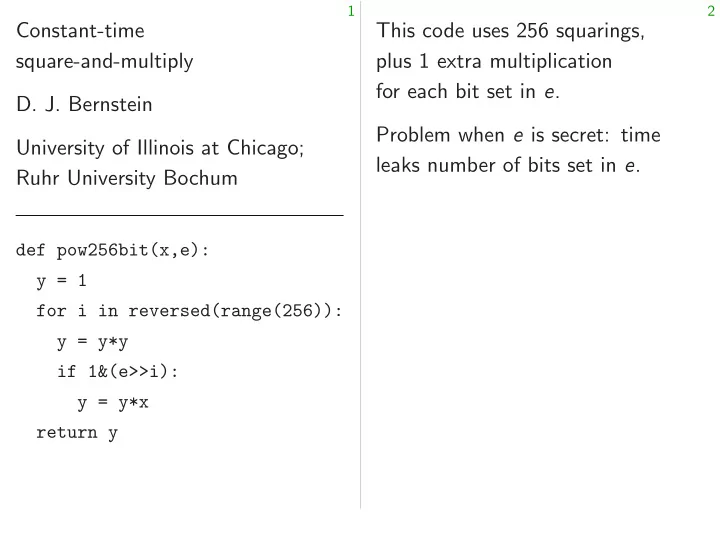

1 2 Constant-time This code uses 256 squarings, square-and-multiply plus 1 extra multiplication for each bit set in e . D. J. Bernstein Problem when e is secret: time University of Illinois at Chicago; leaks number of bits set in e . Ruhr University Bochum def pow256bit(x,e): y = 1 for i in reversed(range(256)): y = y*y if 1&(e>>i): y = y*x return y
1 2 Constant-time This code uses 256 squarings, square-and-multiply plus 1 extra multiplication for each bit set in e . D. J. Bernstein Problem when e is secret: time University of Illinois at Chicago; leaks number of bits set in e . Ruhr University Bochum “I’ll choose secret 256-bit e with exactly 128 bits set. There are def pow256bit(x,e): enough of these e , and then y = 1 there are no more leaks.” for i in reversed(range(256)): y = y*y if 1&(e>>i): y = y*x return y
1 2 Constant-time This code uses 256 squarings, square-and-multiply plus 1 extra multiplication for each bit set in e . D. J. Bernstein Problem when e is secret: time University of Illinois at Chicago; leaks number of bits set in e . Ruhr University Bochum “I’ll choose secret 256-bit e with exactly 128 bits set. There are def pow256bit(x,e): enough of these e , and then y = 1 there are no more leaks.” for i in reversed(range(256)): y = y*y — Time still depends on e , if 1&(e>>i): even if each multiplication y = y*x takes time independent of inputs. return y
1 2 Constant-time This code uses 256 squarings, Hardware re-and-multiply plus 1 extra multiplication is inherently for each bit set in e . Bernstein CPU designers Problem when e is secret: time University of Illinois at Chicago; leaks number of bits set in e . University Bochum “I’ll choose secret 256-bit e with exactly 128 bits set. There are pow256bit(x,e): enough of these e , and then there are no more leaks.” in reversed(range(256)): y*y — Time still depends on e , 1&(e>>i): even if each multiplication = y*x takes time independent of inputs. return y
1 2 This code uses 256 squarings, Hardware reality: Accessing re-and-multiply plus 1 extra multiplication is inherently expensive for each bit set in e . CPU designers try Problem when e is secret: time Illinois at Chicago; leaks number of bits set in e . Bochum “I’ll choose secret 256-bit e with exactly 128 bits set. There are pow256bit(x,e): enough of these e , and then there are no more leaks.” reversed(range(256)): — Time still depends on e , even if each multiplication takes time independent of inputs.
1 2 This code uses 256 squarings, Hardware reality: Accessing plus 1 extra multiplication is inherently expensive. for each bit set in e . CPU designers try to reduce Problem when e is secret: time Chicago; leaks number of bits set in e . “I’ll choose secret 256-bit e with exactly 128 bits set. There are enough of these e , and then there are no more leaks.” reversed(range(256)): — Time still depends on e , even if each multiplication takes time independent of inputs.
2 3 This code uses 256 squarings, Hardware reality: Accessing RAM plus 1 extra multiplication is inherently expensive. for each bit set in e . CPU designers try to reduce cost. Problem when e is secret: time leaks number of bits set in e . “I’ll choose secret 256-bit e with exactly 128 bits set. There are enough of these e , and then there are no more leaks.” — Time still depends on e , even if each multiplication takes time independent of inputs.
2 3 This code uses 256 squarings, Hardware reality: Accessing RAM plus 1 extra multiplication is inherently expensive. for each bit set in e . CPU designers try to reduce cost. Problem when e is secret: time Example: “L1 cache” typically leaks number of bits set in e . has 32KB of recently used data. “I’ll choose secret 256-bit e with This cache inspects RAM exactly 128 bits set. There are addresses, performs various enough of these e , and then computations on addresses there are no more leaks.” to try to save time. — Time still depends on e , even if each multiplication takes time independent of inputs.
2 3 This code uses 256 squarings, Hardware reality: Accessing RAM plus 1 extra multiplication is inherently expensive. for each bit set in e . CPU designers try to reduce cost. Problem when e is secret: time Example: “L1 cache” typically leaks number of bits set in e . has 32KB of recently used data. “I’ll choose secret 256-bit e with This cache inspects RAM exactly 128 bits set. There are addresses, performs various enough of these e , and then computations on addresses there are no more leaks.” to try to save time. — Time still depends on e , : : : so time is a function of RAM even if each multiplication addresses. Avoid all data flow takes time independent of inputs. from secrets to RAM addresses.
2 3 code uses 256 squarings, Hardware reality: Accessing RAM Example: extra multiplication is inherently expensive. from secrets h bit set in e . CPU designers try to reduce cost. Often describ Problem when e is secret: time for softw Example: “L1 cache” typically number of bits set in e . the same has 32KB of recently used data. choose secret 256-bit e with This cache inspects RAM exactly 128 bits set. There are addresses, performs various enough of these e , and then computations on addresses are no more leaks.” to try to save time. Time still depends on e , : : : so time is a function of RAM if each multiplication addresses. Avoid all data flow time independent of inputs. from secrets to RAM addresses.
2 3 256 squarings, Hardware reality: Accessing RAM Example: Avoid all multiplication is inherently expensive. from secrets to branch in e . CPU designers try to reduce cost. Often described as is secret: time for software, but comes Example: “L1 cache” typically bits set in e . the same hardware has 32KB of recently used data. cret 256-bit e with This cache inspects RAM set. There are addresses, performs various e , and then computations on addresses re leaks.” to try to save time. depends on e , : : : so time is a function of RAM multiplication addresses. Avoid all data flow endent of inputs. from secrets to RAM addresses.
2 3 rings, Hardware reality: Accessing RAM Example: Avoid all data flow is inherently expensive. from secrets to branch condi CPU designers try to reduce cost. Often described as a separate time for software, but comes from Example: “L1 cache” typically e . the same hardware reality. has 32KB of recently used data. e with This cache inspects RAM There are addresses, performs various then computations on addresses to try to save time. , : : : so time is a function of RAM addresses. Avoid all data flow inputs. from secrets to RAM addresses.
3 4 Hardware reality: Accessing RAM Example: Avoid all data flow is inherently expensive. from secrets to branch conditions. CPU designers try to reduce cost. Often described as a separate rule for software, but comes from Example: “L1 cache” typically the same hardware reality. has 32KB of recently used data. This cache inspects RAM addresses, performs various computations on addresses to try to save time. : : : so time is a function of RAM addresses. Avoid all data flow from secrets to RAM addresses.
3 4 Hardware reality: Accessing RAM Example: Avoid all data flow is inherently expensive. from secrets to branch conditions. CPU designers try to reduce cost. Often described as a separate rule for software, but comes from Example: “L1 cache” typically the same hardware reality. has 32KB of recently used data. How CPU runs a program This cache inspects RAM (example of “code = data”): addresses, performs various computations on addresses while True: to try to save time. insn = RAM[state.ip] state = execute(state,insn) : : : so time is a function of RAM addresses. Avoid all data flow ip (“instruction pointer” or from secrets to RAM addresses. “program counter”): address in RAM of next instruction.
3 4 are reality: Accessing RAM Example: Avoid all data flow Standard inherently expensive. from secrets to branch conditions. to follow Square and designers try to reduce cost. Often described as a separate rule for software, but comes from def pow256bit(x,e): Example: “L1 cache” typically the same hardware reality. y = 1 32KB of recently used data. for i How CPU runs a program cache inspects RAM y = (example of “code = data”): addresses, performs various yx = computations on addresses while True: bit to save time. insn = RAM[state.ip] y = state = execute(state,insn) return time is a function of RAM addresses. Avoid all data flow ip (“instruction pointer” or If bit is secrets to RAM addresses. “program counter”): address an unused in RAM of next instruction.
Recommend
More recommend