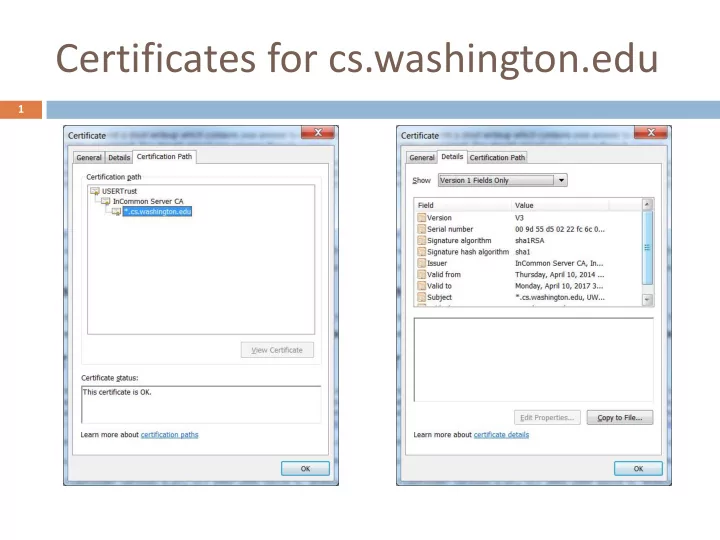

Certificates for cs.washington.edu 1
Certificates for GMail Important fields:
Testing SSL Configuration (1) 3 Client completed verification of received certificate chain
Testing SSL Configuration (2) 4 Received certificate chain (two certificates) Size of received certificate chain
Testing SSL Configuration (3) 5 Issued session identifier (Ses ession-ID ID) for stateful TLS resume. Example from “High Performance Browser Networking”
Where to Use SSL? 6 Login page? Where else? What about JavaScript includes? Image includes? Why not encrypt everything?
Where to Use SSL? 7 Some browsers may not support SSL SSL may decrease performance somewhat. If users are downloading large, public files, there may be a system burden to encrypt these each time. You will probably want the home page accessible via HTTP, so that users don't have to remember to type https to get to it.
Firesheep (2010) 8 Assume you are using the facebook.com site over an unsecured Wi-Fi network such as in shopping malls and coffee shops. When you visit the Facebook site, you are required to enter the username and password. When you send that request and on successful login, Facebook sends you an auth then enti tication tok oken in the clear which is then sent every time you browse Facebook pages
Firesheep 9
Facebook Switches to HTTPS in 2012 10
Lab-2 11 Part 1 Part 2 C programming is tricky Black-box fuzzing is far Bounds are far from from easy obvious even when Very little insight into reasoning about a short function program behavior Makes you appreciate Makes you appreciate programming in Java or having access to C# where array accesses are checked at runtime! source code!
Lab-2: Survey 12 Part 1 Part 2 I will never try to black- I will never program in C A. A. box fuzz a server again for for as long as I live as long as I live Working on this lab makes B. I had an aha moment me appreciate how hard B. about a timing channel static analysis tools have when solving this lab to work I feel that having hiding I will allocate truly gigantic C. C. the source code makes buffers so they can never programs more secure ever overflow
HTTPS in the Browser
The User is Responsible for Visually Validating SSL 14 Often, that’s the user is the weakest lin link Extended Validation (EVSSL) certificate Issued according to a specific set of identity verification criteria. These criteria require extensive verification of the requesting entity's identity by the CA before a certificate is issued
Internet Explorer 9: SSL 15
Internet Explorer 9: EVSSL 16
Firefox 4: SSL 17
Firefox 4: EVSSL 18
Chrome 11: SSL 19
Chrome 11: EVSSL 20
A General UI Attack: Picture-in-Picture 21
CSE484/CSE584 MALWARE AND VIRUSES Dr. Benjamin Livshits
Malware: Different Types 23 A virus is a computer Spyware is software that aids in gathering information about a program that is capable of person or organization without making copies of itself and their knowledge and that may inserting those copies into send such information to other programs. another entity A Trojan often acts as a backdoor, contacting a A worm is a virus that uses controller which can then have a network to copy itself unauthorized access to the onto other computers. affected computer. A drive-by-download attack is a malware delivery technique triggered when the user visits a website.
Wait, There’s More 24
Malware Volume 25 The AV-TEST Institute registers over 450,000 new malicious programs every day http://www.av-test.org/en/statistics/malware/
A Lot of Commercial Activity 26 Cyber Security Market worth $155.74 Billion by 2019 http://www.marketsandmarkets.com/PressReleases/cyber-security.asp
What is a Virus? a program that can infect other programs by modifying them to include a, possibly evolved , version of itself Fred Cohen, 1983
Brief History of Malware 28 Mac users can often be heard to say “I don’t need antivirus software, I have an Apple”. Unfortunately, this is a misguided conclusion. Whilst the dangers are certainly much less than with Windows computers, they do exist nonetheless. Mac users who think they do not need to concern themselves have created an illusion. The claim that Apple users are less threatened than Windows users is currently still correct, but could change rapidly. It was the low market share of Macs that limited the attentions of online criminals; now that Macs are becoming more popular, this state of affairs is changing. http://www.itsecuritywatch.com/
Coevolution: Basic Setup 29 Virus Antivirus Identify a sequence of Wait for user to instructions or data execute an infected file Formulate a signature Scan all files Infect other (binary) Look for signature files by modifying found verbatim them Bottleneck: scanning speed Spread that way
Signatures 30
Signatures Are Updated All The Time 31
Coevolution: Entry Point Scanning 32 Virus Antivirus Entry point scanning Place virus at the entry point or make it directly reachable from the entry Do exploration of point reachable instruction starting with the entry point of the program Make virus small to avoid being easily noticed by Continue until no more user instructions are found
Coevolution: Virus Encryption 33 Virus Antivirus Decryption (and encryption) Decryption routine routines (packers) used by Virus body viruses are easy to fingerprint Decrypt into memory, not do disk Develop signatures to match these routines Set PC to the beginning of the decryption buffer Attempt to decrypt the virus Encrypt with a different body to perform a secondary key before adding virus to verification (x-raying) new executable D E
Simple Decryption Routine 34
Jumping Ahead: Similar Behavior in JavaScript 35
Coevolution: Polymorphic 36 Virus Antivirus Custom detection program Use a mutation engine to generate a (decryption routine, encryption routine) designed to recognize specific pair detection engines Functionally similar or the same, but Generic decryption (GD) syntactically very different Emulator Use the encryption routine to encode Signature matching engine the body of the virus Scan memory/disk at regular intervals in hopes of finding decoded virus body No fixed part of the virus preserved (decryption, encryption, body) D1 D2 E1 E2
Emulation Challenges 37 How long to emulate the execution? Viruses use padding instructions to delay execution. Can also use sleep for a while to slow down the scanner. What is the quality of the emulator? How many CPUs to support? What if decryption starts upon user interactions? How do we trigger it? What about anti-emulation tricks?
AV: Static and Runtime 38 Signature-based virus detection – static techniques Emulation-based detection – runtime technique Generally, both are used at the same time (hybrid)
False Positives 39 A "false positive" is when antivirus software identifies a non-malicious file as a virus. When • this happens, it can cause serious problems. For example, if an antivirus program is configured to immediately delete or quarantine • infected files, a false positive in an essential file can render the operating system or some applications unusable. In May 2007, a faulty virus signature issued by Symantec mistakenly removed essential operating system files, leaving thousands of PCs unable to boot Also in May 2007, the executable file required by Pegasus Mail was falsely detected by Norton AntiVirus as being a Trojan and it was automatically removed, preventing Pegasus Mail from running. Norton anti-virus had falsely identified three releases of Pegasus Mail as malware, and would delete the Pegasus Mail installer file when that happened n response to this Pegasus Mail stated: On the basis that Norton/Symantec has done this for every one of the last three releases of Pegasus Mail, we can only condemn this product as too flawed to use, and recommend in the strongest terms that our users cease using it in favor of alternative, less buggy anti-virus packages
More False Positives 40 In April 2010, McAfee VirusScan detected svchost.exe, a normal Windows binary, as a virus on machines running Windows XP with Service Pack 3, causing a reboot loop and loss of all network access In December 2010, a faulty update on the AVG anti-virus suite damaged 64-bit versions of Windows 7, rendering it unable to boot, due to an endless boot loop created In October 2011, Microsoft Security Essentials removed the Google Chrome browser, rival to Microsoft's own Internet Explorer. MSE flagged Chrome as a Zbot banking trojan
False Alarms 41
Vulnerability Gap 42 As long as user has the right virus signatures and computer has recently been scanner, detection will likely work But the virus landscape changes fast This calls for monitoring techniques for unknown viruses http://www.m86security.com/documents/pdfs/security_labs/m86_security_labs_vulnerability_report.pdf
Recommend
More recommend