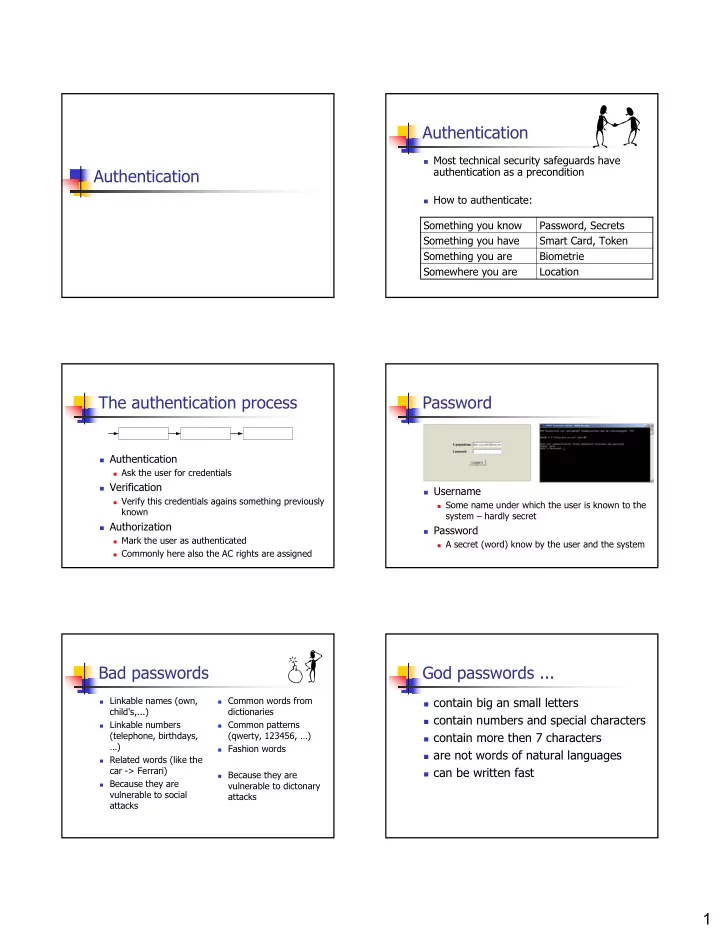

Authentication � Most technical security safeguards have Authentication authentication as a precondition � How to authenticate: Something you know Password, Secrets Something you have Smart Card, Token Something you are Biometrie Somewhere you are Location The authentication process Password � Authentication � Ask the user for credentials � Verification � Username � Verify this credentials agains something previously � Some name under which the user is known to the known system – hardly secret � Authorization � Password � Mark the user as authenticated � A secret (word) know by the user and the system � Commonly here also the AC rights are assigned Bad passwords God passwords ... � Linkable names (own, � Common words from � contain big an small letters child's,...) dictionaries � contain numbers and special characters � Linkable numbers � Common patterns (telephone, birthdays, (qwerty, 123456, …) � contain more then 7 characters …) � Fashion words � are not words of natural languages � Related words (like the car -> Ferrari) � can be written fast � Because they are � Because they are vulnerable to dictonary vulnerable to social attacks attacks 1
Entropy for passwords Password verification � Entropy represents the uncertainty of � Compatre the input with a stored value the password � Passwords need to be stored � This represents how likely it is to guess the password � Plain � Encrypted � The entropy is calculated from the � One way reciprocal probability of each observed � Bi-directional character and its probability of � Passwords need to be transfered apperance � Plain or Encyrpted � H = - Σ p i * log 2 p i Attacks against passwordsystems Ways to harden � Test all possible passwords – brute � Limited number of tries force attack � Wrong inputs slow down the process � Guess likely words – lexical attacks � Challenge Respond � Social engineering � Authorize also the system � Looking for the systems password list � Combining different systems � Attacking the authentication mechanism � Harden the process � Ask the user � Require passwords with high entropy One time passwords Cryptographic techniques � Cryptography for authentication purpose � A password is only valid one‘s � Popular techniques � Technqiues � Kerberos � Transaction numbers (TAN) � Certificates X.509 � Challenge Respond Systems � Hashed with time stamp � Problems � Complex � Infrastructure dependent 2
Security token Smart Cards � Something you have � A card with a chip � Not necessarily for authentication � Popular Representative � e.g. bank card, phone SIM ... � Cryptographic Token � SmartCards � Different types � Problems � ROM Cards � Costly � EEPROM Cards � Technical Infrastructure � Microprocessor cards Attacks against Smart cards Attacks against Smart cards � Protocol attacks � Physical Probing � the communication between the smart � reading data directly from the hardware card and the card reader � Damage part of the chip � Blocking signaling � for example the address counter � block Signals (for example erase signals � Reverse engineering � Freeze or reset the card � reveal the chip design and gain knowledge � make the content of the RAM readable Biometrics Concepts � The security relies on the property of a � Physical human being � DNA � Face � Measuring some aspects of the human � Fingerprint anatomy or physiology and compare it � Iris with previously recorded values � Hand geometry � Behavioral � Problems: Humans change over time � Voice � Signature Verification 3
Conventional biometrics Fingerprints � Face recognition - ID Cards � Look at the friction ridges that cover fingertips � The oldest and probably most accepted � Branches and end points geometry – method commonly 16 characteristics � Pores of the skin � Average security – result of studies � Easy to deployed and relative limited � Handwritten signatures resistance � Is in Europe highly accepted � Problems � There is a statistical probability of mismatch – � Good enough security the number of variation is limited � Fingerprints are mostly „noisy“ � Alteration is easy Iris Scan Problems with biometrics � Not exact enough � Patterns in the Iris are � False positives and Positive False are common recognized � Technical difficult � Iris codes provide the lowest � The technology is new false accept rates of any � Privacy problems known system – US Study � Sicknesses and pregnacy can be recognized � Social problems � Problems � Usage of system � Get people to put there eye into � Revelation generates problems a scanner � Data leak out incidentally � Systems might be ulnerable to � When the use became widespread your data will be known by a lot of people simple photographies Singel Sign-on � Only one sign-on for all applications � Techniques � Save password – but how? Questions ? � Issue a ticket � Trends � Passport 4
Recommend
More recommend