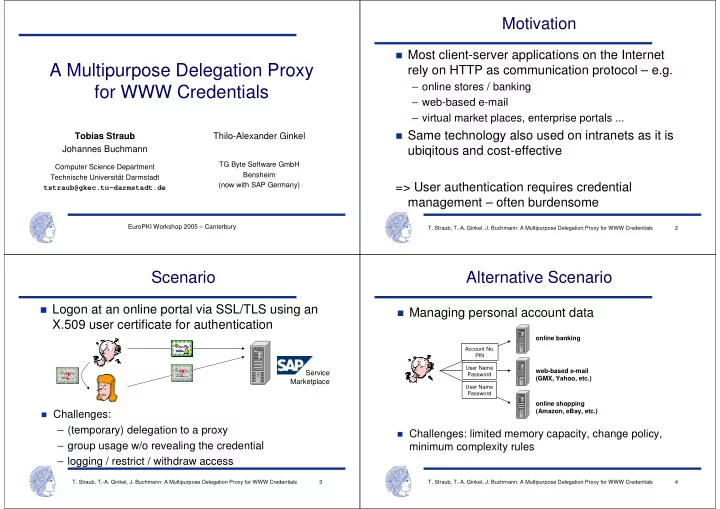

Motivation � Most client-server applications on the Internet A Multipurpose Delegation Proxy rely on HTTP as communication protocol – e.g. – online stores / banking for WWW Credentials – web-based e-mail – virtual market places, enterprise portals ... � Same technology also used on intranets as it is Tobias Straub Thilo-Alexander Ginkel Johannes Buchmann ubiqitous and cost-effective TG Byte Software GmbH Computer Science Department Bensheim Technische Universität Darmstadt (now with SAP Germany) => User authentication requires credential tstraub@gkec.tu-darmstadt.de management – often burdensome EuroPKI Workshop 2005 – Canterbury T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 2 Scenario Alternative Scenario � Logon at an online portal via SSL/TLS using an � Managing personal account data X.509 user certificate for authentication online banking Account No. PIN User Name web-based e-mail ? Service ? Password (GMX, Yahoo, etc.) Marketplace User Name Password online shopping (Amazon, eBay, etc.) � Challenges: – (temporary) delegation to a proxy � Challenges: limited memory capacity, change policy, – group usage w/o revealing the credential minimum complexity rules – logging / restrict / withdraw access T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 3 T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 4
Requirements System Architecture Examined 4 variants: 1. Let proxy impersonate credential owner w/o need to � 3 man-in-the-middle (MITM) approaches where client reveal secret. authenticates towards gateway and gateway authenticates 2. Protect credential from unauthorized access. towards target host 3. Keep track of actual credential usage and restrict it. � 1 client-side solution where client has access to credential DB 4. Support common WWW authentication mechanisms (Basic/Digest Auth., form-based, client certificate- based) 5. Easy-to-use, small footprint solution, operate transparently. T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 5 T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 6 Application Server Variant HTTP Server Variant � Gateway = web server � Gateway = machine providing remote login facilities , e.g. � calling particular URL initiates retrival of credential and – VNC (full-screen desktop) authentication to target host for actual URL, e.g. go to – X11 (forwarding single browser windows) http://gateway/amazon.com instead of http://amazon.com � Credentials managed by browser running on gateway � response returned to client seems to come from gateway Drawbacks: Drawbacks: � no proper delegation or policy enforcement, � MITM has to do hyperlink-rewriting to redirect subsequent � low protection level for credentials, requests to gateway, not directly to target host � user experience, � This is difficult for JavaScript and Macromedia Flash � network latency � Java applets won't run properly due to Sandbox restrictions. T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 7 T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 8
HTTP Proxy Variant Client-Side Architecture � Gateway = intelligent HTTP proxy � Standard web browser enhanced with additional functionality to access centralized credential store. � Well-known approach on the Web � Shouldn't be too difficult ... � Proxy works as forwarding agent acting both as server and client => HTTP-based credentials supported � Alternatively fit up client’s TCP/IP stack or socket library naturally � Allows seamless integration and end-to-end security (confidentiality in this case) Drawback: � SSL normally tunneled through proxy => breaking up Drawback: end-to-end security (i.e. confidentiality) � Credentials are revealed to browser => malicious client could steal them. T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 9 T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 10 Comparison TLS Authentication Proxy Prototype – proxy for HTTP and HTTPS � For each variant , we assessed: – stores credentials and manages - Compatibility and Standard Compliance , access rights (ACL) - Transparency , – authentication method towards - Usability , proxy can be chosen flexibly and - Security Characteristics , independently of actual - Deployment Costs authentication method (see paper for details, please) - – credential usage is � Decided to implement HTTP proxy architecture logged – considered it superior to other MITM architectures – Web interface provided for administration and delegation – lower estimated developement costs compared to client- side variant T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 11 T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 12
Data flow for an SSL target web site with Data flow for an HTTP target web site certificate-based authentication Client Proxy Server Client Proxy Server CONNECT server:443 HTTP/1.1 GET http://server/ HTTP/1.1 HTTP/1.1 302 Moved SSL Handshake Location: https://server:9443/ HTTP/1.1 200 OK CONNECT server:9443 HTTP/1.1 SSL Handshake Replicate certificate SSL Handshake Create Certificate GET /index.html HTTP/1.1 GET / HTTP/1.1 GET / HTTP/1.1 SSL Handshake 401 Authorization Required GET /index.html HTTP/1.1 GET / HTTP/1.1 WWW-Authenticate: [...] Payload Payload Payload Payload T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 13 T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 14 Session Management Authorization Issues � Proxy identifies end-users by distinguished name in � Basic/Digest Authentication: each request has to be their certificate, PKCS#12 tokens issued on-the-fly authenticated � Access rights modeled by database table indexed by – TLS Authentication Proxy does not wait for "401" responses => Basic Authentication speeded up pair (user ID, credential ID) – Not possible for Digest Authentication as it is a challenge- � Constraints defined on fine-grained basis (time frame for response scheme access, maximum number of total/daily logins, � Usually session management used for form-based restriction to a subset of web pages …) authentication � Flag indicates whether delegation is allowed, currently – HTTP Cookies fully supported by prototype, can re-authenticate no restriction on number of sub-delegations automatically to avoid time-outs T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 15 T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 16
Deployment Conclusions 1. Key and certificate distribution: � Work motivated by requirement to delegate X.509 credentials => ship root certificate within PKCS#12 file � TLS Authentication Proxy offers transparent credential management and proxy authentication 2. Web browser configuration: � Users authenticated w/o knowing credential – Web Proxy Auto-Discovery Protocol => allows delegation and group usage – obtain Proxy Auto-Configuration file from the network � Pseudo SSO: target host is unaware of what's going on automatically or manually � Zero footprint solution, reasonable deployment costs � Central storage for credentials instead of spread all over Privacy Issues: clients, however Single Point of Failure/Attack – PAC file adjusted to only route traffic through proxy that requires credential – URLs of such hosts obscured by hash function (PAC file is JavaScript code) T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 17 T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 18 Thank you for your attention! Questions? Contact: Tobias Straub / TU Darmstadt tstraub@gkec.tu-darmstadt.de www.informatik.tu-darmstadt.de/GK/participants/tstraub/ T. Straub, T.-A. Ginkel, J. Buchmann: A Multipurpose Delegation Proxy for WWW Credentials 19
Recommend
More recommend