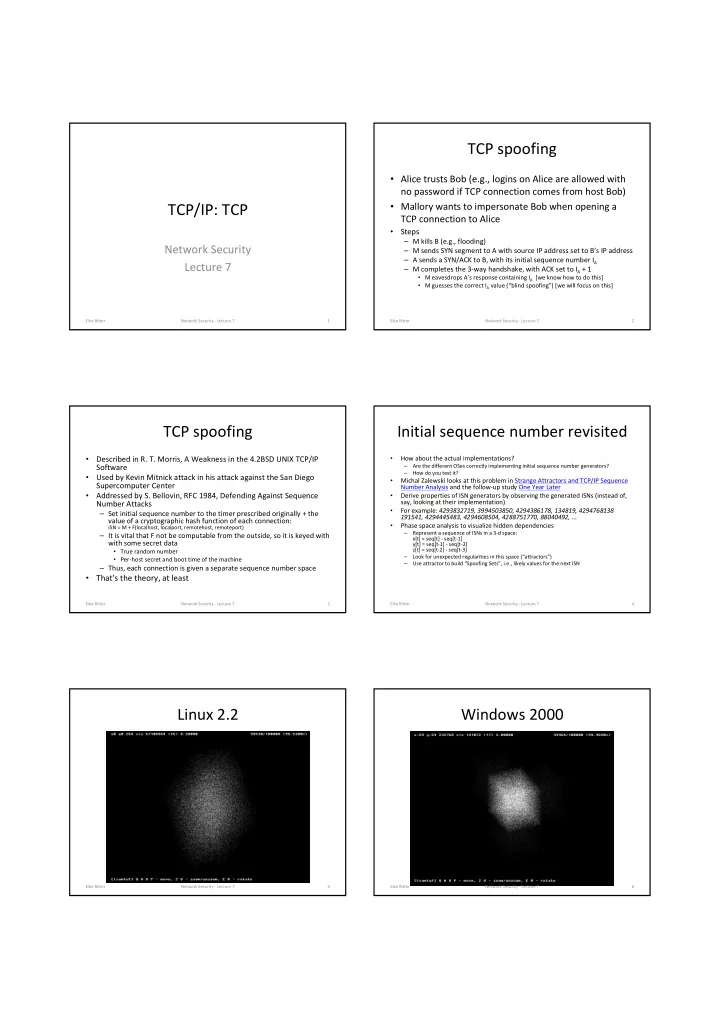

TCP spoofing • Alice trusts Bob (e.g., logins on Alice are allowed with no password if TCP connection comes from host Bob) • Mallory wants to impersonate Bob when opening a TCP/IP: TCP TCP connection to Alice Steps • – M kills B (e.g., flooding) Network Security – M sends SYN segment to A with source IP address set to B’s IP address – A sends a SYN/ACK to B, with its initial sequence number I A Lecture 7 – M completes the 3-way handshake, with ACK set to I A + 1 • M eavesdrops A’s response containing I A [we know how to do this] • M guesses the correct I A value (“blind spoofing”) [we will focus on this] Eike Ritter Network Security - Lecture 7 1 Eike Ritter Network Security - Lecture 7 2 TCP spoofing Initial sequence number revisited Described in R. T. Morris, A Weakness in the 4.2BSD UNIX TCP/IP How about the actual implementations? • • Are the different OSes correctly implementing initial sequence number generators? Software – How do you test it? – Used by Kevin Mitnick attack in his attack against the San Diego • Michal Zalewski looks at this problem in Strange Attractors and TCP/IP Sequence • Supercomputer Center Number Analysis and the follow-up study One Year Later Addressed by S. Bellovin, RFC 1984, Defending Against Sequence Derive properties of ISN generators by observing the generated ISNs (instead of, • • say, looking at their implementation) Number Attacks For example: 4293832719, 3994503850, 4294386178, 134819, 4294768138 – Set initial sequence number to the timer prescribed originally + the • 191541, 4294445483, 4294608504, 4288751770, 88040492, ... value of a cryptographic hash function of each connection: Phase space analysis to visualize hidden dependencies ISN = M + F(localhost, localport, remotehost, remoteport) • Represent a sequence of ISNs in a 3-d space: – It is vital that F not be computable from the outside, so it is keyed with – x[t] = seq[t] - seq[t-1] with some secret data y[t] = seq[t-1] - seq[t-2] z[t] = seq[t-2] - seq[t-3] • True random number Look for unexpected regularities in this space (“attractors”) • Per-host secret and boot time of the machine – Use attractor to build “Spoofing Sets”, i.e., likely values for the next ISN – – Thus, each connection is given a separate sequence number space That’s the theory, at least • Eike Ritter Network Security - Lecture 7 3 Eike Ritter Network Security - Lecture 7 4 Linux 2.2 Windows 2000 Eike Ritter Network Security - Lecture 7 5 Eike Ritter Network Security - Lecture 7 6
Windows 98 Cisco IOS - before Eike Ritter Network Security - Lecture 7 7 Eike Ritter Network Security - Lecture 7 8 Cisco IOS - after TCP hijacking We saw: TCP spoofing + address-based authentication = attacker wins • – What if authentication is performed by other means, e.g., password-based? – Attacker needs a more powerful attack Attacker waits for TCP connection to be established and then creates a • desynchronized state on both ends of the connection – Two points cannot communicate Then creates acceptable packets for both ends • – At this point, attacker completely controls the connection Performed by using spoofed TCP segments to • – Insert data in the streams – Reset an existing connection (denial of service) First described in • L. Joncheray, “Simple Active Attack Against TCP” Eike Ritter Network Security - Lecture 7 9 Eike Ritter Network Security - Lecture 7 10 TCP hijacking TCP hijacking • Scenario: attacker wants to inject data into existing TCP • What happens next? connection between two hosts • Server sends ACK to A – Think of telnet connection between A and B – Remember: attacker is spoofing A’s address – M wants to hijack connection to inject commands that will be – SRV.ACK = M executed on B • Client receives segment, notices it is out of order, and • Attacker waits until the connection to hijack is “quiet” sends ACK with the “right” sequence number – All the sent data has been acknowledged – CLN.ACK = N (N < M) • Attacker injects data into the stream (“desynchronization”) • Server receives segment, notices it is out of order, and – echo “+ +” > ~/.rhosts sends ACK with the “right” sequence number – Source IP is spoofed to A’s IP address – SRV.ACK = M – SEG.SEQ = last ACK from the server • . . . – SEG.ACK = last SEQ from the server • “Ack storm” • Datagram is acceptable and will be processed by the server Eike Ritter Network Security - Lecture 7 11 Eike Ritter Network Security - Lecture 7 12
ACK storm Fixing the ACK storm 172.16.48.2.1026 > 172.16.48.1.23: P 1015112:1015133(21) ack 4056578923 • How to prevent/stop? 172.16.48.1.23 > 172.16.48.2.1026: . seq 4056578923 ack 1015133 172.16.48.2.1026 > 172.16.48.1.23: . seq 1015112 ack 4056578923 • Disable the client so that it does not reply to server’s ACKs 172.16.48.1.23 > 172.16.48.2.1026: . seq 4056578923 ack 1015133 • Resynchronize 172.16.48.2.1026 > 172.16.48.1.23: . seq 1015112 ack 4056578923 172.16.48.1.23 > 172.16.48.2.1026: . seq 4056578923 ack 1015133 – Send “null data” to client so that it resyncs with the server 172.16.48.2.1026 > 172.16.48.1.23: . seq 1015112 ack 4056578923 – In telnet, NOP commands 172.16.48.1.23 > 172.16.48.2.1026: . seq 4056578923 ack 1015133 • Just wait 172.16.48.2.1026 > 172.16.48.1.23: . seq 1015112 ack 4056578923 172.16.48.1.23 > 172.16.48.2.1026: . seq 4056578923 ack 1015133 – ACKs that carry no data are not retransmitted if lost 172.16.48.2.1026 > 172.16.48.1.23: . seq 1015112 ack 4056578923 – ACK storm will congest the network 172.16.48.1.23 > 172.16.48.2.1026: . seq 4056578923 ack 1015133 172.16.48.2.1026 > 172.16.48.1.23: . seq 1015112 ack 4056578923 – So eventually, ACKs will be lost 172.16.48.1.23 > 172.16.48.2.1026: . seq 4056578923 ack 1015133 • ARP spoofing 172.16.48.2.1026 > 172.16.48.1.23: . seq 1015112 ack 4056578923 172.16.48.1.23 > 172.16.48.2.1026: . seq 4056578923 ack 1015133 – Spoofs client so that server ACKs only reach the attacker 172.16.48.2.1026 > 172.16.48.1.23: . seq 1015112 ack 4056578923 Eike Ritter Network Security - Lecture 7 13 Eike Ritter Network Security - Lecture 7 14 SYN flooding SYN flooding defenses • Denial of service attack • How would you protect from this attack? • Attacker sends a SYN packet • Filtering • Victim replies with SYN/ACK segment – To block spoofed packets • Increase the length of the queue storing half-open – Internally, the victim allocates resources to keep track of the half-open connection connections – “Transmission Control Block” (TCB) • Recycle existing half-open connections when the limit is – In practice, some memory reached and new connections arrive • Attacker does not send ACK • Reduce the SYN-RECEIVED timeout • The victim has limited number of available TCBs to keep – Time waited between receiving a SYN and recycling the track of the half-open connection resources allocated to this connection • Do not allocate any state at all for a received SYN – When limit is reached, it will not accept any other connection • Can the attacker easily hide (spoof) its source address? – SYN cookie Eike Ritter Network Security - Lecture 7 15 Eike Ritter Network Security - Lecture 7 16 SYN cookie • Encode the connection state in the initial sequence number and/or other fields (e.g., the Timestamp option) • Set ISN to t | m | s – t: timestamp – m: MSS – s: result of crypto function on server address and port, client address and port, t • When ACK is received – Recover the ISN (ACK – 1) – Check t against current timestamp and check that it is close enough – Recompute s and check that it is valid – Decode m Eike Ritter Network Security - Lecture 7 17
Recommend
More recommend