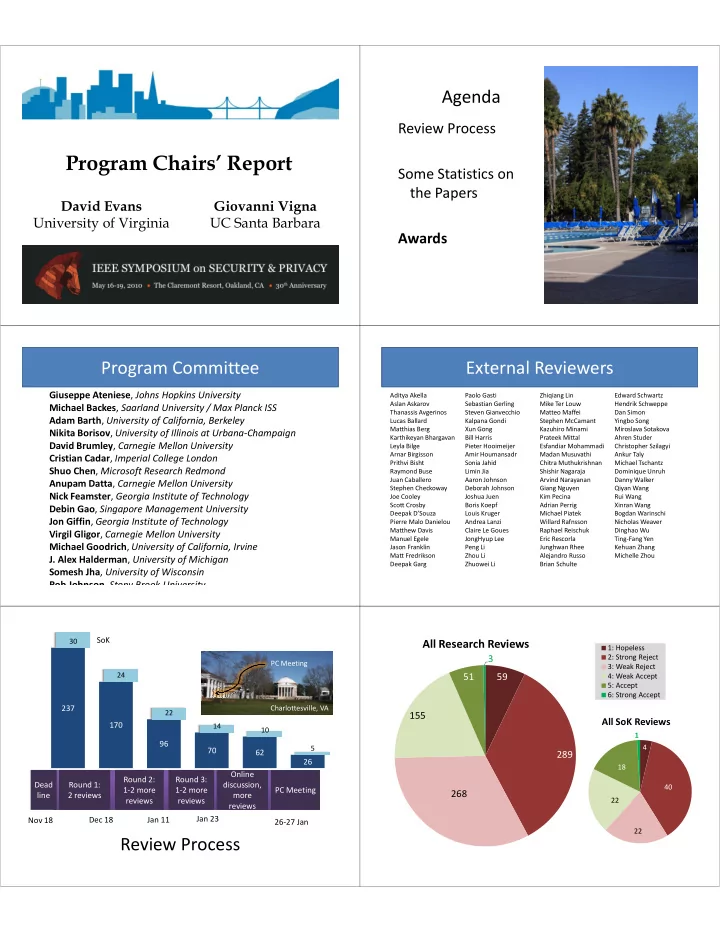

Agenda Review Process ���������������������� Some Statistics on the Papers ����������� �������������� ���������������������� ���������������� Awards Program Committee External Reviewers Giuseppe Ateniese , Johns Hopkins University Aditya Akella Paolo Gasti Zhiqiang Lin Edward Schwartz Aslan Askarov Sebastian Gerling Mike Ter Louw Hendrik Schweppe Michael Backes , Saarland University / Max Planck ISS Thanassis Avgerinos Steven Gianvecchio Matteo Maffei Dan Simon Adam Barth , University of California, Berkeley Lucas Ballard Kalpana Gondi Stephen McCamant Yingbo Song Matthias Berg Xun Gong Kazuhiro Minami Miroslava Sotakova Nikita Borisov , University of Illinois at Urbana-Champaign Karthikeyan Bhargavan Bill Harris Prateek Mittal Ahren Studer David Brumley , Carnegie Mellon University Leyla Bilge Pieter Hooimeijer Esfandiar Mohammadi Christopher Szilagyi Arnar Birgisson Amir Houmansadr Madan Musuvathi Ankur Taly Cristian Cadar , Imperial College London Prithvi Bisht Sonia Jahid Chitra Muthukrishnan Michael Tschantz Shuo Chen , Microsoft Research Redmond Raymond Buse Limin Jia Shishir Nagaraja Dominique Unruh Juan Caballero Aaron Johnson Arvind Narayanan Danny Walker Anupam Datta , Carnegie Mellon University Stephen Checkoway Deborah Johnson Giang Nguyen Qiyan Wang Nick Feamster , Georgia Institute of Technology Joe Cooley Joshua Juen Kim Pecina Rui Wang Scott Crosby Boris Koepf Adrian Perrig Xinran Wang Debin Gao , Singapore Management University Deepak D’Souza Louis Kruger Michael Piatek Bogdan Warinschi Jon Giffin , Georgia Institute of Technology Pierre Malo Danielou Andrea Lanzi Willard Rafnsson Nicholas Weaver Matthew Davis Claire Le Goues Raphael Reischuk Dinghao Wu Virgil Gligor , Carnegie Mellon University Manuel Egele JongHyup Lee Eric Rescorla Ting-Fang Yen Michael Goodrich , University of California, Irvine Jason Franklin Peng Li Junghwan Rhee Kehuan Zhang Matt Fredrikson Zhou Li Alejandro Russo Michelle Zhou J. Alex Halderman , University of Michigan Deepak Garg Zhuowei Li Brian Schulte Somesh Jha , University of Wisconsin Rob Johnson , Stony Brook University SoK 30 All Research Reviews 1: Hopeless 2: Strong Reject 3 PC Meeting 3: Weak Reject 24 51 59 4: Weak Accept 5: Accept 6: Strong Accept 237 Charlottesville, VA 22 155 All SoK Reviews 170 14 10 1 96 4 5 70 62 289 26 18 Online Round 2: Round 3: Dead Round 1: discussion, 40 1-2 more 1-2 more PC Meeting 268 line 2 reviews more reviews reviews 22 reviews Jan 23 Dec 18 Jan 11 Nov 18 26-27 Jan 22 Review Process
0.0 0.5 1.0 1.5 2.0 2.5 3.0 3.5 4.0 4.5 5.0 10% 15% 20% 25% 30% 35% 40% 0% 5% Luxembourg Language-based security Singapore Web security Submissions per Million Switzerland Accepted Research Papers Secure information flow USA (shared by authors) Canada System security 32 Belgium Formal Methods Language-based security AND Web security: 100% (3/3) Austria Acceptance Rate by Topic Embedded systems security Israel Application security Germany 58 Attacks and defenses Australia 3 Norway Hardware security 3 United Kingdom Average Oman 9 Malware Tunisia Security architectures France Finland Network security 0 Italy 0.00 0.05 0.10 0.15 Authentication Netherlands 34 Security and privacy policies Korea Austria Anonymity Spain Israel Metrics Slovak Republic Switzerland Greece Forensics Taiwan Belgium Intrusion detection (shared by authors) Malaysia Accepts per million USA Access control Iran 6: Strong Accept 5: Accept 4: Weak Accept 3: Weak Reject 2: Strong Reject Netherlands Usability and security Hong Kong Pakistan Protocol security UK Japan Cryptography France Chile Privacy-preserving systems China Italy Distributed systems security India China 100 100 120 140 160 10 20 30 40 50 60 70 80 90 20 40 60 80 0 0 Mike Reiter, University of North Carolina Yoshi Kohno*, University of Washington Paper Awards Committee System security Somesh Jha, University of Wisconsin US Academic David Evans, University of Virginia Giovanni Vigna, UC Santa Barbara Network security submissions Number of Germany # accepted × 1/(acceptance rate) Attacks and defenses counting each contact author / number of authors US Commercial Application security Canada Cryptography Submits/Accepts by Topic United Kingdom Best Paper Awards Privacy-preserving systems Papers by Country Security architectures China Protocol security India Intrusion detection Singapore Access control France Formal Methods Switzerland Malware Italy Web security Distributed systems security Australia * Not for Best Practical Paper Award Secure information flow Korea Authentication Pakistan Security and privacy policies Belgium Anonymity .org Hardware security Spain Language-based security Usability and security Austria Forensics Japan Accepted (Scaled) Submitted Embedded systems security Luxembourg Metrics Iran Recovery Israel None Netherlands Censorship-resistance
Best Practical Paper Best Practical Paper Chip and PIN is Broken Presented by IEEE Security & Privacy Steven J. Murdoch Magazine to the “paper most likely to Saar Drimer immediately improve the security of Ross Anderson current environments and systems.” Mike Bond University of Cambridge Best Student Paper Best Paper TaintScope: A Checksum-Aware Directed SCiFI - A System for Secure Face Fuzzing Tool for Automatic Software Identification Vulnerability Detection Margarita Osadchy Tielei Wang, Peking University Benny Pinkas Tao Wei, Peking University Ayman Jarrous Guofei Gu, Texas A & M University Boaz Moskovich Wei Zou, Peking University Univesity of Haifa Thanks! Organizers Giovanni Vigna Ulf Lindqvist (General Chair) Deb Frincke (Registration) Program Committee Al Shaffer (Treasurer) members Jenny McNeill (Publications chair) External reviewers Carrie Gates (Poster and workshops chair) Adrienne Felt (Web/design chair) Authors Angelos Stavrou (Short talks chair) Peter Neumann (30 th Anniversary papers) Technical Committee: Hilarie Orman, Terry Benzel, Sven Dietrich, Cynthia Irvine
Recommend
More recommend