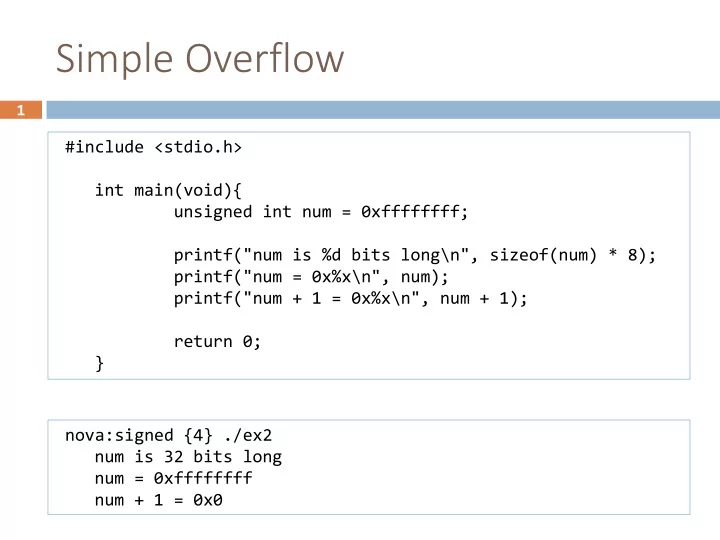

Simple Overflow 1 #include <stdio.h> int main(void){ unsigned int num = 0xffffffff; printf("num is %d bits long\n", sizeof(num) * 8); printf("num = 0x%x\n", num); printf("num + 1 = 0x%x\n", num + 1); return 0; } nova:signed {4} ./ex2 num is 32 bits long num = 0xffffffff num + 1 = 0x0
In Integer Overflows Exploits range of value integers can store int stores between -2 32 and 2 32 -1 Ex: signed two-byte in Cause unexpected wrap-around scenarios Attacker passes int greater than max (positive) -> value wraps around to the min (negative!) Can cause unexpected program behavior, possible buffer overflow exploits Completely crazy from a more abstract point of view
Signed/unsigned Confusion http://phrack.org/issues/60/10.html
There’s more: Memory Safety Issues 4 buffer overflow use after free read/dereference of uninitialized memory double-free null pointer dereference
Memory ry Safety 5 Computer languages such as C and C++ that support arbitrary pointer arithmetic, casting, and deallocation are typically not memory safe. There is a variety of approaches to fi find er errors in programs in C/C++. C/C++ is too close to hardware and provides little out of the box in terms of safe(r) programming
Alternatives? Better Languages 6 Most high-level programming languages avoid the problem by disallowing pointer arithmetic and casting entirely, and by using garbage coll llection for memory management. Generally, elevates the level of vulnerabilities Buffer overruns are not an issue, but other things like XSS are
Attack Defense Zigzag 7 Stack-based buffer overruns StackGuard Heap-based buffer overruns ALSR and NX Heap sprays and ROC Specific defenses
Shellshock 8 That may al allo low a remote attacker to Shellshock is the media- send you text that you hand over to a Bash script as harmless looking friendly name for a security data, only to find that it gets processed as if it were code, or bug found in Bash, a program commands. command shell This sort of trickery is often known as command injection, because it involves sneaking in operating The bug is what's known as a system commands, hoping that they get run by mistake. Rem emote Cod ode Ex Executio ion vulnerability
9 Shellshock
Remote Execution? 10 10 Wait, remote command execution on bash? How can someone re remotely execu cute commands on a lo local shell ll? The issue starts with mod_cgi and how web servers interact with CGI programs (written in Perl, PHP, Shell or any other language). The web server passes (environment) user variables to them so they can do their work. In simple terms, this vulnerability allows an attacker to pass a command as a variable that gets executed by bash. http://blog.sucuri.net/2014/09/bash-vulnerability-shell- shock-thousands-of-cpanel-sites-are-high-risk.html
Patch is the Message 11 11 It means that if you are using mod_cgi on your webserver and you have a CGI written in shell script, you are in deep trouble. Drop everything now and patch your servers. If you have CGI’s written on any other language, but you are using “system()”, “( backticks )” or executing any commands from the CGI, you are in deep trouble. Drop every rything now and patch your r servers. If you don’t know what you have, Drop everything now and patch your r servers.
Patch and Test 12 12 #sudo apt-get [root@yourserver ~]# install bash env x='() { :;}; echo vulnerable' bash -c 'echo hello' - or - #sudo yum update bash: warning: x: ignoring bash function definition attempt bash: error importing function definition for `x' hello
Try rying This on bicycle.c .cs 13 13 But someone needs to come in and acti tively ly patch the machine once the bug is found This is too late – the vulnerability may alr lready have been exp xplo loit ited
CSE484/CSE584 ROBUST APPLICATION CODE THROUGH ANALYSIS Dr. Benjamin Livshits
Cost of f Fixing a Defect 15 15
How Do We Find Bugs? 16 16
Runtime Monitoring 17 17 Pros: Instrument code for testing Easy to reproduce the Heap memory: Purify bug Relatively easy to Valgrind: http://valgrind.org implement Perl tainting (information Con ons: flow) Slows down the Java race condition program significantly 10x-40x slowdowns checking Test only: cannot be used in production Not all paths executed
Black-box Testing 18 18 Pros: Fuzzing and pen enetration tes estin ting Easy to reproduce the Black-box web application security bug analysis Don’t need to understand the code Typically, tries to provide cleverly Can be done by crafted unexpected inputs someone else Also knows as inputs of death Con ons: Example: Have no visibility into Peach fuzzer program logic http://peachfuzzer.com/ Has low coverage Possibly lots of antifuzzer, Dfuz, SPIKE, GPF, etc. missing vulnerabilities
Static Analysis 19 19 Pros: Static code analysis toos Near-perfect code coverage, exercise Coverity all paths Can be run, Tools from Microsoft incrementally as part of development like Prefix and Prefast process Cons: FindBugs (for Java) Can be imprecise Can scale poorly Fortify (for security) Can produce results that are tough to interpret
From Coverity 20 20
From CPyChecker 21 21
From FxCop 22 22
From PVS-Studio 23 23
From Visual Lint 24 24
XSS Detect 25 25
Visual Studio 26 26
Outline General discussion of static analysis tools Goals and limitations Approach based on abstract states More about one specific approach Property checkers from Engler et al., Coverity Sample security-related results Slides from: S. Bugrahe, A. Chou, I&T Dillig, D. Engler, J. Franklin, A. Aiken, Mitchll …
Static Analysis Coverage Advantage 1 1 2 2 4 4 Entry Entry Manual testing only examines 1 3 4 small subset of 1 1 1 2 4 1 3 4 behaviors 1 2 4 1 3 4 2 2 3 1 2 3 1 2 4 1 3 4 1 2 4 1 2 3 1 3 4 4 4 1 2 3 1 2 3 1 3 4 1 2 4 1 2 4 1 3 4 . . Exit Exit Software Behaviors .
Program Analyzers analyze large code bases Code Report Type Line 1 mem leak 324 2 buffer oflow 4,353,245 false alarm Program 3 sql injection 23,212 Analyzer 4 stack oflow 86,923 false alarm 5 dang ptr 8,491 Spec … … … 10,502 info leak 10,921 potentially may emit reports many false alarms warnings
Static Analysis Goals Bug fi finding: identify code that the programmer wishes to modify or improve Correctness: Verify the absence of certain classes of errors
Soundness and Completeness Property Definition Soundness If the program contains an error, the analysis will report a warning. “Sound for reporting correctness” Completeness If the analysis reports a warning, the program will contain an error. “Complete for reporting correctness”
Decidable? Complete Incomplete Reports all errors Reports all errors May report false alarms Sound Reports no false alarms Undecidable Decidable Unsound May not report all errors May not report all errors May report false alarms Reports no false alarms Decidable Decidable
Over- and Underapproximations Sound Modules Reported Over-approximation of Error Behaviors . . . approximation is too False Behaviors Alarm coarse … yields too many false alarms Software
Does This Program Ever Crash? entry X 0 Is Y = 0 ? yes no X X + 1 X X - 1 Is Y = 0 ? yes no Is X < 0 ? exit yes no crash
Does This Program Ever Crash? entry X 0 Is Y = 0 ? yes no X X + 1 X X - 1 Is Y = 0 ? yes no Is X < 0 ? exit yes no infeasible path! overly imprecise crash … program will never crash
Try Analyzing Without Approximation entry X 0 X = 0 Is Y = 0 ? yes no X = 2 X = 1 X = 0 X X + 1 X X - 1 X = 3 X = 2 X = 1 X = 1 X = 2 X = 3 Is Y = 0 ? X = 3 X = 2 X = 1 yes no Is X < 0 ? exit yes no X = 1 X = 2 X = 3 crash non-termination! … therefore, need to approximate
Dataflow Analysis Framework dataflow elements X = 0 d in d out = f(d in ) X X + 1 f d out X = 1 dataflow equation transfer function
Applying the Dataflow Approach X = 0 d in1 X X + 1 f1 d out1 = f 1 (d in1 ) X = 1 d out1 d out1 = d in2 X = 1 d in2 Is Y = 0 ? f2 d out2 = f 2 (d in2 ) d out2 X = 1
Meet/Join Operator ⊔ d out1 = f 1 (d in1 ) d in d in d out2 = f 2 (d in2 ) 1 2 f 1 f 2 d join = d out1 ⊔ d out2 d out1 d out 2 d join d join = d in3 d in3 f 3 d out3 = f 3 (d in3 ) d out3 least upper bound operator What is the space of dataflow elements, ? Example: union of possible values What is the least upper bound operator, ⊔ ?
Try Analyzing with “Signs ” Approximation … entry X 0 X = 0 Is Y = 0 ? yes no X = 0 X = 0 X X + 1 X X - 1 X = pos X = neg X = T lost Is Y = 0 ? precision X = T X = T yes no Is X < 0 ? exit yes no X = T X = T crash terminates... … but reports false alarm … therefore, need more precision
Recommend
More recommend