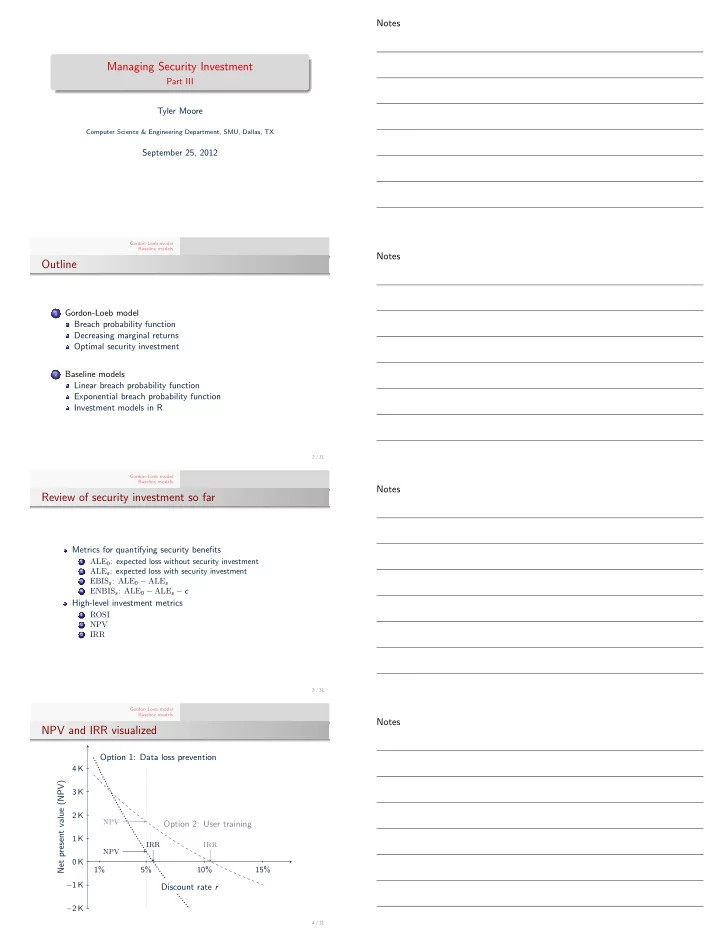

Notes Managing Security Investment Part III Tyler Moore Computer Science & Engineering Department, SMU, Dallas, TX September 25, 2012 Gordon-Loeb model Baseline models Notes Outline Gordon-Loeb model 1 Breach probability function Decreasing marginal returns Optimal security investment Baseline models 2 Linear breach probability function Exponential breach probability function Investment models in R 2 / 31 Gordon-Loeb model Baseline models Notes Review of security investment so far Metrics for quantifying security benefits ALE 0 : expected loss without security investment 1 ALE s : expected loss with security investment 2 EBIS s : ALE 0 − ALE s 3 ENBIS s : ALE 0 − ALE s − c 4 High-level investment metrics ROSI 1 2 NPV IRR 3 3 / 31 Gordon-Loeb model Baseline models Notes NPV and IRR visualized Option 1: Data loss prevention 4 K Net present value (NPV) 3 K 2 K NPV Option 2: User training 1 K IRR IRR NPV 0 K 1% 5% 10% 15% − 1 K Discount rate r − 2 K 4 / 31
Gordon-Loeb model Baseline models Notes Security investment questions worth answering Q: Should we invest in security? A: Yes, if ENBIS s > 0 Q: Should we invest in defense A or B? A: Choose the one with higher ROSI (or NPV if considering longer time horizons) Q: How much should we invest? A: The Gordon-Loeb model can help offer an answer 5 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Gordon-Loeb model Lawrence Gordon Martin Loeb 7 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Gordon-Loeb model Model investment decision over a single period Use Bernoulli loss assumption (suffer loss λ with fixed probability p s ) The probability of loss depends on two factors: security level and the system’s inherent vulnerability The breach probability function maps these factors to probabilities Gordon and Loeb’s model use assumptions about security investment to derive optimal investment levels based on the breach probability functions 8 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Breach probability function S : R + × [0 , 1] → [0 , 1] Maps a security investment c and an exogenous vulnerability v ∈ [0 , 1] to the probability p of incurring a loss of size λ . Furthermore: An invulnerable organization ( v = 0) is exposed to no risk regardless of its security investment: p = S ( c , 0) = 0 for all c Vulnerability determines the probability of loss of an organization which does not invest in security: p = S (0 , v ) = v for all v . S is continuous and twice-differentiable 9 / 31
Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Breach probability functions v S I ( c , v ) = ( α c + 1) β S II ( c , v ) = v α c +1 α > 0 and β > 1 capture security productivity ⇒ Measure how efficiently the security investment reduces probability of loss Can think of α ∈ (0 , 1] as coefficient for linear model relating c to security level s (i.e., s = α · c ) 10 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Visualizing S I ( c , v ) for α = 1 1 v = 1 β = 5 4 β = 2 Probability of loss p 1 v 2 S I ( c , v ) = v = 1 ( α c + 1) β 2 = 1 4 v = 1 4 0 0 1 2 3 4 5 Security investment c 11 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Back to last week’s benefit metrics EBIS = λ ( v − S ( c , v )) ENBIS = λ ( v − S ( c , v )) − c The Gordon-Loeb model assumes that for all v ∈ [0 , 1], and all c > 0, S is strictly convex in c , i.e., δ c S ( c , v ) < 0 and δ cc S ( c , v ) > 0 (Note: δ c is the first partial derivative with respect to c , and δ cc is the second partial derivative with respect to c .) 12 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Decreasing marginal returns to security investment λ v EBIS ∆ EBIS 2 ∆ EBIS 1 v S ( c , v ) ∆ c ∆ c 0 c 1 c 2 Security investment c 13 / 31
Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Why is it reasonable to model security investment with decreasing marginal returns? In the Gordon-Loeb model, decreasing marginal returns emerge from convexity assumption about S Why is this defensible? Benefits to security are often concave – a rational defender 1 implements the measures with best cost-benefit ratio first, leaving less efficient alternatives if the security budget increases Costs to security are often convex – combining defenses 2 can be more expensive than deploying just one (compatibility issues, management complexity) Empirical validation (or refutation) of this assumption is an open research question 14 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Choosing an optimal security investment Given a range of security investment levels, how can a manager choose the optimal amount? If security investment adheres to diminishing marginal returns, then we can identify the investment level c ∗ that maximizes the expected net benefit ENBIS 15 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Choosing an optimal security investment Informally, we look for the investment level where the marginal benefit of security is equal to its marginal cost Formally, we seek the cost level c ∗ where: c ∗ = max ENBIS ( c ) c We find c ∗ using the first-order condition (FOC): δ c EBIS ( c ∗ ) = 1 16 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Choosing an optimal security investment We find c ∗ using the first-order condition (FOC): δ c EBIS ( c ∗ ) = 1 � � δ c λ ( v − S ( c ∗ , v ) = 1 δ c � λ v − λ S ( c ∗ , v ) � = 1 − λ δ c S ( c ∗ , v ) = 1 For c ∗ > 0, this condition maximizes ENBIS because EBIS is concave. 17 / 31
Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Choosing an optimal security investment, visualized c λ v EBIS max c ENBIS ENBIS = EBIS − c 45 ◦ 0 c ∗ Security investment c 18 / 31 Breach probability function Gordon-Loeb model Decreasing marginal returns Baseline models Optimal security investment Notes Gordon-Loeb Rule The Gordon-Loeb model is very sensitive to values assigned to v : small differences can lead to very different optimal investment levels Furthermore, v can be hard to estimate in practice So they came up with a rule of thumb: never spend more than 37% of your expected loss on security Definition (Gordon–Loeb Rule): The optimal security investment c ∗ is bounded from above by λ/ e , where e is the base of the natural logarithm. 19 / 31 Linear breach probability function Gordon-Loeb model Exponential breach probability function Baseline models Investment models in R Notes Other models of security investment are possible Just because Gordon and Loeb came first doesn’t mean that security investment must be modeled in this way The concavity of security benefits is a nice feature, but might not always apply Simpler breach probability functions could also be used 21 / 31 Linear breach probability function Gordon-Loeb model Exponential breach probability function Baseline models Investment models in R Notes Linear breach probability function Let’s start with the simplest possible model 1 We use the Bernoulli loss assumption Two outcomes { 0 , λ } � 0 : 1 − p s , λ : p s � 2 We assume security investment is effective c = λ s For unit loss λ = 1: c = s 3 We can even use a linear breach probability function S ( s , v ) = v · (1 − s ) for s ∈ [0 , 1] . 22 / 31
Recommend
More recommend