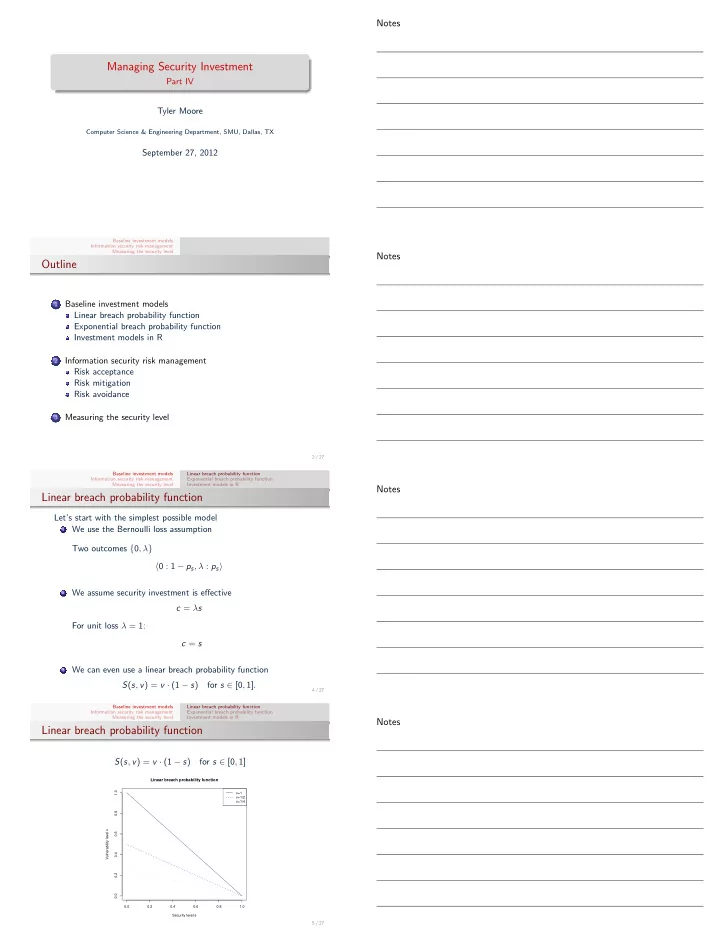

Notes Managing Security Investment Part IV Tyler Moore Computer Science & Engineering Department, SMU, Dallas, TX September 27, 2012 Baseline investment models Information security risk management Measuring the security level Notes Outline Baseline investment models 1 Linear breach probability function Exponential breach probability function Investment models in R Information security risk management 2 Risk acceptance Risk mitigation Risk avoidance Measuring the security level 3 2 / 27 Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes Linear breach probability function Let’s start with the simplest possible model 1 We use the Bernoulli loss assumption Two outcomes { 0 , λ } � 0 : 1 − p s , λ : p s � 2 We assume security investment is effective c = λ s For unit loss λ = 1: c = s 3 We can even use a linear breach probability function S ( s , v ) = v · (1 − s ) for s ∈ [0 , 1] . 4 / 27 Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes Linear breach probability function S ( s , v ) = v · (1 − s ) for s ∈ [0 , 1] Linear breach probability function 1.0 v=1 v=1/2 v=1/4 0.8 Vulnerability level v 0.6 0.4 0.2 0.0 0.0 0.2 0.4 0.6 0.8 1.0 Security level s 5 / 27
Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes One final simplification We reduce the action space to just two possibilities – secure ( s = 0) and insecure ( s = 1) State Security s = c /λ Probability of loss p Expected loss E ( λ ) Insecure 0 v λ v Secure 1 0 0 What are the trade-offs between using a linear breach probability function and the one used in the Gordon-Loeb model? 6 / 27 Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes Exponential breach probability function If diminishing marginal returns is important to include in the model, and we want to retain the Bernoulli loss assumption, then the breach probability function should be convex But the complexity of Gordon-Loeb’s function S I ( c , v ) = ( α c +1) β can be hard to justify v We can use a simpler model with one variable for tuning the security productivity instead of two: S ( s , v ) = v β − s We require β > 1, and also require S ( s , 0) = 0 for all s and S (0 , v ) = v , as in the Gordon-Loeb model 7 / 27 Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes Exponential breach probability function, visualized 1 v = 1 β = 5 4 β = 2 β = 8 Probability of loss p 1 v = 1 2 2 1 4 0 0 1 2 3 4 5 Security level s 8 / 27 Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes Optimal security investment We can compute the optimal security investment s ∗ using the first-order condition of the ENBIS δ s ( ENBIS ( s ∗ )) = 0 δ s � v − S ( s , v ) − s � = 0 v − v β − s − s � � δ s = 0 , which has an analytical solution for v > 0: s = log ( v log( β )) log( β ) Why is this a reasonable first-order condition? Why does it lead to optimal investment? 9 / 27
Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes A visual explanation of the FOC c λ v EBIS max c ENBIS ENBIS = EBIS − c 45 ◦ 0 c ∗ Security investment c 10 / 27 Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes Another way to maximize benefit δ s ( EBIS ( s ∗ )) = 1 which is equivalent to δ s ( ENBIS ( s ∗ )) = 0 Why? Substitute ENBIS ( s ∗ ) = EBIS ( s ∗ ) − s ∗ δ s ( EBIS ( s ∗ ) − s ∗ ) = 0 δ s ( EBIS ( s ∗ )) − δ s ( s ∗ ) = 0 δ s ( EBIS ( s ∗ )) − 1 = 0 δ s ( EBIS ( s ∗ )) = 1 11 / 27 Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes One more caveat Some values of β will be negative for the investment condition In particular, s ∗ < 0 for β ∈ 1 , e 1 / v � � Consequently, we set the optimal security level as follows: � log ( v log( β )) � s ∗ = max , 0 log( β ) 1 , e 1 / v � � If β ∈ , we say that the organization is indefensible The security investment must become more productive to justify any investment 12 / 27 Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes How optimal investment varies λ Optimal security level s ∗ 2 λ/ e (Gordon–Loeb rule of thumb) v = 1 λ 4 v = 1 2 e 2 v = 1 4 0 1 5 10 20 30 40 50 60 indefensible ( v = 1 2 ) indefensible ( v = 1) Security productivity β 13 / 27
Baseline investment models Linear breach probability function Information security risk management Exponential breach probability function Measuring the security level Investment models in R Notes Investment models in R Let’s first review how to make the plot for the linear breach probability function Then let’s explore how optimal investment varies for the exponential breach probability Today’s code: http://lyle.smu.edu/~tylerm/courses/ econsec/code/secinv3.R 14 / 27 Baseline investment models Risk acceptance Information security risk management Risk mitigation Measuring the security level Risk avoidance Notes Information security risk management Just as it can be useful to translate infosec risks and defenses into the language of investment (ROSI, NPV, etc.), one must also be aware of terminology from risk management As IT becomes essential to many businesses, border between information security investment and general risk management has blurred 16 / 27 Baseline investment models Risk acceptance Information security risk management Risk mitigation Measuring the security level Risk avoidance Notes Risk management terminology overview Risk Risk man- Risk analysis agement monitoring identification acceptance validation quantification mitigation documentation avoidance transfer 17 / 27 Baseline investment models Risk acceptance Information security risk management Risk mitigation Measuring the security level Risk avoidance Notes Risk acceptance After risks are identified and quantified, they must be “managed” The simplest option is to do nothing Such “risk acceptance” is prudent when: Worst-case loss is small enough to be paid from proceeds or 1 reserves Probability of occurrence is smaller than other business risks 2 that threaten the organization’s survival This is why the security policies for start-ups are often weaker than for entrenched firms 18 / 27
Recommend
More recommend