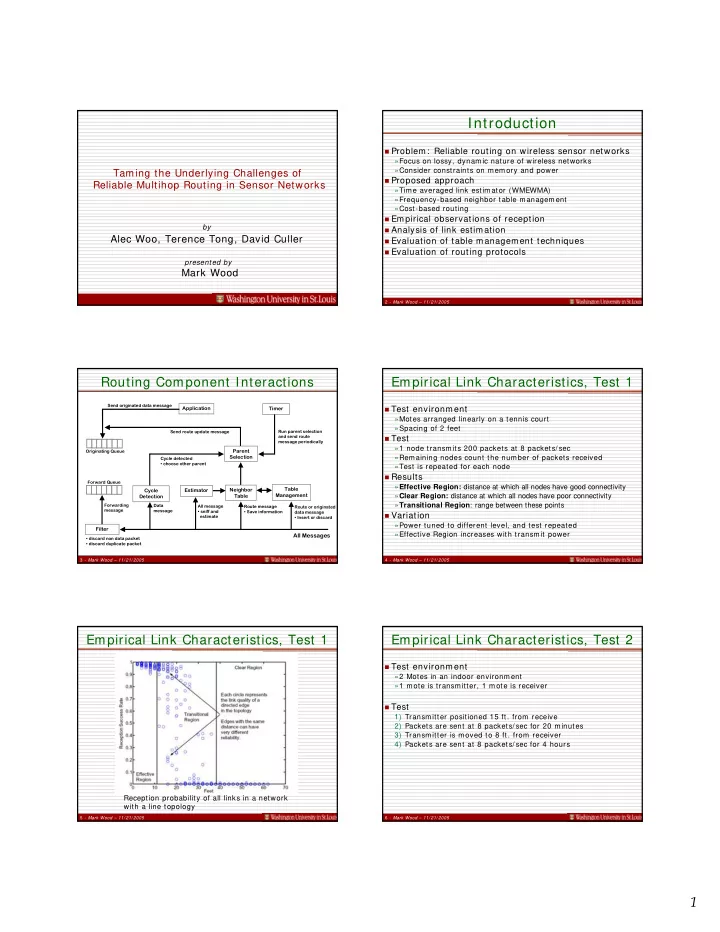

Introduction � Problem: Reliable routing on wireless sensor networks »Focus on lossy, dynamic nature of wireless networks »Consider constraints on memory and power Taming the Underlying Challenges of � Proposed approach Reliable Multihop Routing in Sensor Networks »Time averaged link estimator (WMEWMA) »Frequency-based neighbor table management »Cost-based routing � Empirical observations of reception by � Analysis of link estimation Alec Woo, Terence Tong, David Culler � Evaluation of table management techniques � Evaluation of routing protocols presented by Mark Wood 2 - Mark Wood – 11/ 21/ 2005 Routing Component Interactions Empirical Link Characteristics, Test 1 Send originated data message Application Timer � Test environment »Motes arranged linearly on a tennis court »Spacing of 2 feet Send route update message Run parent selection and send route � Test message periodically »1 node transmits 200 packets at 8 packets/ sec Parent Originating Queue Selection »Remaining nodes count the number of packets received Cycle detected • choose other parent »Test is repeated for each node � Results Forward Queue » Effective Region: distance at which all nodes have good connectivity Neighbor Table Cycle Estimator Table Management Detection » Clear Region: distance at which all nodes have poor connectivity » Transitional Region : range between these points Forwarding Data All message Route message Route or originated message message • sniff and • Save information data message � Variation estimate • Insert or discard »Power tuned to different level, and test repeated Filter »Effective Region increases with transmit power All Messages • discard non data packet • discard duplicate packet 3 - Mark Wood – 11/ 21/ 2005 4 - Mark Wood – 11/ 21/ 2005 Empirical Link Characteristics, Test 1 Empirical Link Characteristics, Test 2 � Test environment »2 Motes in an indoor environment »1 mote is transmitter, 1 mote is receiver � Test 1) Transmitter positioned 15 ft. from receive 2) Packets are sent at 8 packets/ sec for 20 minutes 3) Transmitter is moved to 8 ft. from receiver 4) Packets are sent at 8 packets/ sec for 4 hours Reception probability of all links in a network with a line topology 5 - Mark Wood – 11/ 21/ 2005 6 - Mark Wood – 11/ 21/ 2005 1
Empirical Link Characteristics, Test 2 Empirical Observations � Distribution »Small, irregular region of good connectivity »Some distant nodes with good connectivity »Large, irregular region of poor connectivity »Some asymmetric links � Individual node reception »Receive packets frequently from small group of good neighbors »Receive packets less frequently from large group of more distant nodes »More weakly-connected nodes than well-connected nodes »More packet loss from weakly-connected nodes »More frequent reception from well-connected nodes � Results » Link quality abruptly changes » Mean link quality is relatively stable at a given distance » High variation in instantaneous link quality 7 - Mark Wood – 11/ 21/ 2005 8 - Mark Wood – 11/ 21/ 2005 Connectivity Cell Link Quality Model � Empirical observations suggest a probabilistic link behavior � Goal: Predict link quality of neighboring nodes � Link quality model »Compute the mean and variance from empirical data »For each node pair, associate a probability based on this � Can be used in design of neighbor management policy Cell connectivity of a node in a grid with 8-foot spacing using link quality model 9 - Mark Wood – 11/ 21/ 2005 10 - Mark Wood – 11/ 21/ 2005 Link Estimation WMEWMA � Ideal estimator � Computes average success rate over time period » React quickly » Estimations stable Packets Received in t » Memory footprint small WMEWMA(t, α ) = » Computation load small max(Packets Expected in t, Packets Received in t) � Active: Probe the links » Used in wired networks (IGRP, EI GRP) where t is time window and α controls history of estimator. � Passive: Collect statistics on packets it hears » Easy to do in wireless networks � EWMA smoothens the average » But must listen to packets not addressed to it � Synthetic loss generators evaluated: � Tuned for two settings » Linear regression on Kalman filters » Exponentially weighted moving average (EWMA) »Stable: minimize the settling time » Moving average »Agile: minimize the mean squared error » Time weighted moving average » Packet loss/ success interval with EWMA » Window mean with EWMA (WMEWMA) 11 - Mark Wood – 11/ 21/ 2005 12 - Mark Wood – 11/ 21/ 2005 2
WMEWMA Performance Link Quality Distribution A center node in an 80x80 grid with 4 feet spacing has up to 207 neighbors with varying link quality 30% of the nodes WMEWMA (t = 30, α = 0.6) with stable 75% is “good neighbor” quality setting using empirical traces 13 - Mark Wood – 11/ 21/ 2005 14 - Mark Wood – 11/ 21/ 2005 Neighbor Table Choosing Neighbors � Want to keep a sufficient number of good neighbors in � Contains status and routing entries for neighbors the table � Fields include: � The table should reflect which nodes are most useful for »MAC address routing »Routing cost »Parent address »Child flag � Want to discard nodes with low-quality links »Reception link quality »Send link quality � Lim ited space »Link estimator data structures � Insertion, eviction and reinforcement is done by the Neighbor Table Manager 15 - Mark Wood – 11/ 21/ 2005 16 - Mark Wood – 11/ 21/ 2005 Replacement Algorithms Replacement Algorithm Comparison � FIFO: First-I n-First-Out » Cycles through the neighbors in round-robin style » Eviction is based on order of entry, so no reinforcement � CLOCK: Approximation of Least-Recently-Used (LRU) » Cursor cycles through neighbors looking for unmarked one » If neighbor is marked, then unmark it and go to next one » When neighbor is loaded into memory, mark it » When neighbor has been referenced, mark it � LRH: Least-Recently Heard » Resident entry is made most recently heard � FREQUENCY: Simple policy to estimate frequency Number of good neighbors maintainable at different » Keeps a frequency count for each entry in the table densities with a table size of 40 entries 17 - Mark Wood – 11/ 21/ 2005 18 - Mark Wood – 11/ 21/ 2005 3
Parent Selection Packet Snooping � Cost: An abstract measure of distance � All packets are broadcast »Estimate of energy required to reach destination � Every node is a “router” � Cost metrics »Number of hops � Snooping helps prevent cycles »Expected number of transmissions »Other estimate of cost � Child Pruning: »Node receives a forwarding message with an unreachable route � Other reasons for switching to a new parent: »Message is forwarded with a ‘NO_ROUTE’ address »Link quality drops below threshold »Neighbors snoop the message and learn about unreachable route »Sink is unreachable through current parent »Cycle is detected � Solves counting-to-infinity problem 19 - Mark Wood – 11/ 21/ 2005 20 - Mark Wood – 11/ 21/ 2005 Cycle Prevention Counting to Infinity - Example [Geoffrey M. Voelker, UCSD] � Nodes represent costs to reach sink A/2 B/1 � Why im portant? »In wireless networks, bandwidth is the most scarce resource � Link betw een B and sink fails A/2 B/1 Classic techniques to control cycles Split-Horizon: � B hears of a route to sink via A w ith cost 2 A/2 B/1 Routes are prevented from exiting the interface where they were received update Poison-Reverse: � B sw itches to the “better” ( but invalid) route A/2 B/3 Routes heard through an interface are sent out that interface with metric = infinity � Applying sim ilar techniques to motes: � A hears from B and increases its cost A/4 B/3 »Route invalidation when a node becomes disjoint update »Tree pruning by ‘NACKing’ children’s traffic � Cycle continues as w e count to infinity… 21 - Mark Wood – 11/ 21/ 2005 22 - Mark Wood – 11/ 21/ 2005 Duplicate Packet Elimination Queue Management � Duplicate packets � When forwarding messages dominate the queue »Created upon retransmission when ACK is lost »Prevents node from originating data »If forwarded, can cause more retransmissions »Prevents cycle detection »Cause contention »Wasted energy � Queuing technique »Separate forwarding and originating messages into two queues � Proposed solution »Priority given to originating messages » Sender ID and Sequence Number appended to header »Fair queuing policy is implemented »Parent retains originator ID and originating sequence number of child entries in neighbor table 23 - Mark Wood – 11/ 21/ 2005 24 - Mark Wood – 11/ 21/ 2005 4
Recommend
More recommend