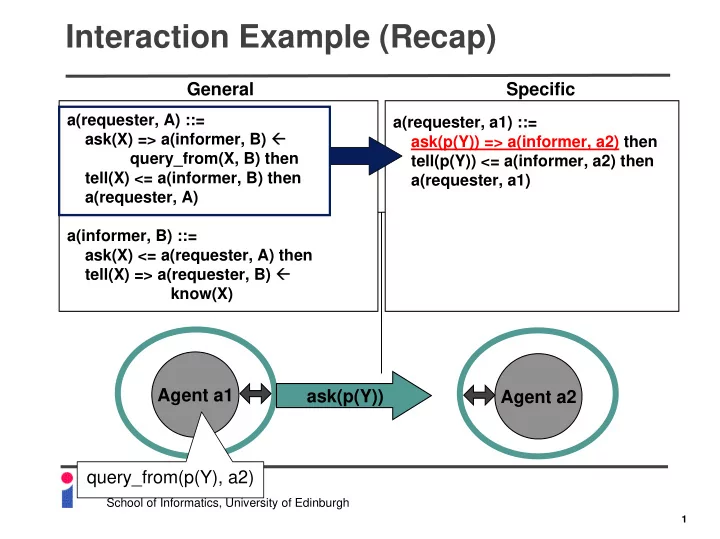

Interaction Example (Recap) General Specific a(requester, A) ::= a(requester, a1) ::= ask(X) => a(informer, B) � ask(p(Y)) => a(informer, a2) then query_from(X, B) then tell(p(Y)) <= a(informer, a2) then tell(X) <= a(informer, B) then a(requester, a1) a(requester, A) a(informer, B) ::= ask(X) <= a(requester, A) then tell(X) => a(requester, B) � know(X) Agent a1 ask(p(Y)) Agent a2 query_from(p(Y), a2) Logic Programming School of Informatics, University of Edinburgh 1
Interaction Example (Recap) Specific General a(requester, A) ::= a(requester, a1) ::= ask(X) => a(informer, B) � ask(p(Y)) => a(informer, a2) then query_from(X, B) then tell(p(Y)) <= a(informer, a2) then tell(X) <= a(informer, B) then a(requester, a1) a(requester, A) a(informer, a2) ::= a(informer, B) ::= ask(p(Y)) <= a(requester, a1) then ask(X) <= a(requester, A) then tell(p(Y)) => a(requester, a1) � tell(X) => a(requester, B) � know(p(Y)) know(X) Agent a1 Agent a2 ask(p(Y)) Logic Programming School of Informatics, University of Edinburgh 2
Interaction Example (Recap) General Specific a(requester, A) ::= ask(X) => a(informer, B) � a(requester, a1) ::= query_from(X, B) then ask(p(Y)) => a(informer, a2) then tell(X) <= a(informer, B) then tell(p(Y)) <= a(informer, a2) then a(requester, A) a(requester, a1) a(informer, B) ::= a(informer, a2) ::= ask(X) <= a(requester, A) then ask(p(a)) <= a(requester, a1) then tell(X) => a(requester, B) � tell(p(a)) => a(requester, a1) know(X) Agent a1 tell(p(a)) Agent a2 know(p(a)) Logic Programming School of Informatics, University of Edinburgh 3
Interaction Example (Recap) General Specific a(requester, a1) ::= a(requester, A) ::= ask(X) => a(informer, B) � ask(p(a)) => a(informer, a2) then tell(p(a)) <= a(informer, a2) then query_from(X, B) then a(requester, a1) ::= tell(X) <= a(informer, B) then ask(X) => a(informer, B) � a(requester, A) query_from(X, B) then tell(X) <= a(informer, B) then a(informer, B) ::= a(requester, a1) ask(X) <= a(requester, A) then a(informer, a2) ::= tell(X) => a(requester, B) � ask(p(a)) <= a(requester, a1) then know(X) tell(p(a)) => a(requester, a1) tell(p(a)) Agent a1 Agent a2 Logic Programming School of Informatics, University of Edinburgh 4
Protocol Rewriting Example (1) a(requester, A) ::= a(requester, A) ::= ask(X) => a(informer, B) � c(ask(X) => a(informer, B)) then query_from(X, B) then tell(X) <= a(informer, B) then tell(X) <= a(informer, B) then a(requester, A) a(requester, A) ask(X) => a(informer, B) � c(ask(X) => a(informer, B)) query_from(X, B) (and the appropriate message is sent) Logic Programming School of Informatics, University of Edinburgh 5
Protocol Rewriting Example (2) a(requester, A) ::= a(requester, A) ::= c(ask(X) => a(informer, B)) then c(ask(X) => a(informer, B)) then tell(X) <= a(informer, B) then c(tell(X) <= a(informer, B)) then a(requester, A) a(requester, A) tell(X) <= a(informer, B) c(tell(X) <= a(informer, B)) (if the appropriate message has been received) Logic Programming School of Informatics, University of Edinburgh 6
Protocol Rewriting Example (3) a(requester, A) ::= a(requester, A) ::= c(ask(X) => a(informer, B)) then c(ask(X) => a(informer, B)) then c(tell(X) <= a(informer, B)) then c(tell(X) <= a(informer, B)) then a(requester, A) ::= a(requester, A) ask(X) => a(informer, B) � query_from(X, B) then tell(X) <= a(informer, B) then a(requester, A) a(requester, A) ::= a(requester, A) …. Logic Programming School of Informatics, University of Edinburgh 7
Protocol Rewriting Role ::= Def Role ::= E Def E A or _ E A E _ or B E B E A then B E then B A E A then B A then E closed(A), B E C � M <= A c(M <= A) message_in(M), k(C). M => A � C c(M => A) k(C), message_out(M). a(R,X) � C a(R,X) ::= Def k(C), pclause(a(R,X) ::= Def). null � C c(null) k(C). closed(X) means that part X of the protocol has been completed. message_in(M) means that the agent has received message M message_out(M) puts message M in the agent’s output buffer. k(C) means C is believed by the agent. Logic Programming School of Informatics, University of Edinburgh 8
Protocol Rewriting expand(Role ::= Def, Role ::= E) :- expand(Def, E). expand(A or _, E) :- expand(A, E). expand(_ or B, E) :- expand(B, E). expand(A then B, E then B) :- expand(A, E). expand(A then B, A then E) :- closed(A), expand(B, E). expand(C � M <= A, c(M <= A)) :- message_in(M), k(C). expand(M => A � C, c(M => A)) :- k(C), message_out(M). expand(a(R,X) � C, a(R,X) ::= Def) :- k(C), pclause(a(R,X) ::= Def). expand(null � C, c(null)) :- k(C). Logic Programming School of Informatics, University of Edinburgh 9
Exhaustive Rewriting expansion(Clause, Final) :- expand(Clause, Expanded), expansion(Expanded, Final). expansion(Clause, Clause) :- \+ expand(Clause, _). Logic Programming School of Informatics, University of Edinburgh 10
Deciding when a Protocol is Closed closed(c(_)). closed(A or _) :- closed(A). closed(_ or B) :- closed(B). closed(A then B) :- closed(A), closed(B). closed(_ ::= Def) :- closed(Def). Logic Programming School of Informatics, University of Edinburgh 11
Satisfying a Constraint (Example) k(A and B) :- !, k(A), k(B). k(X) :- meta_pred(X, Call), !, Call. k(X) :- \+ meta_pred(X, _), call_direct(X), X. meta_pred(not(X), \+ k(X)). meta_pred(setof(E,G,S), setof(E,k(X),S)). call_direct(X) :- (predicate_property(X, built_in) ; predicate_property(X, interpreted) ; predicate_property(X, imported_from(_))), !. Logic Programming School of Informatics, University of Edinburgh 12
Asynchronous Interaction Constraint Protocol Send to Fetch from solver expander server server Linda out in Agent a2 Agent a1 server tuple space holds Prolog clauses can add or remove blocking/unblocking read Logic Programming School of Informatics, University of Edinburgh 13
Recommend
More recommend