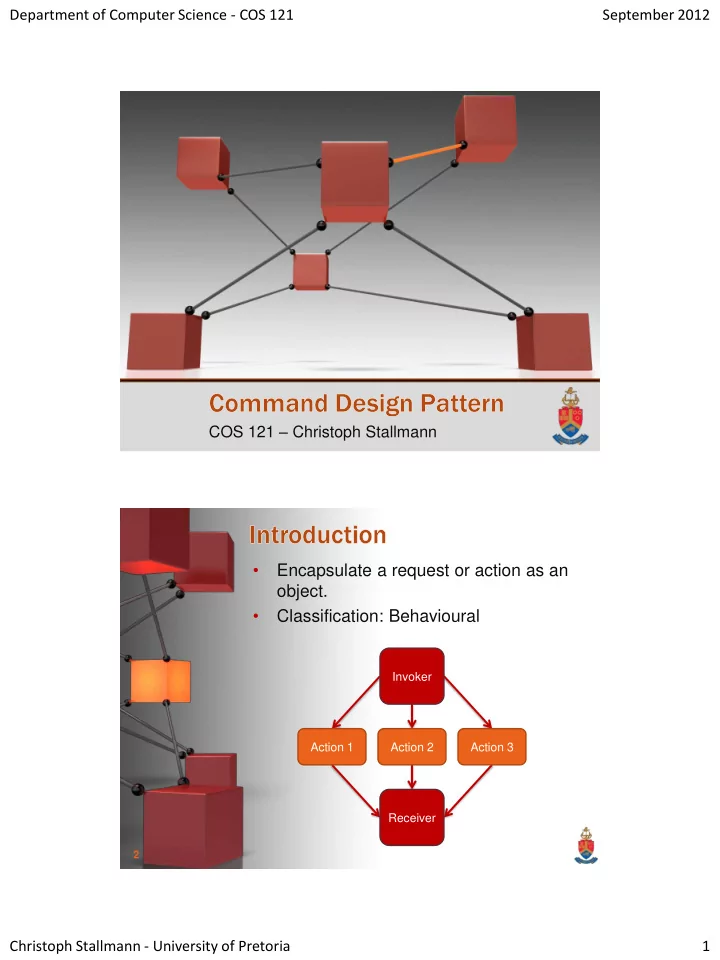

Department of Computer Science - COS 121 September 2012 COS 121 – Christoph Stallmann 1 • Encapsulate a request or action as an object. • Classification: Behavioural Invoker Action 1 Action 2 Action 3 Receiver 2 Christoph Stallmann - University of Pretoria 1
Department of Computer Science - COS 121 September 2012 • Easy to add new commands. • Queue different commands and execute them in order. • Log different actions. • Support undoable operations. 3 4 Christoph Stallmann - University of Pretoria 2
Department of Computer Science - COS 121 September 2012 • Often abstract. • Defines an interface for executing a command or action. 5 • Defines a binding between the receiver and an action. • Implements the execute function. • The execute() function calls the Receiver’s action() function. 6 Christoph Stallmann - University of Pretoria 3
Department of Computer Science - COS 121 September 2012 • Knows how to execute a specific action. • Any class can serve as a Receiver. 7 • Asks the Command to carry out a request. 8 Christoph Stallmann - University of Pretoria 4
Department of Computer Science - COS 121 September 2012 • The application. • Creates the Concrete Command and sets its receiver. • Often this responsibility is delegated to the Invoker. 9 • Initial state. Invoker Command 1 Command 2 Command 3 Receiver 10 Christoph Stallmann - University of Pretoria 5
Department of Computer Science - COS 121 September 2012 • Connect the Receiver to the Commands. Invoker Command 1 Command 2 Command 3 Receiver 11 • Commands are now connected to the Receiver. Invoker Command 1 Command 2 Command 3 Receiver 12 Christoph Stallmann - University of Pretoria 6
Department of Computer Science - COS 121 September 2012 • The Invoker changes or receives external request. Invoker Command 1 Command 2 Command 3 Receiver 13 • The Invoker executes a specific Command. Invoker Command 1 Command 2 Command 3 Receiver 14 Christoph Stallmann - University of Pretoria 7
Department of Computer Science - COS 121 September 2012 • The Command calls a specific action on the receiver. Invoker Command 1 Command 2 Command 3 Receiver 15 • The Receiver executes a specific action. Invoker Command 1 Command 2 Command 3 Receiver 16 Christoph Stallmann - University of Pretoria 8
Department of Computer Science - COS 121 September 2012 • Depending on the request, the Invoker might also execute a different command. Invoker Command 1 Command 2 Command 3 Receiver 17 • http://youtu.be/K1XeTF87Rgk 18 Christoph Stallmann - University of Pretoria 9
Department of Computer Science - COS 121 September 2012 Squad – Receiver Mouse – Invoker 19 Squad – Receiver Mouse – Invoker Select squad 20 Christoph Stallmann - University of Pretoria 10
Department of Computer Science - COS 121 September 2012 Squad – Receiver Mouse – Invoker 21 Squad – Receiver Mouse – Invoker Left mouse click on the screen 22 Christoph Stallmann - University of Pretoria 11
Department of Computer Science - COS 121 September 2012 Mouse – Invoker Squad – Receiver 23 Squad – Receiver Mouse Mouse – Invoker click on the grenade button 24 Christoph Stallmann - University of Pretoria 12
Department of Computer Science - COS 121 September 2012 Squad – Receiver Mouse – Invoker 25 Squad – Receiver Mouse Mouse – Invoker click on the retreat button 26 Christoph Stallmann - University of Pretoria 13
Department of Computer Science - COS 121 September 2012 Squad – Receiver Mouse – Invoker 27 28 Christoph Stallmann - University of Pretoria 14
Department of Computer Science - COS 121 September 2012 29 30 Christoph Stallmann - University of Pretoria 15
Department of Computer Science - COS 121 September 2012 • Decoupling • Decouples the object that invokes an operation from the one that performs it. • Extensibility: • Commands can easily be manipulated and extended. • Composition: • Assemble commands in more complex composite/macro commands. • Addition: • Easy to add new Commands. 31 • Intelligence: • How intelligent should a command be? • One extreme is to delegate everything to the Receiver, in the other extreme the Command does everything. • Undo and redo operations: • Commands can undo/redo operations. • Command must keep additional state to handle these operations. 32 Christoph Stallmann - University of Pretoria 16
Department of Computer Science - COS 121 September 2012 • Chain od Responsibility: • Commands can server as request objects. • Composite: • To implement macro Commands. • Memento: • Keep state for undo operations. • Prototype: • Commands can be copied to be place in a history list. 33 COS 121 – Christoph Stallmann 34 Christoph Stallmann - University of Pretoria 17
Recommend
More recommend