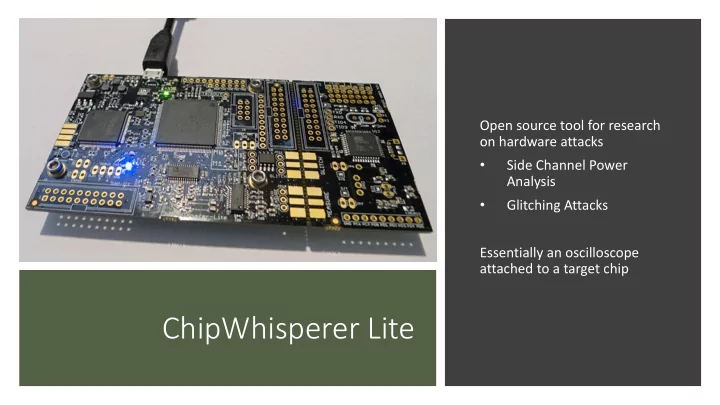

Open source tool for research on hardware attacks • Side Channel Power Analysis • Glitching Attacks Essentially an oscilloscope attached to a target chip ChipWhisperer Lite
Modeling Power Consumption Every device requires power to run (static Dynamic Power – Current required to charge or power) discharge data lines Data moving through the device changes power 00110000 transitioning to 00100011 consumption (dynamic power) • 3 bits changed
Force target device to encrypt many different things Log traces of these different encryptions Analyze these different traces and determine subkeys BREAK ENCRYPTION! Correlation Power Analysis
• Connect to Chipwhisper and set up target board Setting up target device • Connect_cwlite _simpleserial
• Connect to Chipwhisper and set up scope to capture traces Setting up oscilloscope • Setup_cwlite_xmega_aes
CAPTURE TRACES! • Settings on left • Captured traces displayed on the right
• attack_cpa Analyze Traces
Attacking AES Encryption
Results table: first row (in white) is the “result key” from analysis. Note this is the same key as used to generate the traces!
How’d it do that?
How AES works: • AES algorithm XORs the key and data • Uses s-box defined lookup table to replace data • S-box is public and known
Breaking AES Above equation is the relationship between a hypothetical guess for each XOR equation (both key and data to encrypt) compared to the actual change in the trace
• Apply hypothetical guesses to each trace and see what matches • Keep track of which hypothetical has best guess Apply hypothetical guesses • Percentage confidence is the [0,1] number below the results
Results Table (again)
Recommend
More recommend