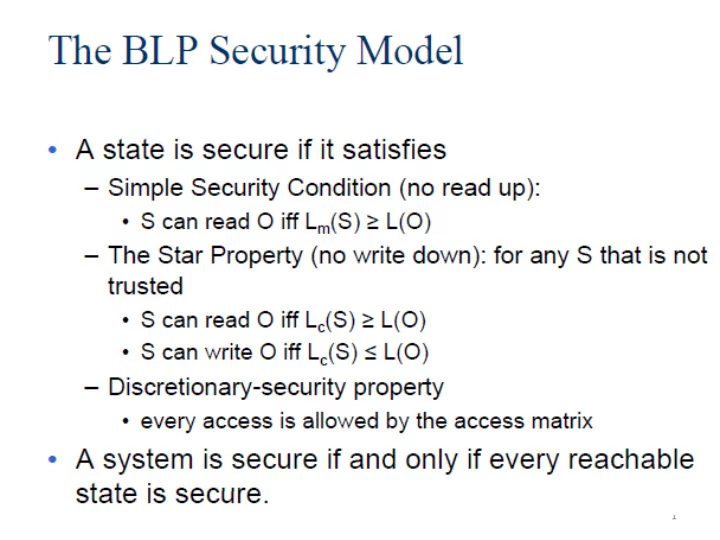

1
2
3
4
5
6
• subject cannot change current levels 7
Objections to BLP (1) • Some processes, such as memory management, need to read and write at all levels • Fix: put them in the trusted computing base • Consequence: once you put in all the stuff a real system needs (backup, recovery, comms, …) the TCB is no longer small enough to be easily verifiable Ross Anderson 8
Objections to BLP(2) • John MacLean ’ s “ System Z ” : as BLP but lets users req. temporary declassification of any file • Fix: add tranquility principles – Strong tranquility: labels never change – Weak tranquility: they don ’ t change in such a way as to break the security policy • Usual choice: weak tranquility using the “ high watermark principle ” – a process acquires the highest label of any resource it ’ s touched • Problem: have to rewrite apps (e.g. license server) Ross Anderson 9
Objections to BLP (3) • High can ’ t acknowledge receipt from Low • This blind write-up is often inconvenient: information vanishes into a black hole • Option 1: accept this and engineer for it (Morris theory) – CIA usenet feed • Option 2: allow acks, but be aware that they might be used by High to signal to Low • Use some combination of software trust and covert channel elimination Ross Anderson 10
Variants of BLP • Noninterference: no input by High can affect what Low can see. So whatever trace there is for High input X, there ’ s a trace with High input Ø that looks the same to Low (Goguen & Messeguer 1982) • Nondeducibility: weakens this so that Low is allowed to see High data, just not to understand it – e.g. a LAN where Low can see encrypted High packets going past (Sutherland 1986) Ross Anderson 11
Variants on Bell-LaPadula (2) • Biba integrity model: deals with integrity rather than confidentiality. It ’ s “ BLP upside down ” – high integrity data mustn ’ t be contaminated with lower integrity stuff • Domain and Type Enforcement (DTE): subjects are in domains, objects have types • Role-Based Access Control (RBAC): current fashionable policy framework Ross Anderson
The Cascade Problem Ross Anderson Connecting the two -- issue
• Consider a simple device that accepts two High inputs H1 and H2, multiplexes them, encrypts them by xor’ing them with a one- time pad, outputs the other copy of the pad on H3, and outputs the ciphertext, which being encrypted with a cipher system giving perfect secrecy, is considered to be Low (output L) 14
• In isolation, this device is provably secure. But if feedback is permitted, then the output from H3 can be fed back into H2, with the result that the high input H1 now appears at the low output L. 15
Composability • Systems can become insecure when interconnected, or when feedback is added Ross Anderson
Composability • So nondeducibility doesn ’ t compose • Neither does noninterference • Many things can go wrong – clash of timing mechanisms, interaction of ciphers, interaction of protocols • Practical problem: lack of good security interface definitions (Keep in mind API failures) • Labels can depend on data volume, or even be non- monotone (e.g. Secret laser gyro in a Restricted inertial navigation set) Ross Anderson
Consistency • US approach (polyinstantiation): Cargo Destination Secret Missiles Iran Unclassified Spares Cyprus • UK approach (don ’ t tell low users): Cargo Destination Secret Missiles Iran Restricted Classified Classified Ross Anderson
Downgrading • A related problem to the covert channel is how to downgrade information • Analysts routinely produce Secret briefings based on Top Secret intelligence, by manual paraphrasing • Also, some objects are downgraded as a matter of deliberate policy – an act by a trusted subject • For example, a Top Secret satellite image is to be declassified and released to the press Ross Anderson
Examples of MLS Systems • SCOMP – Honeywell variant of Multics, launched 1983. Four protection rings, minimal kernel, formally verified hardware and software. Became the XTS-300 • Used in military mail guards • Motivated the ‘ Orange Book ’ – the Trusted Computer System Evaluation Criteria • First system rated A1 under Orange Book Ross Anderson
Examples of MLS Systems (2) • Blacker – series of encryption devices designed to prevent leakage from “ red ” to “ black ” . Very hard to accommodate administrative traffic in MLS! • Compartmented Mode Workstations (CMWs) – used by analysts who read Top Secret intelligence material and produce briefings at Secret or below for troops, politicians … Mechanisms allow cut -and-paste from L H, L L and H H but not H L Ross Anderson
Examples of MLS Systems (3) 22
Examples of MLS Systems (4) • LITS – RAF Logistics IT System – a project to control stores at 80 bases in 12 countries. Most stores ‘ Restricted ’ , rest ‘ Secret ’ , so two databases connected by a pump • Other application-level rules, e.g. ‘ don ’ t put explosives and detonators in the same truck ’ • Eventual solution: almost all stuff at one level, handle nukes differently Ross Anderson
Examples of MLS Systems (5) • DERA ’ s ‘ Purple Penelope ’ was an attempt to relax MLS to accountability for lower levels of stuff • Driver: people determined to use Office • Solution: wrapper around Windows that tracks current level using high watermark • Downgrading allowed, but system forces authentication and audit • Now called ‘ Sybard Suite ’ Ross Anderson
DG/UX System (Cf. Matt Bishop) • Provides mandatory access controls – MAC label identifies security level – Default labels, but can define others • Initially – Subjects assigned MAC label of parent • Initial label assigned to user, kept in Authorization and Authentication database – Object assigned label at creation • Explicit labels stored as part of attributes • Implicit labels determined from parent directory
MAC Regions A&A database , audit Administrati ve Region Hierarchy User data and applications User Region levels Site executables VP–1 Trusted data VP–2 Virus Prevention Re gion VP–3 Executables not part of the TCB VP–4 Executables part of the TCB Reserved for future use VP–5 Categories IMPL_HI is “maximum” (least upper bound) of all levels IMPL_LO is “minimum” (greatest lower bound) of all levels
Directory Problem • Process p at MAC_A tries to create file /tmp/x • /tmp/x exists but has MAC label MAC_B – Assume MAC_B dom MAC_A • Create fails – Now p knows a file named x with a higher label exists • Fix: only programs with same MAC label as directory can create files in the directory – Now compilation won’t work
Multilevel Directory • Directory with a set of subdirectories, one per label – Not normally visible to user – p creating /tmp/x actually creates /tmp/d/x where d is directory corresponding to MAC_A – All p ’s references to /tmp go to /tmp/d
Object Labels • Requirement: every file system object must have MAC label 1. Roots of file systems have explicit MAC labels • If mounted file system has no label, it gets label of mount point 2. Object with implicit MAC label inherits label of parent
Object Labels • Problem: object has two names – /x/y/z , /a/b/c refer to same object – y has explicit label IMPL_HI – b has explicit label IMPL_B • Case 1: hard link created while file system on DG/UX system, so … 3. Creating hard link requires explicit label • If implicit, label made explicit • Moving a file makes label explicit
Object Labels • Case 2: hard link exists when file system mounted – No objects on paths have explicit labels: paths have same implicit labels – An object on path acquires an explicit label: implicit label of child must be preserved so … 4. Change to directory label makes child labels explicit before the change
Object Labels • Symbolic links are files, and treated as such, so … 5. When resolving symbolic link, label of object is label of target of the link • System needs access to the symbolic link itself
Exercise I -- DAC Reading Suggestion: Section 7.3 of Fred Schneider, “ Access Control” Exercise : 7.1, 7.2, 7.3, 7.4, 7.6, 7.10, 7.13, 7.16 ( 9 problems) Submission date: 20 Feb 2017
The Biba Model • Contrary to Bell-LaPadula model, in Biba model information can only flow from a higher integrity class to a lower integrity class. • L is a linearly ordered set of integrity levels • C is a lattice of integrity categories • Integrity levels form a linear lattice in which each level represents the classification of integrity of information an object can contain or the clearance of a subject for modifying an object. • Integrity categories form a subset lattice and are used to enforce the need-to-have principle. • The lattice of security classes is L × C.
Recommend
More recommend