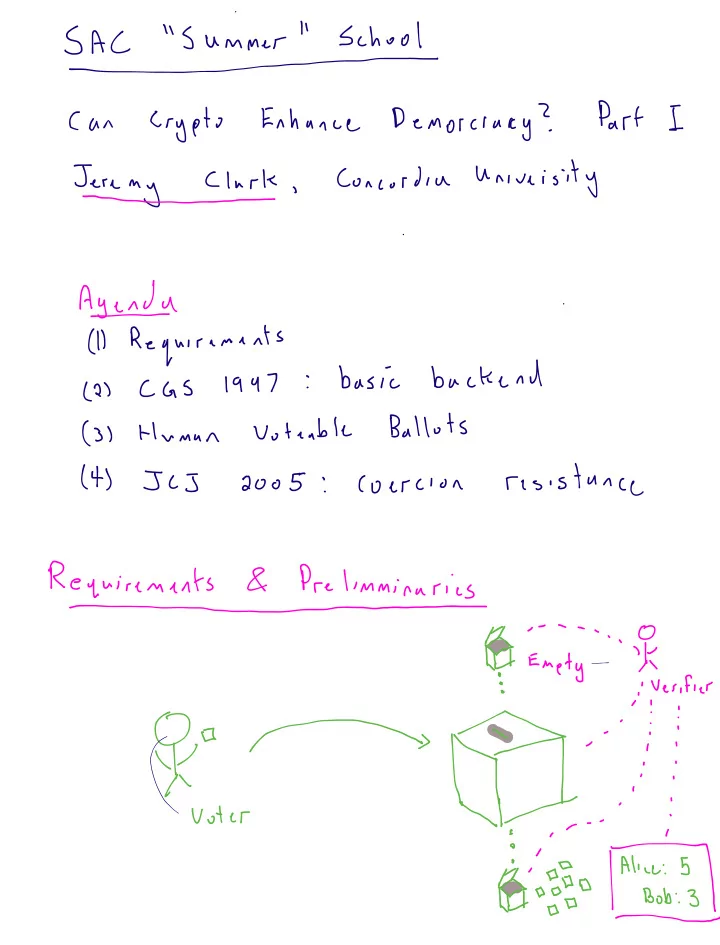

Sch SAC Su mmer Part I Enhance Can Democracy Crypto Concordia University Clerk Agenda 1 Requirements backend basic 1947 CGS 2 Ballots Votiable Human 3 t resistance JCJ 2005 Coercion Requirements Preliminaries Fi Enety i Verify i Oo ii Wi Voter i iii opium Bob 3_
Requirements 1 Verifiable Independently tally correct soundness integrity etc Ballot 2 secrecy receipt free resistant coercion etc REaLyIDEA Transcript Tully Tully cornet iii asf JCJ Anytime situational Others Dispute resolution intern accountability Indecent smeltaneity uperio Fairness running tally no U go Robust submit unconditional
to olbox Crypto 2 Kps Ring Homeomorphic encryption Signatures networks Mix anonymous MPC credentials commitments secret sharing choose cut oblivious transfer blind signatures etc etc v tiny 200 papers systems proposing CGS 1997_ Euroc yet schoenmakers Gennaro Cramer 00 it Eno v voter
Ev Enc pk r v public key out EA of 5 3 Distributed key General PKG on Threshold decryption CPA secure Additively Homomorphic atb b a r a r a a3 BGN Exponigand Rainier B.by I cos Co Ncaa I Co EA D b r 4 Yes 4 Mui 4 3 Nu
JT v encrypts 0 I or given Ency c ca nir Ngs gm y Cgr X 5 ca gv Lg c y iff DDH trek v Cg y or a g y a calgo Ghg DDH is tuple i c d Al O Teo.is ie Bob 0 Tsun n rt I I Tiso.is David Eo sd z am b Dawn C 4 Icehouse fixed
Alternative Sk 95 Chu81 Pika 3 Mixing B B Tis o o iii FE cos D sfhuff.ie MiX Perm write in Leven candidate Any No voter ZKP Summery Integrity Basic F secrecy BB randomize CD
Human Voteable The r X n ez wed i Bn I I counted as cast dispute overlay
TEE commitments Backend Different t Scantegrity c f Eperio slides Internet Voting Same requirements untrusted 1 platform JCT coercion resistance t Dus JCJOS Jacobsson WPES Jails Catalano civitas Principle Voters have real credential a to also vote They make fake can up a credential fakes Backend removes to knowing what they who f run they are are or
Voter Roster threshold in Voter A Oa whee Ob Ib OBIT voter B DencryptsiT Co do voter c Voter B's know I prrvnte.tt Fb Ttb Votes Eb true Alice Tteok Ob Bob Lda Tteok Alice
Roster snuff d d guff e or cob Coa s T com F Are fF Ob Bob Eb Alice EFFI E quality Tes Plaintext b b I Given and Alice a a I Bob threshold decryet nothing else learn a b iff 0 b a at b iff s fit o r Yemen Decrypt
Follow up Selections ABB 106 it Make linear MACS Aly d Panic passwords
Recommend
More recommend