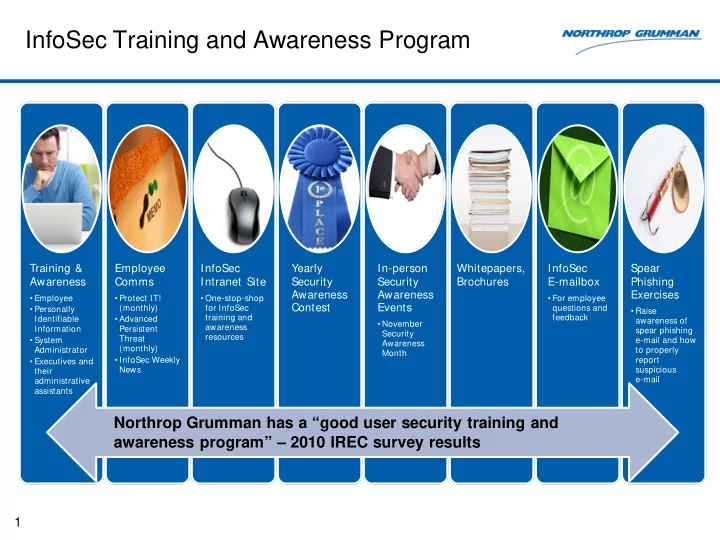

InfoSec Training and Awareness Program Training & Employee InfoSec Yearly In-person Whitepapers, InfoSec Spear Awareness Comms Intranet Site Security Security Brochures E-mailbox Phishing Awareness Awareness Exercises • Employee • Protect IT! • One-stop-shop • For employee Contest Events (monthly) for InfoSec questions and • Personally • Raise training and feedback Identifiable • Advanced awareness of • November awareness Information Persistent spear phishing Security resources Threat • System e-mail and how Awareness (monthly) Administrator to properly Month • InfoSec Weekly report • Executives and News suspicious their e-mail administrative assistants Northrop Grumman has a “good user security training and awareness program” – 2010 IREC survey results 1
Information Security Courses General User Role Based Base Course System Administrator Refresher Course Annual Mandatory Information Security Security Awareness Executives Awareness Video Modules Annual Mandatory Personally IT Governance, Introduction to the Identifiable Risk & ITGRC Information Required for Compliance Protection ITGRC Users Awareness 2
Employee Communications • “Protect IT!” branded monthly communication – Single topic; emphasis on protecting the company network and data • Advanced Persistent Threat monthly About Advanced Persistent communication Threat: – Single topic; emphasis on external threats to It’s not hacking. the company network and data It’s not spam. It’s espionage. • InfoSec Weekly News – Summaries and links to external and internal news articles related to information security • Partnerships with other internal organizations – Provide content for articles and presentations 3
Intranet Website Includes Links to: • Training and awareness materials – Internal and external articles – Security awareness courses – Videos and multimedia – Pages on key awareness topics • Information on major initiatives • Policies, procedures, and work instructions • Organizational and contact information 4
Yearly Security Awareness Contest • Ten Question Quiz – Questions created from information in the monthly communications • Links to communications provided as clues – Prizes awarded from imprinted giveaway inventory – Very popular - average 1,500 entries 5
In-Person Security Awareness Events • Partnership with sector Industrial Security departments • Company-sponsored “Security Awareness Month” every November • In-person communication with employees – Answer questions – Provide awareness materials – Offer simple games in which employees can be quizzed on security awareness and win imprinted giveaways 6
Brochures and Whitepapers • Brochures – Cover key awareness topics • E-mail guidelines • Internet safety • Incident response for system administrators – Easy to hand out at in-person events • Whitepapers – Cover topics more in-depth – Example: recommended guidelines for securing profiles on social media sites – Available on intranet site 7
Spear Phishing Exercises Those who click Those who submit “Suspicious” e- on the link see a information see a mail sent to target “registration” “notification” group webpage webpage • The e-mail includes • Registration page • Explains the security a link to an requests personal awareness exercise “unfamiliar” website information More on this later 8
9 Mark pages according to the proprietary level of information as described in Company Procedure J103 (or remove)
Spear Phishing Exercises 10 Mark pages according to the proprietary level of information as described in Company Procedure J103 (or remove)
Our Concerns Intellectual property theft Foreign and industrial espionage National security 11
Common Spear Phishing Attacks Username/password verification Program information request Industry conference information 12
The Problem with Spear Phishing 100% got through 13 Mark pages according to the proprietary level of information as described in Company Procedure J103 (or remove)
The Solution Security Awareness 14 Mark pages according to the proprietary level of information as described in Company Procedure J103 (or remove)
Spear Phishing Exercises 15
Objectives Test employees’ awareness of fraudulent e-mail messages Test support groups’ incident response process effectiveness 16
Phase 0: Initial Preparation • Who must approve a spear phishing exercise Approvals campaign? Policies and • Are relevant policies and procedures in place, and have they been communicated to employees? Procedures Remedial • What (if any) remedial action must be taken by employees who become “victims” of spear phishing Action Plan exercises? • Who should be included in the core implementation Core Team team? 17
Core Team CISO IT Executive Management •Lead overall effort •Notify IT executive management Project Lead •Send out pre- and post-exercise communications to management Training & Domain Name Active E-mail System Web Support Awareness Service (DNS) Directory (AD) •Establish fictitious •Create webpages •Create distribution list •Configure fictitious •Create/edit all domain •Create backend •Configure e-mail domain and redirect content – e-mail, environment database webpages, comms domain to internal •Configure/collect web •Configure/collect e- web server and scripts metrics mail metrics •Process target •Run end-to-end tests group feedback •Send out e-mails •Process metrics •Create final report Team restricted to a minimal number to prevent information leaks 18
Basic Spear Phishing Exercise Model Registration Notification E-mail Page Page • Contains spoofed • Clicking to this page • Explains the security sender e-mail means the target is awareness exercise address already “hooked” • Describes the clues • Includes embedded • Requests personal • Explains how URL to unfamiliar information suspicious e-mail website (a fictitious should be reported domain) • Provides e-mail • May contain other address for suspicious “clues” providing feedback 19
Exercise Phases Phase 1: Determination of premise Phase 2: Approval to proceed Phase 3: Preparation and testing Phase 4: Exercise implementation Phase 5: Reporting and lessons learned 20
Phase 1: Premise Who is the target group? How do we “hook” them? What clues should we include? 21
Premise Examples “Verify your network account or it will be suspended” “Last chance to receive a free encrypted flash drive” • “Register at our site to download this whitepaper and receive a free encrypted flash drive!” “Security Enhancement – Because of recent security threats, you must register at our site to continue to receive information from us” “New cyber security product – register for more information” 22
Phase 2: Acquire Approvals as Needed Draft E-mail / Draft Target Group Premise Webpages 23
Phase 3: Preparation and Testing Distribution • Review and remove specific names if necessary List •Purchase bulk mailer software •Establish fictitious domain names •If needed, configure perimeter e-mail environment to Infrastructure allow e-mails to bypass security controls •Turn on read receipts •Enable capture of e-mail replies and forwards • Registration page Webpage • Create backend database • Include input validation Creation • On notification page, include detailed descriptions of clues and references to relevant policies and procedures 24
Phase 3: Preparation and Testing, cont’d • Create pre- and post-exercise notifications • Create scripts for responses from support groups Communications • Ensure that users are not tipped off that a test is in progress • Determine what metrics are needed, and make sure all metrics collection is in place Metrics Collection • (More details on metrics are included on subsequent slides in this deck) • Verify that the entire process runs smoothly and End-to-End Tests that metrics data is captured correctly 25
Phase 4: Exercise Implementation Send out appropriate communications after the start of the test • Notify management that a spear phishing exercise is in progress (as needed) • Notify support organizations after they have gone through their initial incident response process Monitor metrics • Have set checkpoints throughout the day to ensure that metric data is being collected properly Determine when to shut down the exercise • One business day is usually sufficient for metrics Exercise may warrant sending a follow-up message to recipients for feedback • “Why did you click or not click?” Shut down the exercise • Disable links to webpages • Stop metrics collection 26
Phase 5: Reporting and Lessons Learned Description of test Presentation of metrics Target comments Lessons learned Recommendations Inclusion of screenshots of e-mail and webpages Summary slide of all spear phishing exercises 27
Recommend
More recommend