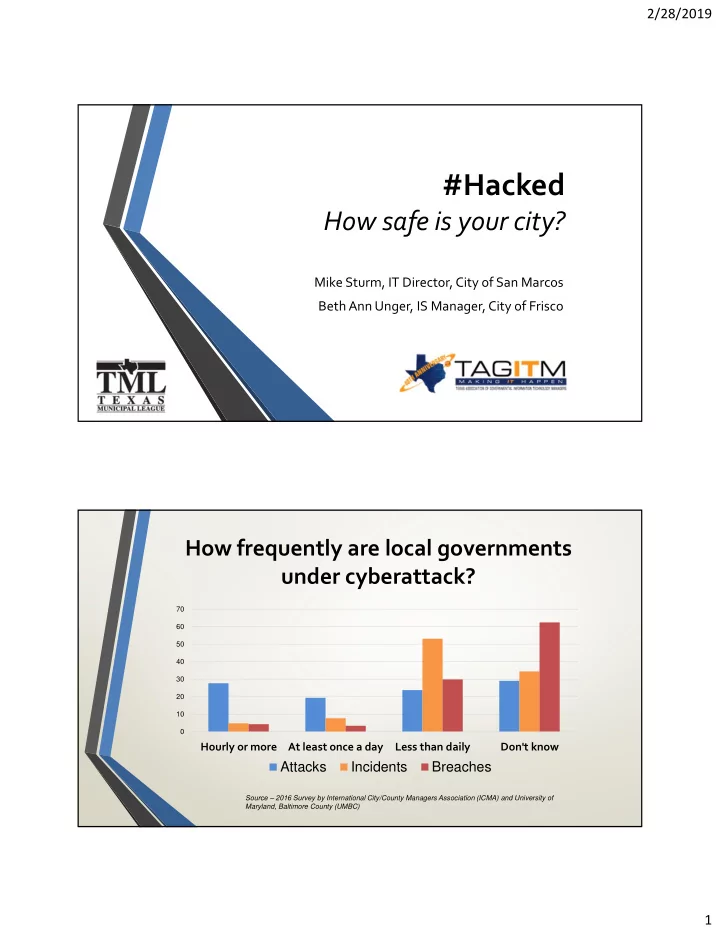

2/28/2019 #Hacked How safe is your city? Mike Sturm, IT Director, City of San Marcos Beth Ann Unger, IS Manager, City of Frisco How frequently are local governments under cyberattack? 70 60 50 40 30 20 10 0 Hourly or more At least once a day Less than daily Don't know Attacks Incidents Breaches Source – 2016 Survey by International City/County Managers Association (ICMA) and University of Maryland, Baltimore County (UMBC) 1
2/28/2019 How well prepared are local governments to respond to cyberthreats? Recover from ransomware Recover from exfiltration Prevent exfiltration Detect exfiltration Recover from breaches Prevent breaches Detect incidents Detect attacks 0 20 40 60 80 100 120 Very Good / Excellent Good Poor / Fair Don't Know Source – 2016 Survey by International City/County Managers Association (ICMA) and University of Maryland, Baltimore County (UMBC) Are Cities Really a Target? "Government organizations, in particular city governments, are prime targets; they not only process a lot of citizen and business data, but are also less secure as tighter budgets severely limit what IT updates they can carry out," Bittner said. "Bad actors have no doubt put the 89,000 local governments across the country in their cross-hairs . It is just a matter of time before many of these governments realize they’ve been hacked.“ Mike Bittner, Digital Security & Operations manager at The Media Trust 2
2/28/2019 In the News https://securitytoday.com/articles/2019/01/15/ransomware-attack-closes-down-texas-town.aspx In the News https://abc13.com/technology/houston-city-systems-were-hacked-twice/4925202/ 3
2/28/2019 In the News https://www.wired.com/story/atlanta-spent-26m-recover-from-ransomware-scare/ In the News https:// www.nbcnews.com/news/us-news/baltimore-s-911-emergency-system-hit-cyberattack-n860876 4
2/28/2019 In the News https://www.kbtx.com/content/news/City-of-Bryan-- 506137221.html In the News https://www.houstonchronicle.com/news/houston- texas/houston/article/Harris-County-looks-to-boost-cyber-security-after- 12524738.php 5
2/28/2019 In the News https://www.nytimes.com/2017/04/08/us/dallas-emergency-sirens-hacking.html In the News https://www.denverpost.com/2018/04/05/samsam-ransomware-cdot-cost/ 6
2/28/2019 This map issued by the Justice Department reveals the scope of the ransomware attack that struck the city of Atlanta government computers and more than 200 victims across the country, including hospitals, local governments and public institutions. SOURCE: U.S. Justice Department (The Atlanta Journal-Constitution) Two People Responsible for SamSam https://patch.com/colorado/denver/feds-indict-iranian-hackers-samsam- ransomware-cdot-others 7
2/28/2019 This map issued by the Justice Department reveals the scope of the ransomware attack that struck the city of Atlanta government computers and more than 200 victims across the country, including hospitals, local governments and public institutions. SOURCE: U.S. Justice Department (The Atlanta Journal-Constitution) Common Threats 8
2/28/2019 Single Layer of Deterrents Invaders 9
2/28/2019 14 Billion Spam messages are sent on a daily basis Hackers Work Fast Unfortunately, hackers work fast, too. According to May 2017 research by the Federal Trade Commission, it took only nine minutes before the hackers tried to access the information from a fake data breach. – Melanie Lockert , Credit Krama Inc 10
2/28/2019 According to industry analysts, cybercrimes are expected to cost $6 trillion annually worldwide by 2021... and 2019 could be the worst year yet for cyberbreaches. - Texas Government Insider, Strategic Partnerships, Inc. Categories of Phishing Messages Vishing Whaling Smishing Spear Phishing Search Engine Phishing PHARMING 11
2/28/2019 Strong Foundation CJIS Financial HIPAA Payroll PCI SCADA Homeland Security State and Federal regulations Human Factor Crypto locker W-2 Phishing Scam Cloud Services – Denial of Services Financial Phishing Scams Financial Fraud 12
2/28/2019 Smart Initiatives Layered Defense 13
2/28/2019 What’s the current status of the cybersecurity program in your local government? Developed security Acquired and Created a culture Obtained awareness training implemented of information cyber for workers and continuous security in your insurance contractors vulnerabilitymoni- government toring capabilities 54% 64% 63% 57% Used metrics Adopted a Established trusted Adopted a and testing to cybersecurity partnerships for cybersecurity document strategic plan Developed a information sharing framework, based on program cyber and response national standards 35% effectiveness response plan and guidelines 50% 25% 27% 42% In July-August 2018 PTI conducted a survey of local government I.T. executives representing cities and counties across the U.S. How Safe is Your City? Have your city adopted security policies that define acceptable behaviors and practices? Resources: • TML Risk Pool – city login required to access eRiskHub • https://www.sans.org/security-resources/policies/general 14
2/28/2019 How Safe is Your City? Does your city provide regular security awareness training? Resources: • www.knowbe4.com • www.sans.org • TML Risk Pool – city login required to access eRiskHub How Safe is Your City? Does your city conduct regular security assessment or audits? Resources: • Department of Homeland Security Services Catalog • Texas Department of Information Resources Managed Security Services 15
2/28/2019 How Safe is Your City? Does your city have Cyber Liability Insurance Coverage? Resources: • TML Risk Pool – provides coverage to Risk Pool members. Additional coverage available for a modest additional fee. It’s Not a Matter of If, but When • Security Can be Inconvenient - Empower your Information Technology (IT) staff to help protect you • If you don’t have internal IT resources, procure managed security services • Department of Homeland Security Services Catalog • Texas Department of Information Resources Managed Security Services • No amount of money or resources will guarantee your security • Identify your resources and have a plan before an incident occurs 16
2/28/2019 Additional Free Resources for IT Staff Center for Information Security (CIS) https://www.cisecurity.org/ • CIS 20 Critical Controls: https://www.cisecurity.org/controls/ • Benchmarks: Secure Configurations for 100+ Operating Systems and software • Hardened Images: https://www.cisecurity.org/hardened-images/ • CIS SecureSuite: https://www.cisecurity.org/cis-securesuite/ • Free Tools and Resources • CIS-CAT Pro – Vulnerability & Benchmark scanning tool Additional Free Resources for IT Staff MS-ISAC: https://www.cisecurity.org/ms-isac/ • 24/7 Security Operation Center • Incident Response Services • Cybersecurity Advisories and Notifications • Malicious Code Analysis Platform (MCAP) • Access to Cybersecurity Table-top Exercises • Vulnerability Management Program • Nationwide Cyber Security Review (NCSR) • Awareness and Education Materials 17
2/28/2019 Additional Free Resources for IT Staff • Cyber Training • Federal Virtual Training Environment (FedVTE) • (https://niccs.us-cert.gov/training/federal-virtual-training- environment-fedvte) • Texas Engineering Extension Service (TEEX) • (https://teex.org/Pages/Program.aspx?catID=607&courseTitle=Cy bersecurity) • DHS Catalog of free services: https://www.us- cert.gov/sites/default/files/c3vp/sltt/SLTT_Hands_On_Support.pdf #Hacked How safe is your city? Mike Sturm, IT Director, City of San Marcus Beth Ann Unger, IS Manager, City of Frisco 18
Recommend
More recommend