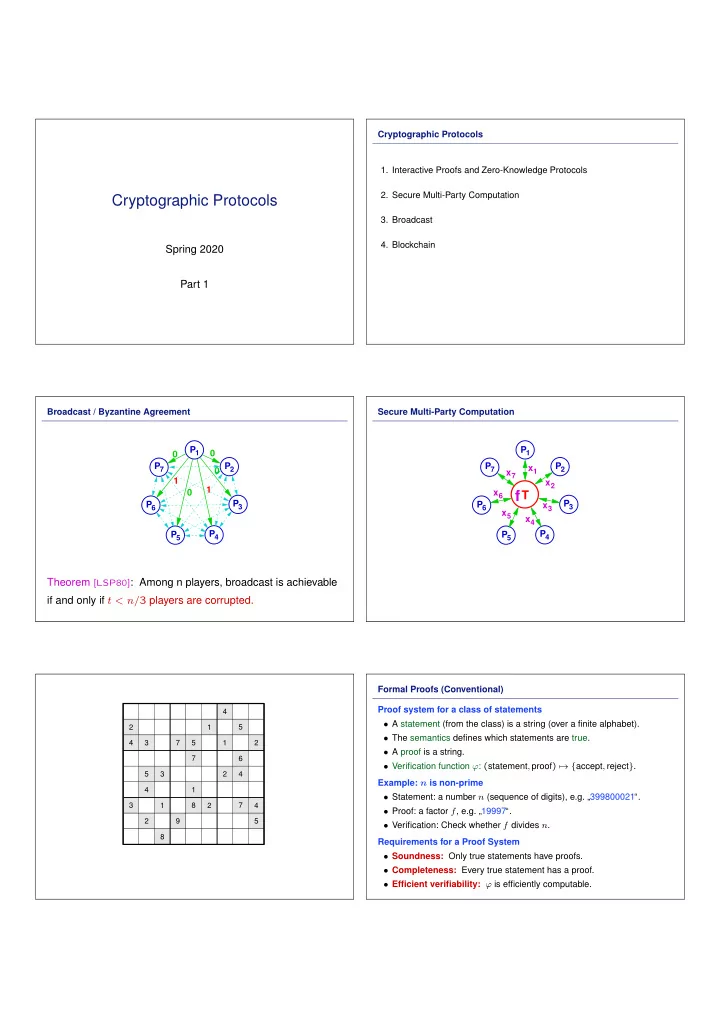

Cryptographic Protocols 1. Interactive Proofs and Zero-Knowledge Protocols 2. Secure Multi-Party Computation Cryptographic Protocols 3. Broadcast 4. Blockchain Spring 2020 Part 1 Broadcast / Byzantine Agreement Secure Multi-Party Computation P 1 P 1 0 0 P 7 P 2 P 7 P 2 x 1 0 x 7 1 x 2 1 0 x 6 f T P 3 P 3 P 6 P 6 x 3 x 5 x 4 P 5 P 4 P 5 P 4 Theorem [LSP80] : Among n players, broadcast is achievable if and only if t < n/ 3 players are corrupted. Formal Proofs (Conventional) Proof system for a class of statements 4 • A statement (from the class) is a string (over a finite alphabet). 2 1 5 • The semantics defines which statements are true. 4 3 7 5 1 2 • A proof is a string. 7 6 • Verification function ϕ : ( statement , proof ) �→ { accept , reject } . 5 3 2 4 Example: n is non-prime 4 1 • Statement: a number n (sequence of digits), e.g. ”399800021“. 3 1 8 2 7 4 • Proof: a factor f , e.g. ”19997“. 2 9 5 • Verification: Check whether f divides n . 8 Requirements for a Proof System • Soundness: Only true statements have proofs. • Completeness: Every true statement has a proof. • Efficient verifiability: ϕ is efficiently computable.
Proof System: Sudoku has Solution Efficient Primality Proof Good Proof System 4 2 1 5 An efficiently verifiable proof that n is prime: • Statement: 9-by-9 Matrix Z over { 1 , . . . , 9 , ⊥} . 4 3 7 5 1 2 • Proof: 9-by-9 Matrix X over { 1 , . . . , 9 } . 7 6 0. For small n (i.e., n ≤ T ), do table look-up (empty proof). 5 3 2 4 • Verification: 4 1 1. The list of distinct prime factors p 1 , . . . , p k of n − 1 . 3 1 8 2 7 4 1) 2 9 5 i =1 p α i � k ( n − 1 = i ) 2) 8 2. Number a such that Stupid Proof System a n − 1 ≡ 1 ( mod n ) • Statement: 9-by-9 Matrix Z over { 1 , . . . , 9 , ⊥} . • Proof: “” (empty string) and a ( n − 1) /p i �≡ 1 ( mod n ) • Verification: For all possible X , check if X is solution for Z . for 1 ≤ i ≤ k . → This is not a proof! 3. Primality proofs for p 1 , . . . , p k (recursion!). Two Types of Proofs Static Proofs vs. Interactive Proofs Static Proof Proofs of Statements: • Sudoku Z has a solution X . Prover P Verifier V • z is a square modulo m , i.e. ∃ x z = x 2 (mod m ) . knows statement s , knows statement s • The graphs G 0 and G 1 are isomorphic. proof p p ( s, p ) → { accept , reject } • The graphs G 0 and G 1 are non-isomorphic. ✲ • P = NP Interactive Proof Motivation for IP’s: Proofs of Knowledge: Prover P Verifier V 1. zero knowledge • I know a solution X of Sudoku Z . 2. more powerful • I know a value x such that z = x 2 knows statement s , knows statement s (mod m ) . m 1 3. applications • I know an isomorphism π from G 0 to G 1 . ✲ m 2 • I know a non-isomorphism between G 0 and G 1 ???? ✛ . . . • I know a proof for either P = NP or P � = NP . m ℓ • I know x such that z = g x . ( s, m 1 , . . . , m ℓ ) → { accept , reject } ✲ Often: Proof of knowledge → Proof of statement (knowledge exists) Interactive Proofs: Requirements (Informal) The Graph Isomorphism (GI) Problem G 0 G 1 • Completeness: If the statement is true [resp., the prover knows the 6 1 claimed information], then the correct verifier will always accept the 1 2 3 proof by the correct prover. 5 2 • Soundness: If the statement is false [resp., the prover does not know 5 the claimed information], then the correct verifier will accept the proof 4 6 4 3 only with negligible probability, independent of the prover’s strategy. 0 1 0 1 0 1 0 1 0 1 0 1 Desired Property: 1 0 1 1 1 0 1 0 1 0 0 1 0 1 0 0 1 1 0 1 0 0 1 1 • Zero-Knowledge: As long as the prover follows the protocol, the 1 1 0 0 1 0 1 0 0 0 1 0 0 1 1 1 0 0 0 0 1 1 0 1 verifier learns nothing but the fact that the statement is true [resp., that 1 0 1 0 0 0 1 1 1 0 1 0 the prover knows the claimed information].
Graph Isomorphism – One Round of the Protocol Graph-NON-Isomorphism – One Round of the Protocol Setting: Given two graphs G 0 and G 1 . Setting: Given two graphs G 0 and G 1 . Goal: Prove that G 0 and G 1 are isomorphic. Goal: Prove that G 0 and G 1 are not isomorphic. Peggy Vic Peggy Vic knows G 0 , G 1 , σ s.t. G 1 = σ G 0 σ − 1 knows G 0 and G 1 knows G 0 and G 1 knows G 0 and G 1 pick random permutation π b ∈ R { 0 , 1 } , π at random T T = π G 0 π − 1 ✲ T T = π G b π − 1 ✛ c c ∈ R { 0 , 1 } ✛ if T ∼ G 0 : r = 0 , c = 0 : ρ = π r r ? if T ∼ G 1 : r = 1 = b ✲ ρ ? c = 1 : ρ = πσ − 1 = ρ G 0 ρ − 1 c = 0 : T ✲ ? = ρ G 1 ρ − 1 c = 1 : T Fiat-Shamir – One Round of the Protocol Guillou-Quisquater – One Round of the Protocol Setting: m is an RSA-Modulus. Setting: m is an RSA-Modulus. Goal: Prove knowledge of a square root x of a given z ∈ Z ∗ Goal: Prove knowledge of an e -th root x of a given z ∈ Z ∗ m . m . Peggy Vic Peggy Vic knows x s.t. x 2 = z ( mod m ) knows x s.t. x e = z ( mod m ) knows z knows z k ∈ R Z ∗ k ∈ R Z ∗ m , m , t t t = k 2 t = k e ✲ ✲ c c c ∈ R { 0 , 1 } c ∈ R C ⊆ { 0 , . . . , e − 1 } ✛ ✛ r r r 2 ? r e ? r = k · x c = t · z c r = k · x c = t · z c ✲ ✲ Schnorr – One Round of the Protocol Setting: Cyclic group H = � h � , | H | = q prime. Goal: Prove knowledge of the discrete logarithm x of a given z ∈ H . Peggy Vic knows x ∈ Z q s.t. h x = z knows z k ∈ R Z q , t t = h k ✲ c c ∈ R C ⊆ Z q ✛ r h r ? = t · z c r = k + xc ✲
Recommend
More recommend