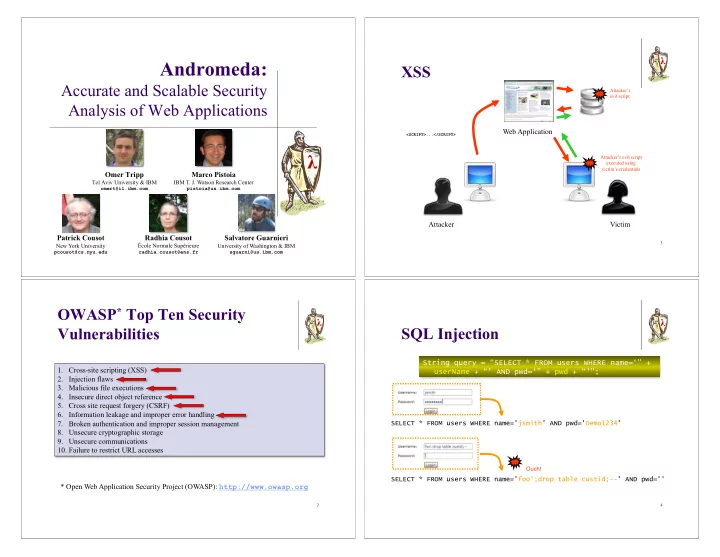

λ Andromeda: XSS Accurate and Scalable Security Attacker’s evil script Analysis of Web Applications Web Application <SCRIPT>...</SCRIPT> λ Attacker’s evil script executed using victim’s credentials Omer Tripp Marco Pistoia Tel Aviv University & IBM IBM T. J. Watson Research Center omert@il.ibm.com pistoia@us.ibm.com Attacker Victim Radhia Cousot Patrick Cousot Salvatore Guarnieri 3 New York University École Normale Supérieure University of Washington & IBM pcousot@cs.nyu.edu radhia.cousot@ens.fr sguarni@us.ibm.com OWASP * Top Ten Security λ λ Vulnerabilities SQL Injection String query = “SELECT * FROM users WHERE name=‘” + 1. Cross-site scripting (XSS) userName + “’ AND pwd=‘” + pwd + “’”; 2. Injection flaws 3. Malicious file executions 4. Insecure direct object reference 5. Cross site request forgery (CSRF) 6. Information leakage and improper error handling 7. Broken authentication and improper session management SELECT * FROM users WHERE name='jsmith' AND pwd='Demo1234' 8. Unsecure cryptographic storage 9. Unsecure communications 10. Failure to restrict URL accesses Ouch! SELECT * FROM users WHERE name='foo';drop table custid;--' AND pwd='' * Open Web Application Security Project (OWASP): http://www.owasp.org 2 4
λ λ Malicious File Executions Existing Static-Analysis Solutions Web application manage files in the file system Type systems: The name or contents of such files are often Complex, conservative, require code annotations obtained from user input Classic slicing: Maliciously crafted user inputs could cause the Has not been shown to scale to large applications while maintaining sufficient accuracy execution or deletion of security-sensitive files 5 7 Information Leakage and λ λ Improper Error Handling Motivation Web applications are large and complex Sound analyses If too precise, do not scale well If too imprecise, have too many false positives Unsound analyses Have false negatives Are often unstable (extra-sensitivity to program changes) 6
λ λ Intuition behind Andromeda Motivating Example Taint analysis can be public class Aliasing5 extends HttpServlet { protected void doGet(HttpServletRequest req, HttpServletResponse resp) treated as a demand- throws ServletException, IOException { driven problem StringBuffer buf = new StringBuffer("abc"); foo(buf, buf, resp, req); This enables lazy } computation of vulnerable void foo(StringBuffer buf, StringBuffer buf2, ServletResponse resp, information flows, instead ServletRequest req) throws IOException { String name = req.getParameter("name"); of eagerly computing a buf.append(name); complete data-flow PrintWriter writer = resp.getWriter(); writer.println(buf2.toString()); /* BAD */ solution } } λ λ Publications on Andromeda Contributions of Andromeda FASE 2013 – Andromeda algorithm Scalable and sound demand-driven taint analysis Omer Tripp, Marco Pistoia, Patrick Cousot, Radhia Cousot, Salvatore Guarnieri, “Andromeda: Accurate and Scalable Security Analysis of Web Applications” Modular analysis OOPSLA 2011 – Integration with Framework for Frameworks (F4F) Incremental analysis Manu Sridharan, Shay Artzi, Marco Pistoia, Salvatore Guarnieri, Omer Tripp, Ryan Berg, “F4F: Taint Analysis of Framework-based Web Applications” Framework and library support ISSTA 2011 (1) – Andromeda for JavaScript Salvatore Guarnieri, Marco Pistoia, Omer Tripp, Julian Dolby, Stephen Teilhet, Ryan Multiple language support (Java, .NET, Berg, “Saving the World Wide Web from Vulnerable JavaScript” ISSTA 2011 (2) – Andromeda as the basis for String Analysis (ACM SIGSOFT JavaScript) Distinguished Paper Award) Takaaki Tateishi, Marco Pistoia, Omer Tripp, “Path- and Index-sensitive String Analysis Inclusion in an IBM product: IBM Security based on Monadic Second-order Logic” AppScan Source IBM Journal on Research and Development 2013 – Permission analysis for Android applications Drago ș Sbîrlea, Michael G. Burke, Salvatore Guarnieri, Marco Pistoia, Vivek Sarkar, “Automatic Detection of Inter-application Permission Leaks in Android Applications”
λ λ High-level Algorithm Modularity of the Analysis Runs on data flow (def-to-use) Input: Web application plus supporting rules Produces and uses pre-compiled models {( Sources , Sinks , Sanitizers )} Build class hierarchy Format: <method, entry> <method, exit> Construct CHA-based call graph with intra- Example: procedural type-inference optimization <m, v2.f.g> <m, v1.h> Perform data-flow analysis (explained next) Report any flow from a source to a sink not intercepted by a sanitizer in the same rule A Novel Approach to λ λ Abstract Domain Taint Analysis Start from taint sources Consists of triplets: Propagate taint intra- Method where Static Single Assignment (SSA) variable is procedurally through def-to-use m1() defined Inter-procedurally propagate taint forward and record SSA variable ID constraints in callees Access path Record constraints on call sites, recursively (allows for Inputs form a lattice according to subsumption relation defined polymorphism) m2(p1, p2, p3) on access paths, e.g. : Resolve aliasing by going back o.* ≥ o.f.* ≥ o.f.g to allocation sites In the final constraint- The * symbol represents any feasible sub-path propagation graph , detect paths Array load/store semantics is applied to arrays, maps, session between sources and sinks not intercepted by sanitizers objects, etc. m3(q1, q2)
λ λ Modular Analysis Incremental Analysis Persist constraint edges at A taint constraint is an edge in the constraint-propagation library entrypoints m1() graph Constraint edges are The support graph records mapped to contexts how constraints were learned ( i.e. , based on which other During analysis time, the constraints) constraint edges specific m2(p1, p2, p3) Facts learned in a scope that to a particular context are underwent change are used Application transitively invalidated Summaries are source-, Preconditions recomputed Library sink- and sanitizer- Fixed-point analysis specific recommenced m3(q1, q2) λ λ Backward Propagation Integration with F4F Pushes constraints back to callers F4F (OOPSLA 2011) analyzes code and metadata of frameworks and represents them in artifacts Infinite context sensitivity written in an XML-like language Polymorphism with respect to taint Andromeda translates those artifacts into legal The constraint p1.f.g p2.h in m3 is Java code that – from a data-flow perspective – is propagated to m1 and m2 (and, recursively, to equivalent to the original framework code their callers) // ... New code is human-readable and reusable by x1.f.g x2.h // ... m3(y1,y2); m3(x1,x2); m1() m2() // ... // ... other analyzers y1.f.g y2.h New code is compiled and added to the analysis m3(p1,p2) scope
λ Experimental Results* Thank You! pistoia@us.ibm.com λ * More details in paper λ Conclusion The notorious scalability barrier finally lifted without compromising soundness Incremental analysis is a great promise for developers Production summaries already generated
Recommend
More recommend