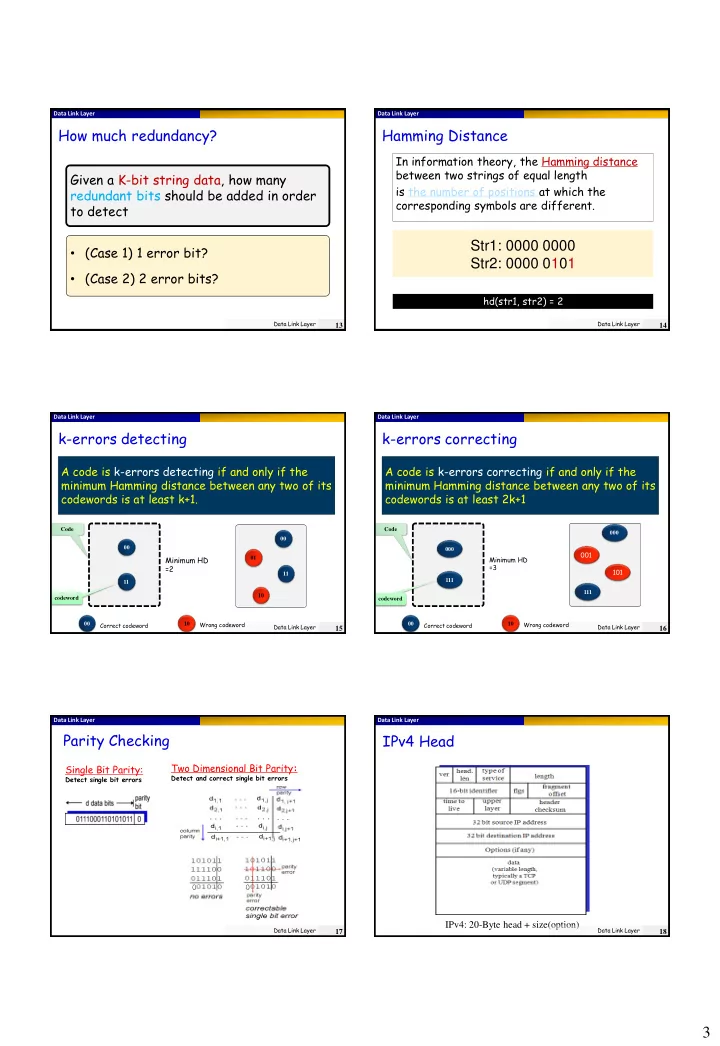

Data Link Layer Data Link Layer How much redundancy? Hamming Distance In information theory, the Hamming distance between two strings of equal length Given a K-bit string data, how many is the number of positions at which the redundant bits should be added in order corresponding symbols are different. to detect Str1: 0000 0000 • (Case 1) 1 error bit? Str2: 0000 0101 • (Case 2) 2 error bits? hd(str1, str2) = 2 Data Link Layer Data Link Layer 13 14 Data Link Layer Data Link Layer k-errors detecting k-errors correcting A code is k-errors detecting if and only if the A code is k-errors correcting if and only if the minimum Hamming distance between any two of its minimum Hamming distance between any two of its codewords is at least k+1. codewords is at least 2k+1 Code Code 000 00 00 000 001 Minimum HD 01 Minimum HD =3 =2 101 11 111 11 111 10 codeword codeword 00 Correct codeword 10 Wrong codeword 00 Correct codeword 10 Wrong codeword Data Link Layer Data Link Layer 15 16 Data Link Layer Data Link Layer Parity Checking IPv4 Head Two Dimensional Bit Parity : Single Bit Parity: Detect and correct single bit errors Detect single bit errors 0 0 IPv4: 20-Byte head + size(option) Data Link Layer Data Link Layer 17 18 3
Data Link Layer Data Link Layer Internet checksum (review) Next talk about CRC Goal: detect “errors” (e.g., flipped bits) in transmitted packet (note: used at transport layer only) Receiver: Sender: compute checksum of treat segment contents CRC is a popular error detecting received segment as sequence of 16-bit code! integers check if computed checksum equals checksum field value: checksum: addition (1’s Widely used in Ethernet complement sum) of NO - error detected segment contents YES - no error detected. But maybe errors sender puts checksum value into UDP checksum nonetheless? field Data Link Layer Data Link Layer 19 20 Data Link Layer Data Link Layer Foundation: Remainder computation Polynomial representation : 13 Numerical 5 B =b n-1 b n-2 …b 2 b 1 b 0 2 3 remainder: Polynomial: B(x)=b n-1 x n-1 + b n-2 x n-2 + … + b 2 x 2 + b 1 x 1 + b 0 Polynomial ( ) A x G x remainder: Q x ( ) R x ( ) ( ) Bit stream: Example: 1001 6 5 2 x x x 1 2 x x 1 Example: 3 2 1 0 1 0 0 1 x x x x 4 2 4 2 x x x 1 x x x 1 3 x 1 Data Link Layer Data Link Layer 21 22 Data Link Layer Data Link Layer CRC: Basic Idea CRC: Overview r B x ( ) x R x ( ) Q x ( ) G x ( ) Shared knowledge: G(x) ( ) ( ) ( ) ( ) A x ( ) Q x ( ) G x ( ) R x ( ) A x R x Q x G x Sender B(X) R(X) Given B(x) 6 5 2 x x x 1 Noisy compute R(x) 2 x x 1 4 2 4 2 channel x x x 1 x x x 1 Example: 6 5 2 B’(X) R’(X) Using B’(x) x x x 1 No remainder! R’(x)?=R * (x) 2 compute R*(x) x x 1 4 2 x x x 1 Receiver Data Link Layer Data Link Layer 23 24 4
Data Link Layer Data Link Layer How to compute R(x)? CRC Example Data: 101110 Generator: 1001 R(x): 011 Data plus redundancy to D . 2 r R = remainder[ ] send G 101110011 Data Link Layer Data Link Layer 25 26 Data Link Layer Data Link Layer Multiple Access Links and Protocols Link Layer Two types of “links”: Type 1: point-to-point 1 Link Layer and 5 Ethernet services PPP for dial-up access 6 Link-layer switches point-to-point link between Ethernet switch and host 2 Error detection Type 2: broadcast (shared wire or medium) 7 PPP and correction old-fashioned Ethernet 8 Link virtualization: 3 Multiple access Upstream TV Cable ATM protocols 802.11 wireless LAN 4 Link-layer addressing humans at a shared wire (e.g., cocktail party shared RF shared RF cabled Ethernet) (shared air, acoustical) (e.g., 802.11 WiFi) (satellite) Data Link Layer Data Link Layer 27 28 Data Link Layer Data Link Layer Multiple Access Protocols Ideal Multiple Access Protocol Model: Broadcast channel of rate R bps (1) single shared broadcast channel 1. when one node wants to transmit, it can send at (2) two or more simultaneous transmissions by nodes: rate R. interference 2. when M nodes want to transmit, each can send at collision if node receives two or more signals at the same time average rate R/M multiple access protocol (MAC) impossible Distributed algorithm that determines how nodes share channel, i.e., determine when node can transmit 3. fully decentralized: Assumption: communication about channel sharing must no special node to coordinate transmissions use channel itself! no synchronization of clocks, slots no out-of-band channel for coordination 4. simple Data Link Layer Data Link Layer 29 30 5
Data Link Layer Data Link Layer MAC Protocols: a taxonomy Channel Partitioning MAC protocols: TDMA Three broad classes: TDMA: time division multiple access Channel Partitioning access to channel in "rounds" static divide channel into smaller “pieces” (time each station gets fixed length slot (length = pkt slots, frequency, code) trans time) in each round allocate piece to node for exclusive use Random Access unused slots go idle channel not divided, allow collisions example: 6-station LAN, 1,3,4 have pkt, slots 2,5,6 “recover” from collisions idle “Taking turns” dynamic 6-slot nodes take turns frame nodes with more to send can take longer 1 3 4 1 3 4 turns Data Link Layer Data Link Layer 31 32 Data Link Layer Data Link Layer FDMA vs. TDMA Channel Partitioning MAC protocols: FDMA FDMA: frequency division multiple access channel spectrum divided into frequency bands each station assigned fixed frequency band unused transmission time in frequency bands go idle example: 6-station LAN, 1,3,4 have pkt, frequency bands 2,5,6 idle frequency bands FDM cable Data Link Layer Data Link Layer 33 34 Data Link Layer Data Link Layer Frequency Division Multiplexing Wavelength Division Multiplexing Wavelength division multiplexing. (a) The original bandwidths. (b) The bandwidths raised in frequency. (b) The multiplexed channel. Data Link Layer Data Link Layer 35 36 6
Data Link Layer Data Link Layer Random Access Protocols Pure (unslotted) ALOHA unslotted Aloha : simple, no synchronization When node has packet to send when frame first arrives transmit at full channel data rate R. no a priori coordination among nodes transmit immediately two or more transmitting nodes ➜ “collision”, collision probability increases: random access MAC protocol specifies: frame sent at t 0 collides with other frames sent in [t 0 -1,t 0 +1] how to detect collisions how to recover from collisions (e.g., via delayed retransmissions) Examples of random access MAC protocols: ALOHA slotted ALOHA CSMA, CSMA/CD, CSMA/CA Data Link Layer Data Link Layer 37 38 Data Link Layer Data Link Layer Pure Aloha efficiency Slotted ALOHA P(success by given node) Assumptions: Operation: all frames same size when node obtains fresh = P(node transmits) . frame, transmits in next time divided into equal P(no other node transmits in [p 0 -1,p 0 ] . slot size slots (time to P(no other node transmits in [p 0 -1,p 0 ] transmit 1 frame) if no collision: node can = p . (1-p) N-1 . (1-p) N-1 send new frame in next nodes start to transmit slot = p . (1-p) 2(N-1) only slot beginning if collision: node nodes are synchronized retransmits frame in if 2 or more nodes … choosing optimum p and then letting n -> infty ... each subsequent slot transmit in slot, all with prob. p until nodes detect collision = 1/(2e) = 0.18 success Data Link Layer Data Link Layer 39 40 Data Link Layer Data Link Layer Slotted ALOHA Slotted Aloha efficiency max efficiency: find Efficiency : long-run fraction of successful slots p* that maximizes Np(1-p) N-1 (many nodes, all with many frames to send) for many nodes, take limit of Np*(1-p*) N-1 suppose: N nodes with as N goes to infinity, Pros Cons many frames to send, gives: collisions, wasting slots single active node can each transmits in slot Max efficiency = 1/e = 0.37 idle slots continuously transmit with probability p at full rate of channel nodes may be able to prob that given node At best: channel detect collision in less highly decentralized: has success in a slot = used for useful ! than time to transmit only slots in nodes transmissions 37% p(1-p) N-1 packet need to be in sync prob that any node has of time! clock synchronization a success = Np(1-p) N-1 simple Data Link Layer Data Link Layer 41 42 7
Recommend
More recommend