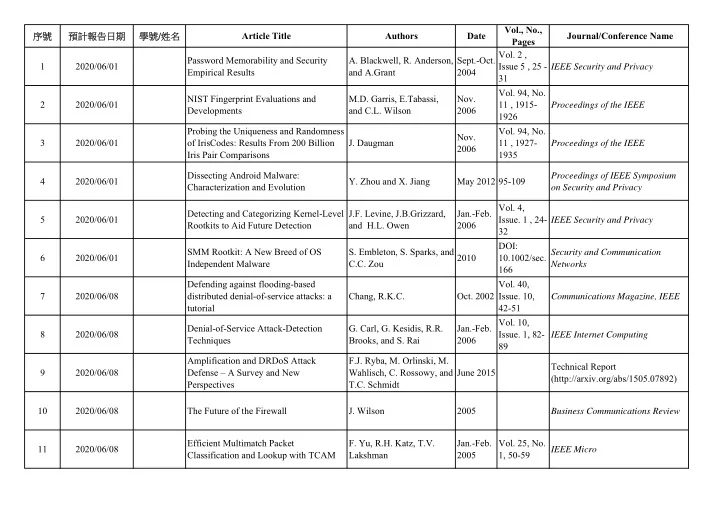

Vol., No., Article Title Authors Date Journal/Conference Name 序號 預計報告日期 學號/姓名 Pages Vol. 2 , Password Memorability and Security A. Blackwell, R. Anderson, Sept.-Oct. 1 2020/06/01 Issue 5 , 25 - IEEE Security and Privacy Empirical Results and A.Grant 2004 31 Vol. 94, No. NIST Fingerprint Evaluations and M.D. Garris, E.Tabassi, Nov. 2 2020/06/01 11 , 1915- Proceedings of the IEEE Developments and C.L. Wilson 2006 1926 Probing the Uniqueness and Randomness Vol. 94, No. Nov. 3 2020/06/01 of IrisCodes: Results From 200 Billion J. Daugman 11 , 1927- Proceedings of the IEEE 2006 Iris Pair Comparisons 1935 Dissecting Android Malware: Proceedings of IEEE Symposium 4 2020/06/01 Y. Zhou and X. Jiang May 2012 95-109 Characterization and Evolution on Security and Privacy Vol. 4, Detecting and Categorizing Kernel-Level J.F. Levine, J.B.Grizzard, Jan.-Feb. 5 2020/06/01 Issue. 1 , 24- IEEE Security and Privacy Rootkits to Aid Future Detection and H.L. Owen 2006 32 DOI: SMM Rootkit: A New Breed of OS S. Embleton, S. Sparks, and Security and Communication 6 2020/06/01 2010 10.1002/sec. Independent Malware C.C. Zou Networks 166 Defending against flooding-based Vol. 40, 7 2020/06/08 distributed denial-of-service attacks: a Chang, R.K.C. Oct. 2002 Issue. 10, Communications Magazine, IEEE tutorial 42-51 Vol. 10, Denial-of-Service Attack-Detection G. Carl, G. Kesidis, R.R. Jan.-Feb. 8 2020/06/08 Issue. 1, 82- IEEE Internet Computing Techniques Brooks, and S. Rai 2006 89 Amplification and DRDoS Attack F.J. Ryba, M. Orlinski, M. Technical Report 9 2020/06/08 Defense – A Survey and New Wahlisch, C. Rossowy, and June 2015 (http://arxiv.org/abs/1505.07892) Perspectives T.C. Schmidt 10 2020/06/08 The Future of the Firewall J. Wilson 2005 Business Communications Review Efficient Multimatch Packet F. Yu, R.H. Katz, T.V. Jan.-Feb. Vol. 25, No. 11 2020/06/08 IEEE Micro Classification and Lookup with TCAM Lakshman 2005 1, 50-59
Scalable Packet Classification by TCAM Vol. 16, No. 12 2020/06/08 C.L. Lee and P.C. Wang 2007 Journal of High Speed Networks Entry Encryption Algorithm 3, 275-28 Performance Improvement of Two- P.C. Wang, C.L. Lee, C.T. Aug. Vol. 15, No. IEEE/ACM Transactions on 13 2020/06/15 Dimensional Packet Classification by Chan, and H.Y. Chang 2007 4, 906-917 Networking Filter Rephrasing Packet Classification Algorithms From Y. Qi, L. Xu, B. Yang, Y. 14 2020/06/15 2009 648-656 Proceedings of IEEE INFOCOM Theory to Practice Xue, and J. Li Vol. E93-D, Packet Classification with Hierarchical C.L. Lee, C.T. Chan, and IEICE Transactions on 15 2020/06/15 May 2010 No. 5, 1117- Cross-Producting P.C. Wang Information and Systems 1126 Fast TCAM-based Multi-match Packet Jun. 2018 Vol. 4, Issue IEEE Transactions on Multi-Scale 16 2020/06/15 H.T. Lin and P.C. Wang Classification Using Discriminators 4, 686-697 Computing Systems Detecting and resolving packet filter A. Hari, S. Suri, and G. Mar. 17 2020/06/15 1203-1212 Proceedings of IEEE INFOCOM conflicts Parulkar 2010 Fast and Scalable Conflict Detection for F. Baboescu and G. Aug. Vol. 42, No. 18 2020/06/15 Computer Networks Packet Classifier Varghese 2003 6, 717-735 A Topology-based Conflict Detection S. Thanasegaran, Y. Yin, International Journal of Nov. Vol. 4, No. 19 2020/06/22 System for Firewall Policies Using Bit- Y. Tateiwa, Y. Katayama, Communications, Network and 2011 11, 683-695 vector-based Spatial Calculus and N. Takahashi System Sciences Vol. E95-D, An Efficient Conflict Detection C.L. Lee, G.Y. Lin, and IEICE Transactions on 20 2020/06/22 Feb. 2012 No. 2, 472- Algorithm for Packet Filters Y.C. Chen Information and Systems 479 Vol. 11, No. Fast and Complete Conflict Detection 21 2020/06/22 C.Y. Lai and P.C. Wang Jun. 2017 2, 1137- IEEE Systems Journal for Packet Classifiers 1148 Vol. 17, Defending Yourself: The Role of J. McHugh, A.Christie, and Sep.-Oct. 22 2020/06/22 Issue. 5, 42- IEEE Software Intrusion Detection Systems J. Allen 2000 51 Proceedings of Computer Security 23 2020/06/22 Offloading IDS computation to the GPU Jacob N and Brodley C 2006 371–380 Applications Conference
Gnort: High Performance Network G. Vasiliadis, S. Antonatos, Proceedings of International 24 2020/06/22 Intrusion Detection Using Graphics M. Polychronakis, E.P. 2008 116–134 Symposium on Recent Advances in Processors Markatos, and S. Iasnnidis Intrusion Detection Hierarchical Multi-Pattern Matching Vol. 178, T.F. Sheu, N.F. Huang, and 25 2020/06/29 Algorithm for Network Content 2008 Issue 14, Information Science H.P. Lee Inspection 2880-2898 An Efficient Pre-filtering Mechanism for C. Wu, J. Yin, Z. Cai, E. 26 2020/06/29 Parallel Intrusion Detction Based on 2009 298–305 Security Technology Zhu , and J. Cheng Many-core GPU G. Vasiliadis, M. Proceedings of ACM Conference MIDeA: A Multi-Parallel Intrusion 27 2020/06/29 Polychronakis, and S. 2011 297–308 on Computer and Communication Detection Architecture Ioannidis Security Robust and Scalable String Pattern Y.H. Yang and V.K. Vol. 25, IEEE Transactions on Parallel and 28 2020/06/29 Matching for Deep Packet Inspection on 2013 Prasanna 2283-2292 Distributed Systems Multicore Processors A Hybrid CPU/GPU Pattern-Matching C.L. Lee, Y.S. Lin, and 29 2020/06/29 Oct. 2015 PLoS One Algorithm for Deep Packet Inspection Y.C. Chen 評分原則 : 1. 報告內容 : 60% ( 重點為是否能清楚描述論文的內容 ) 2. 投影片 : 20% ( 重點在是否能有效呈現論文內容,並配合報告內容 ) 3. 時間控制 : 10% ( 報告時間為 20 分鐘,誤差在 +- 2 分鐘內不扣分,超過誤差範圍每分鐘扣 1 分 ) 4. 同學互評 : 10% 5. 報告當日上午 10 點前必須將投影片檔案上傳至 E-Learning 系統 否則每遲交一天扣總分 5 分,投影片檔案請以學號做為檔名,學號英文字母請使用大寫。 6. 需將投影片使用 A4 紙張以雙面且每面 4 張投影片的方式列印,並於報告時繳交,否則扣總分 10 分。 7. 若無法於預訂時間報告,可與其他同學交換報告時間,但報告論文亦必須同時交換, 且於報告日期 3 天前與同意交換之同學親自找助教登記。未按規定者,總分扣 20 分。 8. 報告當日若未準時至教室報告,但仍於當日報告者,扣總分 10 分。
Recommend
More recommend