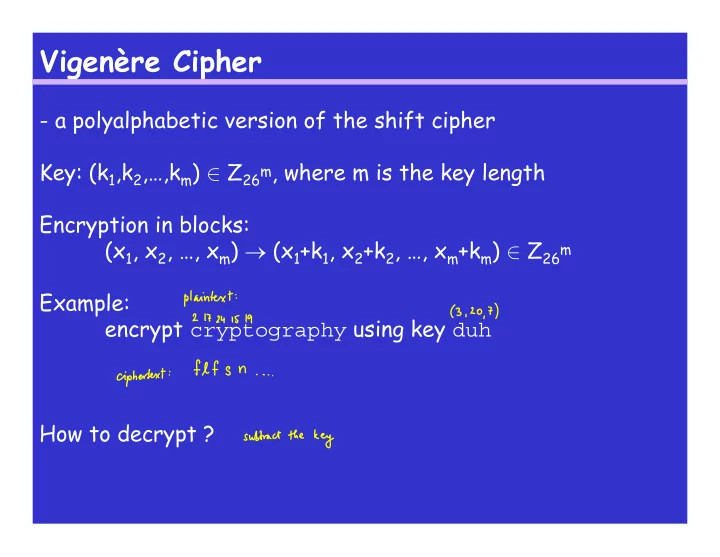

Vigenère Cipher - a polyalphabetic version of the shift cipher Key: (k 1 ,k 2 ,…,k m ) ∈ Z 26m , where m is the key length Encryption in blocks: (x 1 , x 2 , …, x m ) → (x 1 +k 1 , x 2 +k 2 , …, x m +k m ) ∈ Z 26m Example: encrypt cryptography using key duh How to decrypt ?
Cryptanalysis of the Vigenère Cipher - if m small: - exhaustive search might be ok - how many keys ? - known plaintext attack: easy / hard ? - ciphertext-only attack - long thought safe against this attack - what do we know now ? - first find the key length m: counting coincidences (see Section 2.3.1), Kasiski test, index of coincidence
Kasiski test - two identical segments of ciphertext of length ≥ 3 likely correspond to the same segments of plaintext - if two such segments are δ positions apart, what is the likely relationship between m and δ ? Example (Stinson, Exercise 1.21 1(b) using Vigenère): KCCPKBGUFDPHQTYAVINRRTMVGRKDNBVFDETDGILTXRGUD DKOTFMBPVGEGLTGCKQRACQCWDNAWCRXIZAKFTLEWRPTYC QKYVXCHKFTPONCQQRHJVAJUWETMCMSPKQDYHJVDAHCTRL SVSKCGCZQQDZXGSFRLSWCWSJTBHAFSIASPRJAHKJRJUMV GKMITZHFPDISPZLVLGWTFPLKKEBDPGCEBSHCTJRWXBAFS PEZQNRWXCVYCGAONWDDKACKAWBBIKFTIOVKCGGHJVLNHI FFSQESVYCLACNVRWBBIREPBBVFEXOSCDYGZWPFDTKFQIY CWHJVLNHIQIBTKHJVNPIST Trigram HJV: positions 108, 126, 264, 318, and 330. Conclusions ?
Index of Coincidence Reasoning: Let y = y 1 y 2 …y n be the ciphertext. For a given m, we define these substrings of y: y 1 = y 1 y m+1 y 2m+1 … y 2 = y 2 y m+2 y 2m+2 … : : : : y m = y m y 2m y 3m … If m is divisible by the key length, what property do we expect from these strings ? If m not divisible by the key length, then what ?
Index of Coincidence Example: For m=6 and the text from slide 3: y 1 = KGQNGVGGTGCQWAWQHNJEPJTKQFWAP … y 2 = CUTRRFIUFEKCCKRKKCVTKVRCDRSFR … y 3 = CFYRKDLDMGQWRFPYFQAMQDLGZLJSJ … y 4 = PDATDETDBLRDXTTVTQJCDASCXSTIA … Y 5 = KPVMNTXKPTANILYXPRUMYHVZGWBAH … Y 6 = BHIVBDROVGCAZECCOHWSHCSQSCHSK …
Index of Coincidence Def: Suppose that x = x 1 x 2 …x n is a string of n alphabetic characters. The index of coincidence of x , denoted I c ( x ), is defined to be the probability that two random elements of x are identical. Thus, I c ( x ) = where f i , i ∈ Z 26 is the number of occurrences of the symbol i in the string x .
Index of Coincidence For English text, the index of coincidence is approximately ∑ i=025 p i2 = 0.066 where p i is the probability of occurrence of symbol i (see Table 2.1). What is the index of coincidence of shift ciphertext, if plaintext is English ? For a completely random text, the index of coincidence is approximately Idea: find m so that the index of coincidence close to 0.066
Index of Coincidence Example from slide 3: m = 1: 0.041 m = 2: 0.038, 0.047 m = 3: 0.056, 0.048, 0.048 m = 4: 0.037, 0.042, 0.037, 0.050 m = 5: 0.043, 0.043, 0.031, 0.035, 0.043 m = 6: 0.063, 0.084, 0.049, 0.065, 0.042, 0.071 m = 7: 0.031, 0.044, 0.043, 0.038, 0.044, 0.044, 0.041 What m do we choose ?
Computing the Key - need to find (k 1 ,k 2 ,…,k m ) - let f i be the number of occurrences of symbol i, i ∈ Z 26 in y i ; let n’ be the length of y i Idea 1: use frequencies to determine k i Idea 2: - more precise but needs more computation - for a shift g, we expect the normalized frequencies (divide by n’) f g /n’, f g+1 /n’, f g+2 /n’, …, f g+25 /n’ to be “close to” p 0 ,p 1 ,…,p 25 iff g = k i
Computing the Key Idea 2, continued: - let M g = ∑ i=025 p i f g+i /n’ - if g=k i , what do we expect M g to be ? - if g ≠ k i , what do we expect M g to be ? - algorithm to determine the key ?
Recommend
More recommend