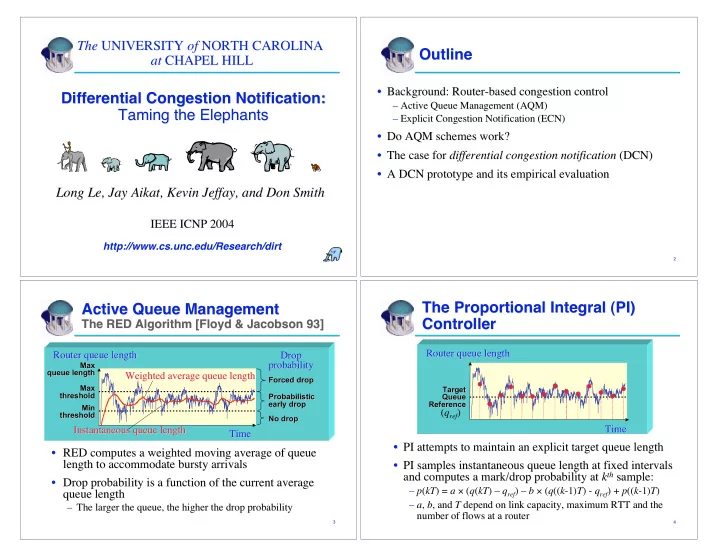

The UNIVERSITY UNIVERSITY of of NORTH CAROLINA NORTH CAROLINA The Outline Outline at at CHAPEL HILL CHAPEL HILL • Background: Router-based congestion control Background: Router-based congestion control • Differential Congestion Notification: Differential Congestion Notification: – Active Queue Management (AQM) – Active Queue Management (AQM) Taming the Elephants Taming the Elephants – – Explicit Congestion Notification (ECN) Explicit Congestion Notification (ECN) • • Do AQM schemes work? Do AQM schemes work? • The case for The case for differential congestion notification differential congestion notification (DCN) (DCN) • • A DCN prototype and its empirical evaluation A DCN prototype and its empirical evaluation • Long Le, Jay Aikat, Kevin Jeffay, and Don Smith Long Le, Jay Aikat, Kevin Jeffay, and Don Smith IEEE ICNP 2004 IEEE ICNP 2004 http://www.cs.unc.edu/Research/dirt 1 1 2 2 The Proportional Integral (PI) The Proportional Integral (PI) Active Queue Management Active Queue Management Controller Controller The RED Algorithm [Floyd & Jacobson 93] The RED Algorithm [Floyd & Jacobson 93] Router queue length Router queue length Router queue length Drop Router queue length Drop Max probability probability Max queue length queue length Weighted average queue length Weighted average queue length Forced drop Forced drop Max Max Target Target threshold threshold Probabilistic Probabilistic Queue Queue early drop early drop Reference Reference Min Min ( q ref ) threshold threshold No drop No drop Time Time Instantaneous queue length Instantaneous queue length Time Time • PI attempts to maintain an explicit target queue length PI attempts to maintain an explicit target queue length • • RED computes a weighted moving average of queue • RED computes a weighted moving average of queue length to accommodate bursty bursty arrivals arrivals length to accommodate • PI samples instantaneous queue length at fixed intervals PI samples instantaneous queue length at fixed intervals • and computes a mark/drop probability at k k th th sample: sample: and computes a mark/drop probability at • Drop probability is a function of the current average Drop probability is a function of the current average • – p ( kT ) = a � ( q ( kT ) – q ref ) – b � ( q (( k -1) T ) - q ref ) + p (( k -1) T ) queue length queue length – a – a , , b b , and , and T T depend on link capacity, maximum RTT and the depend on link capacity, maximum RTT and the – The larger the queue, the higher the drop probability – The larger the queue, the higher the drop probability number of flows at a router number of flows at a router 3 3 4 4
Explicit Congestion Notification Explicit Congestion Notification Do AQM Schemes Work? Do AQM Schemes Work? Overview Overview Evaluation of ARED, PI, and REM Evaluation of ARED, PI, and REM Sched- P 1 P 2 P 3 P 4 P 5 P 6 P 7 P 8 P 9 uler • “ “The Effects of Active Queue Management on Web The Effects of Active Queue Management on Web • data ACK Performance Performance” ” [SIGCOMM 2003]. When user response [SIGCOMM 2003]. When user response data ACK data ACK data ACK data ACK data ACK data ACK times are important performance metrics: times are important performance metrics: data ACK – Without ECN, PI results in a modest performance – Without ECN, PI results in a modest performance Router Router improvement over drop-tail and other AQM schemes improvement over drop-tail and other AQM schemes – With ECN, both PI and REM provide significant performance – With ECN, both PI and REM provide significant performance • • Set a bit in a packet Set a bit in a packet’ ’s header and forward towards s header and forward towards improvement over drop-tail improvement over drop-tail the ultimate destination the ultimate destination • A receiver recognizes the marked packet and sets • A receiver recognizes the marked packet and sets a corresponding bit in the next outgoing ACK a corresponding bit in the next outgoing ACK • When a sender receives an ACK with ECN it When a sender receives an ACK with ECN it • invokes a response similar to that for packet loss. invokes a response similar to that for packet loss. 5 5 6 6 Evaluation of ARED, PI, and REM Evaluation of ARED, PI, and REM Outline Outline Experimental Results – Experimental Results – 98% Load 98% Load • • Background: Router-based congestion control Background: Router-based congestion control 50% of 50% of – Active Queue Management Active Queue Management – responses… responses… – Explicit Congestion Notification Explicit Congestion Notification – Performance Performance • • Do AQM schemes work? Do AQM schemes work? gain with ECN gain with ECN • Analysis of AQM performance Analysis of AQM performance • Performance gain of Performance gain of PI over drop-tail – The case for The case for differential congestion notification differential congestion notification (DCN) (DCN) – PI over drop-tail • A DCN prototype and its empirical evaluation • A DCN prototype and its empirical evaluation …complete in …complete in 125 ms or less 125 ms or less 7 7 8 8
The Structure of Web Traffic The Structure of Web Traffic The Structure of Web Traffic The Structure of Web Traffic Percent of bytes transferred by response sizes Distribution of response sizes Percent of bytes transferred by response sizes Distribution of response sizes 100 …account for …account for 90 only 20% of all only 20% of all 80 bytes transferred 87% of bytes transferred 87% of 70 responses… responses… 60 50 40 30 …are 10K But objects that are …are 10K But objects that are bytes or less 20 10K bytes or smaller… bytes or less 10K bytes or smaller… 10 0 1 10 100 1K 10K 100K 1M 10M 100M 1G 100 1K 10K 100K 1M 10M 100M 1G 9 9 10 10 Realizing Differential Notification Realizing Differential Notification Classifying Flows Classifying Flows Issues and approach Issues and approach A score-boarding approach A score-boarding approach HB SB • How to identify packets belonging to long-lived, high • How to identify packets belonging to long-lived, high Low-bandwidth flows bandwidth flows with minimal state? bandwidth flows with minimal state? Flow Scheduler P 1 P 2 P 3 Scheduler – – Adopt the Adopt the Estan Estan & Varghese flow filtering scheme & Varghese flow filtering scheme classifier PI-like developed for traffic accounting [SIGCOMM 2002] developed for traffic accounting [SIGCOMM 2002] Controller High-bandwidth flows • How to determine when to signal congestion (by • How to determine when to signal congestion (by • Use two hash tables (hash keys are formed by IP addressing 4- Use two hash tables (hash keys are formed by IP addressing 4-tuple tuple • dropping packets)? dropping packets)? plus protocol number): plus protocol number): – A – A “ “suspect suspect” ” flow table HB ( flow table HB (“ “high-bandwidth high-bandwidth” ”) and ) and – Use a PI-like scheme [ Use a PI-like scheme [Infocom Infocom 2001] 2001] – – – A per-flow packet count table SB ( A per-flow packet count table SB (“ “scoreboard scoreboard” ”) ) • • Arriving packets from flows in HB are subject to dropping Arriving packets from flows in HB are subject to dropping • Differential treatment of flows an old idea: Differential treatment of flows an old idea: • • Arriving packets from other flows are inserted into SB and tested to • Arriving packets from other flows are inserted into SB and tested to – CHOKe CHOKe – AFD AFD – RIO-PS RIO-PS – FRED – FRED – – – determine if the flow should be considered high-bandwidth determine if the flow should be considered high-bandwidth – SRED SRED – SFB – SFB – – RED-PD RED-PD – … – … – – – Use a simple packet count threshold for this determination Use a simple packet count threshold for this determination 11 11 12 12
Recommend
More recommend