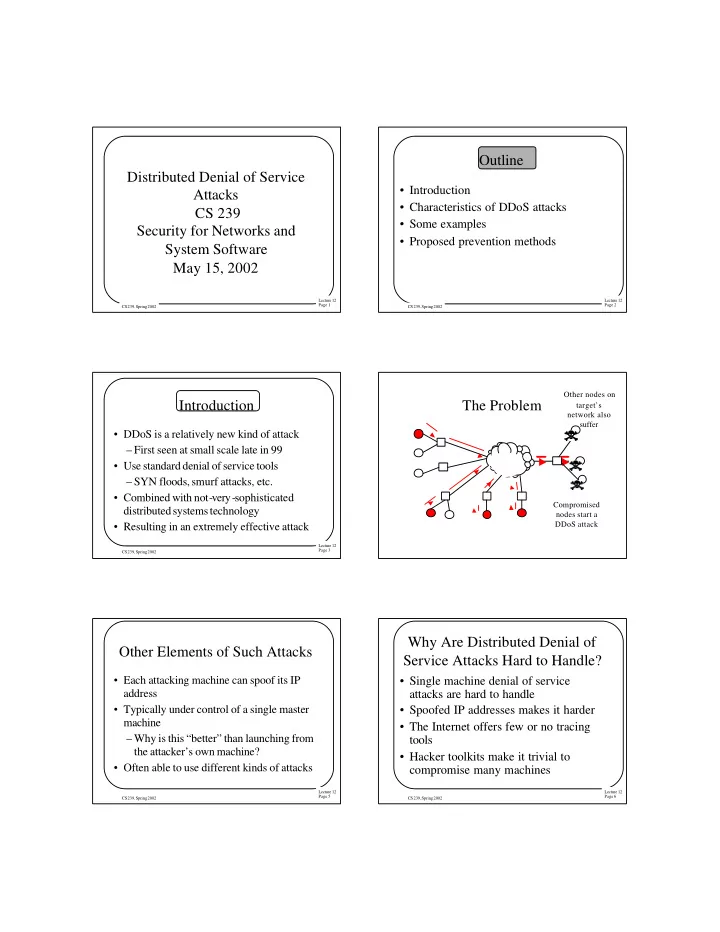

Outline Distributed Denial of Service • Introduction Attacks • Characteristics of DDoS attacks CS 239 • Some examples Security for Networks and • Proposed prevention methods System Software May 15, 2002 Lecture 12 Lecture 12 Page 1 Page 2 CS 239, Spring 2002 CS 239, Spring 2002 Other nodes on Introduction The Problem target’s network also suffer • DDoS is a relatively new kind of attack – First seen at small scale late in 99 • Use standard denial of service tools – SYN floods, smurf attacks, etc. • Combined with not-very-sophisticated Compromised distributed systems technology nodes start a DDoS attack • Resulting in an extremely effective attack Lecture 12 Page 3 CS 239, Spring 2002 Why Are Distributed Denial of Other Elements of Such Attacks Service Attacks Hard to Handle? • Each attacking machine can spoof its IP • Single machine denial of service address attacks are hard to handle • Typically under control of a single master • Spoofed IP addresses makes it harder machine • The Internet offers few or no tracing – Why is this “better” than launching from tools the attacker’s own machine? • Hacker toolkits make it trivial to • Often able to use different kinds of attacks compromise many machines Lecture 12 Lecture 12 Page 5 Page 6 CS 239, Spring 2002 CS 239, Spring 2002
Sample Distributed Denial of Trinoo Service Toolkits • Trinoo • An early example • Relatively unsophisticated • Tribe Flood Network • But still effective • Stacheldraht • Doesn’t spoof IP addresses • Uses UDP flooding attacks –Basically, sending streams of UDP packets at random ports Lecture 12 Lecture 12 Page 7 Page 8 CS 239, Spring 2002 CS 239, Spring 2002 Trinoo Masters and Daemons Tribe Flood Network (TFN) • The machines actually sending the UDP • Somewhat more sophisticated than trinoo packets are daemons • Also uses master and daemon concept • The daemons are controlled by one or more • But can spoof IP addresses masters • And can exploit several different • Master machines start and stop attacks weaknesses – And specify the victim – TCP SYN flood, ICMP echo request • Daemons store encrypted list of acceptable flood, smurf attacks, plus UDP floods masters • Master/daemon communications sometimes encrypted Lecture 12 Lecture 12 Page 9 Page 10 CS 239, Spring 2002 CS 239, Spring 2002 Where Did the Toolkits Stacheldraht Come From? • A German hacker who calls himself • German for barbed wire Mixter wrote at least some of them • Derived, apparently, from Tribe Flood –TFN, at least Network • Other hackers altered his code or wrote • Added encryption to master/daemon their own communications before TFN did • After authors fiddled around a bit, they • Uses similar attacks to TFN posted the kits to hacking sites Lecture 12 Lecture 12 Page 11 Page 12 CS 239, Spring 2002 CS 239, Spring 2002
Effects of Distributed Denial of Combating Distributed Denial of Service Attacks Service Attacks • Successfully launched against Yahoo, • Desirable properties of solution CNN, ETrade, many other sites • Approaches • Less successfully launched against Microsoft –Attacker didn’t have enough client machines • Attacks occur regularly Lecture 12 Lecture 12 Page 13 Page 14 CS 239, Spring 2002 CS 239, Spring 2002 Desirable Solution Properties Desirable Solution Properties Should be quick Should be accurate Lecture 12 Lecture 12 Page 15 Page 16 CS 239, Spring 2002 CS 239, Spring 2002 Desirable Solution Properties Desirable Solution Properties Not realistic to change basic stuff Must interoperate Should be cheap properly with • To deploy existing Internet • To run technology Lecture 12 Lecture 12 Page 17 Page 18 CS 239, Spring 2002 CS 239, Spring 2002
Desirable Solution Properties Candidate Approaches • Filtering at the target • Tracing approaches • Pushback approaches • Filtering near source • Cooperative approaches • Public hygiene approaches Must itself be • Law enforcement approaches secure Lecture 12 Lecture 12 Page 19 Page 20 CS 239, Spring 2002 CS 239, Spring 2002 Filtering at the Target Filtering Solutions • When attack is detected, filter it • How? –Based on source IP addresses –Based on other header information Shut off the flow –Based on packet payload information at the target’s router • Modern routers can do this filtering Lecture 12 Page 21 CS 239, Spring 2002 Problems With Filtering Tracing Approaches Solutions • Find the sending sources and shut them • Can only be reactive down • Often requires assistance of third party • Requires tracing the attack packets –ISP provider or backbone site back through the network • Can’t filter everything always • Not simple with today’s technology • More clever attacks could bypass any • Smart attackers only attack for a while simple filter –Leaving nothing to trace Lecture 12 Lecture 12 Page 23 Page 24 CS 239, Spring 2002 CS 239, Spring 2002
Basics of Tracing Tracing Solutions • Identify an attack packet ? • Check its IP address ? ? ? ? – If not forged, take external action – But it’s probably forged • Ask next upstream router where it came Trace the attack from back to its source(s) • And that router must ask the previous router Lecture 12 Page 25 CS 239, Spring 2002 Problems With Tracing Solutions Pushback Approaches • Install filtering at router close to target • No automated tools to do this • That router asks upstream routers to install • “Asking a router” amounts to a phone filters call to a system administrator – Which relieves the burden on target’s • Ultimately requires help of backbone router providers • Filters can be pushed further back, as • In wide DDOS, may have to trace needed hundreds of attack streams • Can rate limit, rather than filter Lecture 12 Lecture 12 Page 27 Page 28 CS 239, Spring 2002 CS 239, Spring 2002 Problems With Pushback Pushback Solutions But that router Approaches may still be So push the filtering overloaded • Requires cooperation among parties further back who normally don’t cooperate • Must address security flaws • Like other types of filtering, may filter the wrong stuff Start by shutting –And, with this approach, may get a off the flow at the target’s router lot of it Lecture 12 Lecture 12 Page 29 Page 30 CS 239, Spring 2002 CS 239, Spring 2002
Filtering Near the Sources Source Side Filtering Solutions • Try to detect the problem close to the sites that are creating the traffic • Rate limit at routers close to the problem sites • A distributed solution to a distributed problem • Routers near attackers may have better information Shut off the flow at multiple entry points Lecture 12 Lecture 12 Page 31 Page 32 CS 239, Spring 2002 CS 239, Spring 2002 Problems With Filtering Near the Cooperative Approaches Sources • Requires deployment at many sites to be • Gather information from many effective different sources • Trying to detect the problem far away from • Analyze the total information to where it occurs understand what’s going on • Might be foolable from outside the local network • Apply some subset of previous – Turning the defense tool into an attack mechanisms to solve the problem tool Lecture 12 Lecture 12 Page 33 Page 34 CS 239, Spring 2002 CS 239, Spring 2002 Problems With Cooperative Public Hygiene Approaches Approaches • Must leverage off other approaches • A longer-term solution –Possibly inheriting their problems • Make sure that it’s harder to launch attacks • Some information provided may be untrustworthy • Make sure it’s harder to spoof IP addresses • Presumes some network connectivity • Basically, make sure everyone on the –Will that be available during an Internet has secure machines attack? Lecture 12 Lecture 12 Page 35 Page 36 CS 239, Spring 2002 CS 239, Spring 2002
Problems With Public Hygiene Public Hygiene Solutions Approaches • Only work well if a high percentage of all sites follow them • Only work as long as no new vulnerabilities are discovered • Some of the prophylactic measures are limiting to those who apply them – And they’re not directly getting the Make it harder to benefits corrupt a bunch of machines Lecture 12 Lecture 12 Page 37 Page 38 CS 239, Spring 2002 CS 239, Spring 2002 Law Enforcement Approaches Law Enforcement Solutions • Call in the FBI • Have them trace down the culprit and toss him in jail • That’ll teach him! Call in the Feds! Lecture 12 Lecture 12 Page 39 Page 40 CS 239, Spring 2002 CS 239, Spring 2002 Problems With Law Enforcement A Sample Approach Approaches • The law, in its majesty, moves slowly • D-WARD –Even by human standards • Being developed here at UCLA • This kind of investigation is inherently • One of the family of approaches that costly works close to sources –And thus can’t often be done • Smart attackers may be very, very hard to find Lecture 12 Lecture 12 Page 41 Page 42 CS 239, Spring 2002 CS 239, Spring 2002
Recommend
More recommend