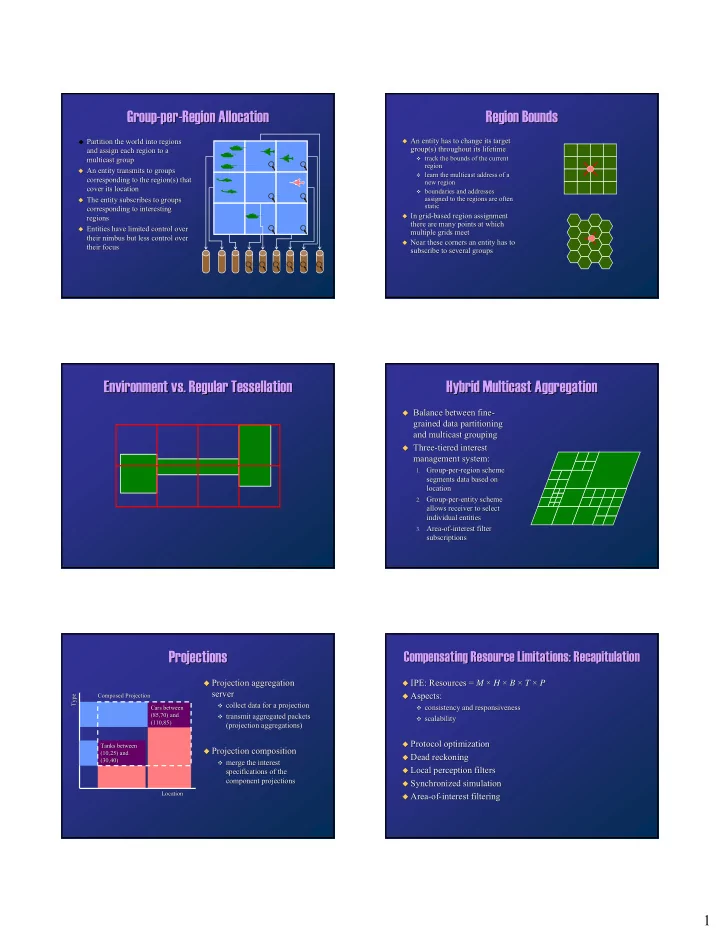

Group- Group -per per- -Region Allocation Region Allocation Region Bounds Region Bounds � An entity has to change its target An entity has to change its target � Partition the world into regions Partition the world into regions � group(s) throughout its lifetime group(s) throughout its lifetime and assign each region to a and assign each region to a � track the bounds of the current track the bounds of the current multicast group multicast group � region region � An entity transmits to groups An entity transmits to groups � � learn the multicast address of a learn the multicast address of a � corresponding to the region(s) that corresponding to the region(s) that new region new region cover its location cover its location � boundaries and addresses boundaries and addresses � assigned to the regions are often assigned to the regions are often � The entity subscribes to groups The entity subscribes to groups � static static corresponding to interesting corresponding to interesting � In grid In grid- -based region assignment based region assignment regions regions � there are many points at which there are many points at which � Entities have limited Entities have limited control over control over � multiple grids meet multiple grids meet their nimbus but less control over their nimbus but less control over � Near these corners an entity has to Near these corners an entity has to � their focus their focus subscribe to several groups subscribe to several groups Environment vs. Regular Tessellation Tessellation Hybrid Multicast Aggregation Environment vs. Regular Hybrid Multicast Aggregation � Balance between Balance between fine fine- - � grained grained data partitioning data partitioning and multicast grouping and multicast grouping � Three Three- -tiered tiered interest interest � management system: management system: 1. Group Group- -per per- -region region scheme scheme 1. segments data based on segments data based on location location 2. Group Group- -per per- -entity entity scheme scheme 2. allows receiver to select allows receiver to select individual entities individual entities 3. Area Area- -of of- -interest interest filter filter 3. subscriptions subscriptions Projections Projections Compensating Resource Limitations: Recapitulation Compensating Resource Limitations: Recapitulation � Projection aggregation Projection aggregation � IPE: Resources = IPE: Resources = M M × × H H × × B B × × T T × × P � � P server server � Aspects: Aspects: Composed Projection Composed Projection Type Type � � collect data for a projection collect data for a projection � � consistency and responsiveness consistency and responsiveness Cars between Cars between � (85,70) and (85,70) and � transmit aggregated packets transmit aggregated packets � � scalability scalability � (110,85) (110,85) (projection aggregations) (projection aggregations) � Protocol optimization Protocol optimization � Tanks between Tanks between � Projection composition Projection composition � (10,25) and (10,25) and � Dead reckoning Dead reckoning � (30,40) (30,40) � merge the interest merge the interest � � Local perception filters Local perception filters specifications of the specifications of the � component projections component projections � Synchronized simulation Synchronized simulation � Location Location � Area Area- -of of- -interest filtering interest filtering � 1
§10 Cheating Prevention §10 Cheating Prevention The goals of cheating prevention The goals of cheating prevention � traditional cheating in computer games traditional cheating in computer games � protect the sensitive information protect the sensitive information � � � cracking the copy protection cracking the copy protection � cracking passwords cracking passwords � � � fiddling with the binaries: boosters, trainers, etc. fiddling with the binaries: boosters, trainers, etc. � pretending to be an administrator pretending to be an administrator � � � here, the focus is on multiplayer online games here, the focus is on multiplayer online games � provide a fair playing field provide a fair playing field � � � exploiting technical advantages exploiting technical advantages � tampering the network traffic tampering the network traffic � � � exploiting social advantages exploiting social advantages � colluding with other players colluding with other players � � � cheaters’ motivations cheaters’ motivations � uphold a sense of justice inside uphold a sense of justice inside � � the game world the game world � vandalism and dominance vandalism and dominance � � peer prestige peer prestige � abusing beginners abusing beginners � � � greed greed � gangs gangs � � Network Security Taxonomy of Online Cheating of Online Cheating 1 (4) 1 (4) Network Security Taxonomy � Cheating by compromising Cheating by compromising passwords passwords � Military Military � � � dictionary attacks dictionary attacks � � private private networks networks → → no problem no problem � � Cheating by social engineering Cheating by social engineering � � Business, industry, e Business, industry, e- -commerce,… commerce,… � � password scammers password scammers � � ‘traditional’ ‘traditional’ security problems security problems � � Cheating Cheating by denying service from peer players by denying service from peer players � � denial denial- -of of- -service service ( (DoS) attack DoS) attack � Entertainment industry Entertainment industry � � � clog clog the opponent’s the opponent’s network connection network connection � � multiplayer computer games, online games multiplayer computer games, online games � � specialized specialized problems problems � Taxonomy of Online Cheating of Online Cheating 2 (4) 2 (4) Taxonomy of Online Cheating of Online Cheating 3 (4) 3 (4) Taxonomy Taxonomy � Cheating due to illicit information Cheating due to illicit information � Cheating Cheating by tampering with by tampering with � � the network traffic � access to replicated, hidden game data access to replicated, hidden game data the network traffic � � compromised software or data compromised software or data � � reflex augmentation reflex augmentation � � packet interception packet interception fire � fire � Cheating related with internal misuse Cheating related with internal misuse � � look look- -ahead cheating ahead cheating � � privileges privileges of system administrators of system administrators � rotate rotate fire fire � packet replay attack packet replay attack � � logging critical operations into logging critical operations into CD CD- -ROMs ROMs � � Cheating with authoritative clients Cheating with authoritative clients � Cheating by exploiting a bug or design flaw Cheating by exploiting a bug or design flaw � � � repair the observed defects with patches repair the observed defects with patches � � receivers accept commands blindly receivers accept commands blindly � � limit the original functionality to avoid the defects limit the original functionality to avoid the defects � � requests instead of commands requests instead of commands � � good software design in the first place! good software design in the first place! � � checksums from the game state checksums from the game state � 2
Recommend
More recommend