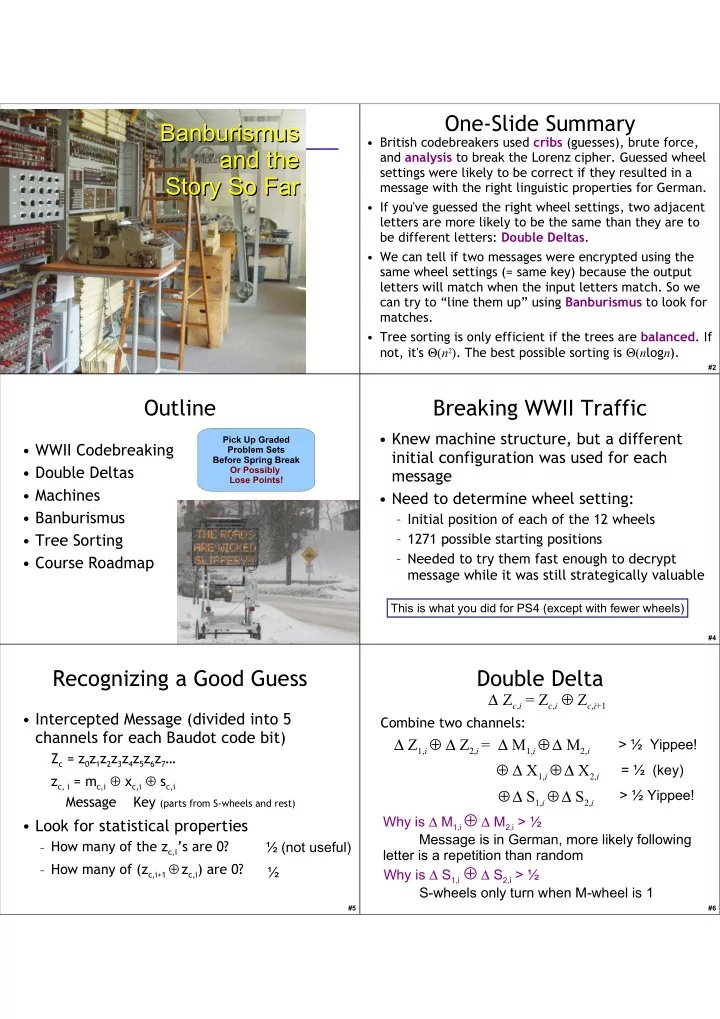

One-Slide Summary Banburismus Banburismus • British codebreakers used cribs (guesses), brute force, and the and the and analysis to break the Lorenz cipher. Guessed wheel settings were likely to be correct if they resulted in a Story So Far Story So Far message with the right linguistic properties for German. • If you've guessed the right wheel settings, two adjacent letters are more likely to be the same than they are to be different letters: Double Deltas . • We can tell if two messages were encrypted using the same wheel settings (= same key) because the output letters will match when the input letters match. So we can try to “line them up” using Banburismus to look for matches. • Tree sorting is only efficient if the trees are balanced . If not, it's Θ ( n 2 ) . The best possible sorting is Θ ( n log n ). #2 Outline Breaking WWII Traffic • Knew machine structure, but a different Pick Up Graded • WWII Codebreaking Problem Sets initial configuration was used for each Before Spring Break • Double Deltas Or Possibly message Lose Points! • Machines • Need to determine wheel setting: • Banburismus – Initial position of each of the 12 wheels • Tree Sorting – 1271 possible starting positions – Needed to try them fast enough to decrypt • Course Roadmap message while it was still strategically valuable This is what you did for PS4 (except with fewer wheels) #3 #4 Recognizing a Good Guess Double Delta ∆ Z c , i = Z c , i ⊕ Z c , i +1 • Intercepted Message (divided into 5 Combine two channels: channels for each Baudot code bit) ∆ Z 1, i ⊕ ∆ Z 2, i = ∆ M 1, i ⊕ ∆ M 2, i > ½ Yippee! Z c = z 0 z 1 z 2 z 3 z 4 z 5 z 6 z 7 … ⊕ ∆ X 1, i ⊕ ∆ X 2, i = ½ (key) z c, i = m c,i ⊕ x c,i ⊕ s c,i ⊕ ∆ S 1, i ⊕ ∆ S 2, i > ½ Yippee! Message Key (parts from S-wheels and rest) Why is ∆ M 1,i ⊕ ∆ M 2,i > ½ • Look for statistical properties Message is in German, more likely following – How many of the z c,i ’s are 0? ½ (not useful) letter is a repetition than random – How many of (z c,i+1 ⊕ z c,i ) are 0? Why is ∆ S 1,i ⊕ ∆ S 2,i > ½ ½ S-wheels only turn when M-wheel is 1 #5 #6
Using the Advantage Actual Advantage • If the guess of X is correct, should see higher • Probability of repeating letters than ½ of the double deltas are 0 Prob[ ∆ M 1, i ⊕ ∆ M 2, i = 0] ~ 0.614 • Try guessing different configurations to find 3.3% of German digraphs are repeating highest number of 0 double deltas • Probability of repeating S-keys • Problem : Prob[ ∆ S 1, i ⊕ ∆ S 2, i = 0] ~ 0.73 # of double delta operations to try one config Prob[ ∆ Z 1, i ⊕ ∆ Z 2, i ⊕ ∆ X 1, i ⊕ ∆ X 2, i = 0] = length of Z * length of X = 0.614 * 0.73 + (1-0.614) * (1-0.73) = for 10,000 letter message = 12 M for each setting * 7 ⊕ per double delta ∆ M and S are 0 ∆ M and S are 1 = 89 M ⊕ operations Need a fast = 0.55 if the wheel settings guess is correct (0.5 otherwise) way to compute XOR! (that's a lot!) #7 #8 Heath Robinson Machine Colossus • Dec 1942: Decide to build a machine to do these ⊕ s quickly, due June 1943 • Apr 1943: first “Heath • Heath Robinson machines were too slow Robinson” machine is • Colossus designed and first built in Jan 1944 delivered! • Replaced keytext tape loop with electronic keytext – Predecessor to Colossus generator • Intercepted ciphertext on tape: • Speed up ciphertext tape: – 2000 characters per second – 5,000 chars per second = 30 mph (12 miles per hour) – Perform 5 double deltas simultaneously – Needed to perform 7 ⊕ operations each ½ ms Heath Robinson, British Cartoonist (1872-1944) – Speedup = 2.5X for faster tape * 5X for parallelism #9 #10 Impact on WWII Colossus Design Ciphertext Tape • 10 Colossus machines operated at Bletchley park Electronic Keytext Logic Tape Reader – Various improvements in speed Generator • Decoded 63 million letters in Nazi command messages Position Counter Counter • Learned German troop locations to plan D-Day (knew the deception was working) Printer #11 #12
Colossus History Kept secret after the war, all machines destroyed How could the folks at Bletchley Park solve a problem ~ 1 quintillion times harder than ps4? Rebuild, Bletchley Park, During WWII Summer 2004 #13 #14 Motivation Helps… Confronted with the prospect of defeat, the Allied cryptanalysts had worked night and day to penetrate German ciphers. It would appear that fear was the main driving force, and that adversity is one of the foundations of successful codebreaking. Simon Singh, The Code Book Poster in RAF Museum #15 #16 Liberal Arts Trivia: Maritime Law Liberal Arts Trivia: Geography • A letter of marque is an official government • This capital city of Uttar Pradesh, the most document authorizing an agent to search, populous state of India, is popularly known as seize, or destroy specified assets or personnel the The City of Nawabs. It is also known as belonging to a foreign party beyond the the Golden City of the East, Shiraz-i-Hind and borders of the nation ("marque" or frontier). The Constantinople of India. It is a center of They are usually used to authorize private Hindi and Urdu literature, and the birthplace parties to raid and capture merchant shipping of Kathak, a classic Indian dance form. The of an enemy nation. In the past, a ship city was besieged during the Indian Rebellion operating under a letter of marque and of 1857. reprisal was privately owned and was called a "private man-of-war" or ... what? #17 #18
Banburismus Enigma • Invented commercially, 1923 Given two Enigma- • German Navy, Army, Air Force encrypted messages, how • About 50,000 in use (many were can we determine if they captured by Allies) were encrypted starting • Modified throughout WWII, with the same wheel Germans believed perfectly secure settings? • Kahn’s Codebreakers (1967) didn’t know it was broken • Turing’s 1940 Treatise on Enigma Enigma machine at Bletchley declassified in 1996 Park Enigma in Use, 10 December 1943 #19 #20 Simple Substitution Ciphers Reverse Engineering ABCDEFGHIJKLMNOPQRSTUVWXYZ Enigma encrypt decrypt “This fictional movie about a fictional U.S. submarine mission is followed by a mention in the end credits of those actual British missions. Oh, the British deciphered the Enigma code, too. Come to think of it, they pretty JIDKQACRSHLGWNFEXUZVTPMYOB much did everything in real life that the Americans do in this movie.” Roger Ebert’s review of U-571 HELLO ⇒ RQGGF (2000 Academy Award Winner) #21 #22 http://en.wikipedia.org/wiki/Image:Enigma-action.png Rotor Wheels Simple substitution Latch turns next rotor once per rotation Image from #23 #24
Language is Non-Random Alan Turing’s Solution • Random strings: the probability of two letters in the two messages matching is 1/26 (number of letters in alphabet) • Same-encrypted strings: the output letters will match when the input letters match M1: GXCYBGDSLVWBDJLKWIPEHVYGQZWDTHRQXIKEESQS – This happens much more frequently because some letters (e.g., “e” is ~13% of all letters) M2: YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU are more common #25 #26 Banburismus Banbury Bletchley Park M1: GXCYBGDSLVWBDJLKWIPEHVYGQZWDTHRQXIKEESQS M2: YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU #27 #28 Intercepted Message 2 Intercepted Message 1 Intercepted Message 1 A A A A B B B B C C C C D D D D E E E E F F F F G G G G H H H H I I I I J J J J K K K K L L L L M M M M N N N N O O O O P P P P Q Q Q Q R R R R S S S S T T T T U U U U V V V V W W W W X X X X Y Y Y Y Z Z Z Z CKGLPIFLR... PICJTTIOQN... #29 #30
Trying Possible Alignments Trying Possible Alignments GXCYBGDSLVWBDJLKWIPEHVYGQZWDTHRQXIKEESQS GXCYBGDSLVWBDJLKWIPEHVYGQZWDTHRQXIKEESQS YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU ... ... YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAX.. YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAX.. #31 #32 Trying Possible Alignments Trying Possible Alignments GXCYBGDSLVWBDJLKWIPEHVYGQZWDTHRQXIKEESQS GXCYBGDSLVWBDJLKWIPEHVYGQZWDTHRQXIKEESQS YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAXVXDVU ... ... YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAX.. YNSCFCCPVIPEMSGIZWFLHESCIYSPVRXMCFQAX.. #33 #34 Liberal Arts Trivia: Geology • A stratovolcano or composite volcano is a tall, conical volcano made of many layers of lava, tephra and volcanic ash: they are characterized by steep sides and periodic eruptions. They are common in subduction zones where the ocean crust is drawn under the continental crust. Mount St. Helens and Turing’s Hut 8 at Bletchley Park Mount Fuji are both stratovolcanos: name the Don’t complain about your working space. country containing each one. You can do good computer science anywhere. But find a quiet, undisturbed place to work on the exam. #35 #36
Recommend
More recommend