
Introduction Retargetable Compilers System on Chip ■ Many different types of DSPs and embedded processors ■ Daniel Karlsson ASIPs (replace by latest general purpose processor?) ❚ danka@ida.liu.se no compromise, high speed, low cost, low power ❚ Compilation plays important role ■ ESLAB, IDA, Linköpings universitet Retargetable Processors 1 of 36 Retargetable Processors 2 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001 Outline Basic Compilation Techniques (Overview) Introduction ■ Basic compilation techniques ■ Retargetable compilation issues ■ Processor modelling and the CHESS compiler ■ Summary ■ Retargetable Processors 3 of 36 Retargetable Processors 4 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001
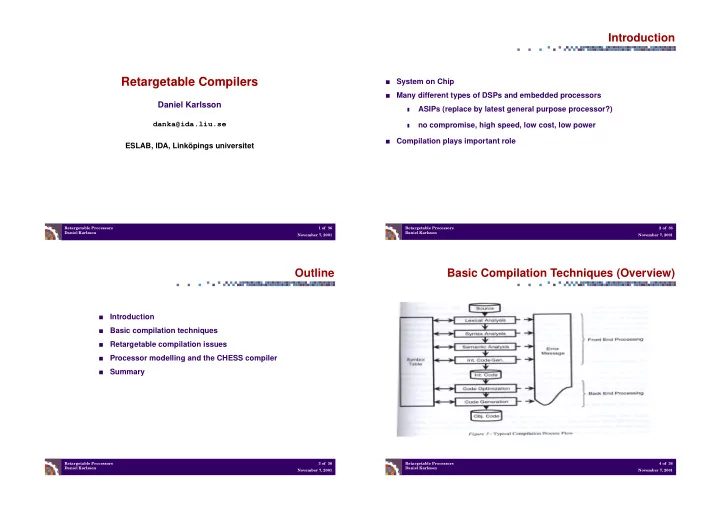
Front-End Processing Back-End Processing (1/3) Lexical analysis Machine independent code optimisation ■ ■ Generating tokens Common sub-expression elimination ❚ ❚ Syntax analysis Loop unrolling ■ ❚ Generating parse tree ❚ Loop-invariant expression movement ❚ Creating symbol table ❚ Induction variable elimination ❚ Semantic analysis ■ Unreachable code elimination ❚ Generating syntax tree ❚ Control flow optimisation ❚ Intermediate code generation ■ Arithmetic optimisation ❚ Generating quadruples (virtual machine) ❚ Operation combining ❚ Retargetable Processors 5 of 36 Retargetable Processors 6 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001 Back-End Processing (2/3) Back-End Processing (3/3) Machine dependent code optimisation ■ Machine specific instruction mapping ❚ Object code generation ■ - Auto incr/decr indexed memory access instructions Code reordering ❚ - Stack instructions Instruction pattern matching ❚ - MAC (Multiply and ACcumulate) instruction Register allocation ❚ Spill code reduction ❚ Register assignment ❚ - Too many pseudo registers -> memory space access Instruction scheduling ❚ - Pipeline hazards Retargetable Processors 7 of 36 Retargetable Processors 8 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001
Questions What’s the Difference? What stages/transformations does the code go through in a compiler? Retargetability ■ ■ Name a few optimisation strategies, both machine independent and machine Register constraints ■ ■ dependent. Special-purpose registers ❚ What are the tasks of code generation? ■ Unusual wordlength ❚ Arithmetic specialisation ■ Instruction-level parallelism ■ Discussion: DCU and ACU ❚ Is there one optimisation strategy which generally generates better results ■ Optimisations ■ than others? Poor compilation unaffordable ❚ Retargetable Processors 9 of 36 Retargetable Processors 10 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001 About Retargetability Levels of Retargetability Rapid set-up of a compiler will boost for algorithm developers wishing to evaluate the efficiency of application code on different existing architectures. Retargetability permits architecutre exploration. The processor designer is able Automatically retargetable ■ to tune the architecture to run efficiently for a set of source applications in a Compiler user retargetable ■ particular domain. Compiler developer retargetable ■ Instruction-Set Source Code Specification Architecture Retargetable FirmWare SoftWare Exploration Compiler Development HardWare Design Design Cycle Cycle Machine Code Retargetable Processors 11 of 36 Retargetable Processors 12 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001
Processor Modelling Languages Principal Compiler Tasks Mimola (HDL) ■ Netlists display an explicit activation of functional components by bits ❚ in the instruction word. Instruction-set matching and selection ■ Register allocation and assignment ■ nML ■ Instruction scheduling and compaction ■ Describes behavioural mechanics rather than structural detail. ❚ Description of operations, storage elements, binary and assembly syn- ❚ tax, and an execution model. Based on synchronous register-transfer model ❚ Instruction Set Graph (ISG) ■ Associates behavioural information with structural information. ❚ Retargetable Processors 13 of 36 Retargetable Processors 14 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001 Instruction-Set Matching and Selection Register Allocation and Assignment Instruction set matching: Determine wide set of target instructions which can Register allocation: Determine a set of registers which may hold the value of a implement the source code. variable. Instruction set selection: Choose the best subset of instructions from the Register assignment: Determine a physical register which is specified to hold matched set. the value of a variable. A pattern based approach: Solution based on graph colouring: 1: Produce a template base of patterns, each member represents an instruction. 1: Build interference graph. (nodes=variables, edges=overlap) 2: Translate the source program to a forest of syntax trees. 2: Assign colours to each node. Adjacent nodes may not have the 3: Match the trees to the pattern set. same colour. 4: A subset of all the matched patterns are selected to form the implementation in microcode. Drawback: Can not handle control-flow constructs (if, case, function calls, ...) Special purpose registers complicate the matter. Retargetable Processors 15 of 36 Retargetable Processors 16 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001
Instruction Scheduling Instruction Compaction Scheduling: Determine an order of execution of instructions. Huge interdependence with instruction selection and register allocation. Mutation scheduling: Compaction: Fine-grained scheduling to support instruction-level parallelism. 1: Implementations of instructions can be regenerated by means of a mutation set. 1: Define pseudo microinstructions and sequences of micro-oper- 2: After generation of quadruples, calculate critical path. ations with source and destinations properties. 3: Improve speed by identifying the instructions which lie on 2: Pack and upward past pseudo microinstructions to form real critical paths and mutating them to other implementations which microinstructions. allow a rescheduling of the instructions. Integer Linear Programming (ILP): 1: Consider the following aspects: pattern-matching, scheduling, register assignment and spilling to memory. 2: Dynamically make trade-offs between these based on an objec- tive function and a set of constraints. Common obj. func.: minimise time. Common constraints: architecture characteristics. Retargetable Processors 17 of 36 Retargetable Processors 18 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001 Optimisation for Embedded Processors Questions ”Optimisations” which could reduce efficiency: Common subexpression elimination -> increase register pressure. Constant propagation -> too narrow instruction word What are the main differences between compilationfor general purpose proc- ■ essors and embedded processors? Loop optimisations (unrolling, pipelining, ...) are important. What are the principal compiler tasks? ■ Take processor characteristics into account! Can we just adopt optimisation techniques for general purpose compilers? ■ Memory optimisations may lead to cost reduction. Narrowing of instruction words ■ Paged memory ■ Reduce number of page changes ❚ Long subroutines broken into several pieces ❚ Multi-memory allocation ■ Retargetable Processors 19 of 36 Retargetable Processors 20 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001
Instruction Set Graph (ISG) (1/2) Instruction Set Graph (ISG) (2/2) 〈 , 〉 ∪ Bipartite graph with where contains ■ GISG = VISG EISG VISG = VS VI VS all vertices representing storage elements in the processor and contains all VI ⊆ ( × ) ∪ ( × ) vertices representing its operation types. Edges rep- EISG VS VI VI VS resent the connectivity of the processor. An operation type is a primitive processor activity. ■ Retargetable Processors 21 of 36 Daniel Karlsson Retargetable Processors 22 of 36 November 7, 2001 Daniel Karlsson November 7, 2001 Enabling and Encoding Storage Elements Static storage ■ The set of instructions that enables operation type is called its enabling Ei i ■ Transitory storage ■ 2 B → condition . . enabling : VI ∩ ⊆ ( ) Given a subset of operation types , VIo VI enabling VIo = enabling i ■ ∈ i VIo Memory: VM is the enabling condition for the set . VIo Registers: VR Transitories: VT ∅ The set has an encoding conflict if . ■ VIo enabling VIo = ∪ ∪ Structural skeleton: VS = VM VR VT Retargetable Processors 23 of 36 Retargetable Processors 24 of 36 Daniel Karlsson Daniel Karlsson November 7, 2001 November 7, 2001
Recommend
More recommend