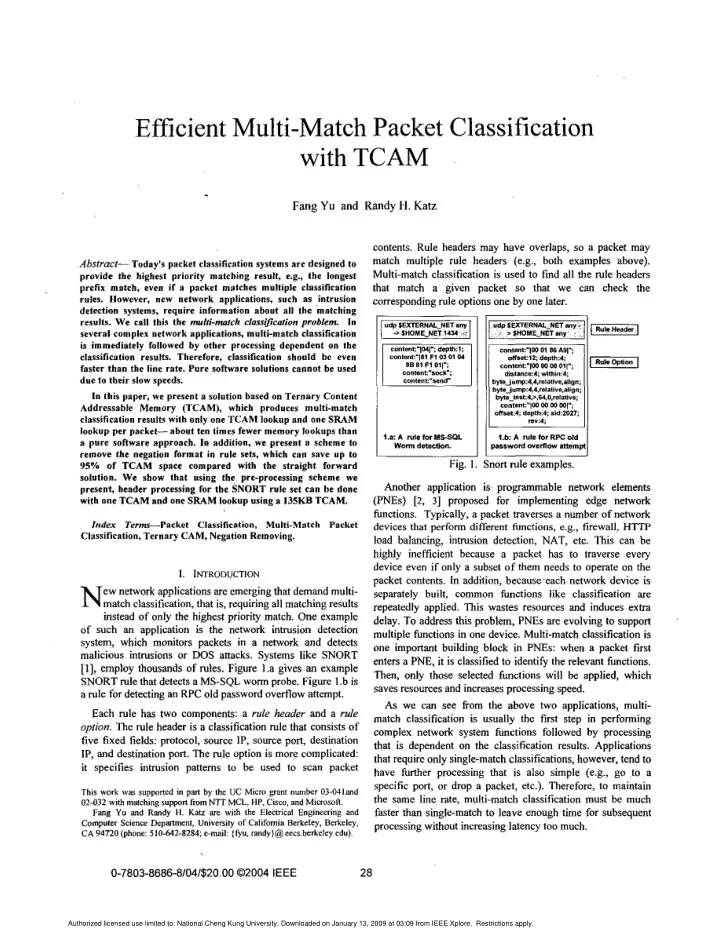

Fang Yu and Randy H. Katz zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA Efficient Multi-Match Packet Classification contents. Rule headers may have overlaps, zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA with TCAM results. We call this the multi-mtch classijication zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA so a packet may match multiple rule headers (e.g., both examples above). Abstract- Today's packet classification systems are designed to provide the highest priority matching result, e.g., the longest Multi-match classification is used to fmd all the rule headers that match a given packet so that we can check the prefix match, even if a packet matches multiple classification rules. However, new network applications, such as intrusion corresponding rule options one by one later. detection systems, require information about all the matching problem In several complex network applications, multi-match classification is immediately followed by other processing dependent on the contmt:~p4l": conten1:"lW 01 86 AOl"; daplh.1; classification results. Therefore, classification should be even contenl'"l81 F1 I 01 04 I 0ffset:lZ: depth4 0) O B $1 F1 0117 faster than the line rate. Pure software solutions cannot be used cO"lB"t:--K-: due to their slow speeds. with one TCAM and one SRAM lookup using a zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA In this paper, we present a solution based on Ternary Content Addressable Memory (TCAM), which produces multi-match classification results with only one TCAM lookup and one SRAM Classification, Ternary CAM, Negation Removing. zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA lookup per packet- about ten times fewer memory lookups than 1.a: A rule for MSSQL 1.b A rule for RPC Old a pure software approach. In addition, we present a scheme to remove the negation format in rule sets, which can save u p to Fig. 1. Snort rule examples. 95% of TCAM space compared with the straight forward solution. We show that using the pre-processing scheme we Another application is. proganunable network elements present, header processing for the SNORT rule set can be done 135KB (PNEs) [2, 31 proposed for implementing edge network TCAM. functions. Typically, a packet traverses a number of network Index Term-Packet Classification, Multi-Match Packet devices that perform different functions, e.g., firewall, HTTP load balancing, intrusion detection, NAT, etc. This can be highly inefficient because a packet has to traverse every device even if only a subset of them needs to operate on the SNORT rule that detects a MS-SQL worm probe. Figure zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA I. INTRODUCTION packet contents. In addition, becauweach network device is N ew network applications are emerging that demand multi- separately built, common functions like classification are match classification, that is, requiring all matching results repeatedly applied. This wastes resources and induces extra Each rule has two components: a rule header and a rule zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA instead of only the highest priority match. One example delay. To address this problem, PNEs are evolving to support of such an application is the network intrusion detection multiple functions in one device. Multi-match classification is system, which monitors packets in a network and detects one important building block in PNEs: when a packet first malicious intrusions or DOS attacks. Systems like SNORT enters a PNE, it is classified to identify the relevant functions. [I], employ thousands of rules. Figure 1.a gives an example Then, only those selected functions will be applied, which 1 .b is saves resources and increases processing speed. a rule for detecting an RPC old password overflow attempt. supported in pm by the UC zyxwvutsrqponmlkjihgfedcbaZYXWVUTSRQPONMLKJIHGFEDCBA As we can see !?om the above two applications, multi- match classification is usually the fmt step in performing @on. The rule header is a classification rule that consists of complex network system functions followed by processing five fixed fields: protocol, source IP, source port, destination that is dependent on the classification results. Applications IP, and destination port. The rule option is more complicated: that require only single-match classifications, however, tend to it specifies intrusion patterns to be used to scan packet have further processing that is also simple (e.g., go to a specific port, or drop a packet, etc.). Therefore, to maintain This work was Micro @ant number 03-041and 02-032 with matching support fromNTTMCL, HP, Cisco, and Microson. the same line rate, multi-match classification must be much Fang Yu and Randy H. Katz are with the Electrical Engineering and faster than single-match to leave enough time for subsequent Computer Science Depmtmenf, University of California Berkeley, Berkeley, processing without increasing latency too much. CA 94720 (phone: 510-642-8284; e-mail: (&U, randy)@ eecs.berkeley.edu). 0-7803-8686-8/04/$20.00 02004 IEEE 28 Authorized licensed use limited to: National Cheng Kung University. Downloaded on January 13, 2009 at 03:09 from IEEE Xplore. Restrictions apply.
Recommend
More recommend