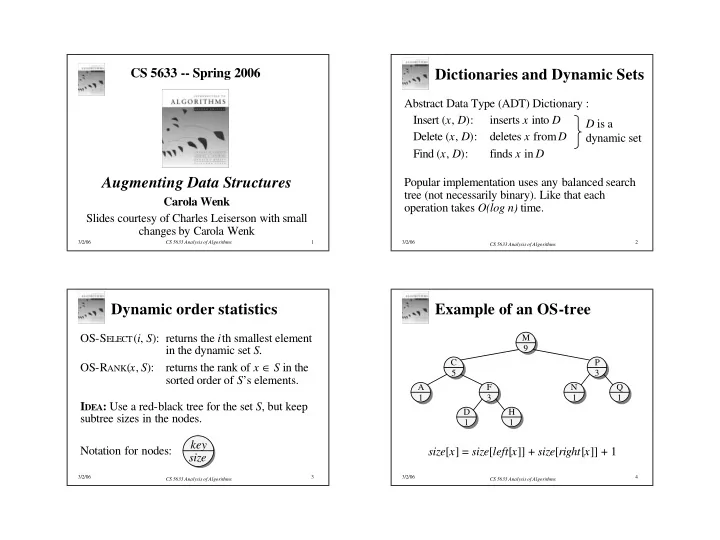

CS 5633 -- Spring 2006 Dictionaries and Dynamic Sets Abstract Data Type (ADT) Dictionary : Insert ( x , D ): inserts x into D D is a Delete ( x , D ): deletes x from D dynamic set Find ( x , D ): finds x in D Augmenting Data Structures Popular implementation uses any balanced search tree (not necessarily binary). Like that each Carola Wenk operation takes O(log n) time. Slides courtesy of Charles Leiserson with small changes by Carola Wenk 3/2/06 CS 5633 Analysis of Algorithms 1 3/2/06 2 CS 5633 Analysis of Algorithms Dynamic order statistics Example of an OS-tree OS-S ELECT ( i , S ): returns the i th smallest element M 9 in the dynamic set S. returns the rank of x ∈ S in the C P OS-R ANK ( x , S ): 5 3 sorted order of S ’s elements. A F N Q 1 3 1 1 I DEA : Use a red-black tree for the set S , but keep D H subtree sizes in the nodes. 1 1 key Notation for nodes: size [ x ] = size [ left [ x ]] + size [ right [ x ]] + 1 size 3/2/06 3 3/2/06 4 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms
Selection Example Implementation trick: Use a sentinel OS-S ELECT ( root , 5) (dummy record) for NIL such that size [ NIL ] = 0. i = 5 M M OS-S ELECT ( x , i ) ? i th smallest element in the k = 6 9 9 subtree rooted at x i = 5 C C P k ← size [ left [ x ]] + 1 k = 2 ? k = rank( x ) 5 5 3 if i = k thenreturn x A F F i = 3 N Q if i < k k = 2 1 3 3 1 1 thenreturn OS-S ELECT ( left [ x ] , i ) D H H H i = 1 else return OS-S ELECT ( right [ x ] , i – k ) 1 1 1 1 k = 1 (OS-R ANK is in the textbook.) Running time = O ( h ) = O (log n ) for red-black trees. 3/2/06 5 3/2/06 6 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms Data structure maintenance Example of insertion Q. Why not keep the ranks themselves I NSERT (“K”) in the nodes instead of subtree sizes? M M 10 9 A. They are hard to maintain when the C C P red-black tree is modified. 6 5 3 k ← size [ left [ x ]] + 1 ? k = rank( x ) A F F N Q 1 3 4 1 1 Modifying operations: I NSERT and D ELETE . D H H 1 2 1 Strategy: Update subtree sizes when K inserting or deleting. 1 3/2/06 7 3/2/06 8 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms
Handling rebalancing Data-structure augmentation Don’t forget that RB-I NSERT and RB-D ELETE may Methodology: ( e.g., order-statistics trees ) also need to modify the red-black tree in order to 1. Choose an underlying data structure ( red-black maintain balance. trees ). • Recolorings : no effect on subtree sizes. 2. Determine additional information to be stored • Rotations : fix up subtree sizes in O (1) time. in the data structure ( subtree sizes ). Example: 3. Verify that this information can be maintained E C for modifying operations (RB-I NSERT , RB- 16 16 C E D ELETE — don’t forget rotations ). 4 7 11 8 4. Develop new dynamic-set operations that use the information (OS-S ELECT and OS-R ANK ). 7 3 3 4 ∴ RB-I NSERT and RB-D ELETE still run in O (log n ) time. These steps are guidelines, not rigid rules. 3/2/06 9 3/2/06 10 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms Interval trees Following the methodology Goal: To maintain a dynamic set of intervals, 1. Choose an underlying data structure. such as time intervals. •Red-black tree keyed on low (left) endpoint. 2. Determine additional information to be i = [7, 10] stored in the data structure. low [ i ] = 7 10 = high [ i ] •Store in each node x the largest value m [ x ] 5 11 17 19 in the subtree rooted at x , as well as the 4 8 15 18 22 23 interval int [ x ] corresponding to the key. Query: For a given query interval i , find an int interval in the set that overlaps i . m 3/2/06 11 3/2/06 12 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms
Example interval tree Modifying operations 3. Verify that this information can be maintained for modifying operations. •I NSERT : Fix m ’s on the way down. 17,19 •Rotations — Fixup = O (1) time per rotation: 23 red 11,15 6,20 5,11 22,23 30 30 18 23 6,20 11,15 4,8 15,18 30 19 30 19 8 18 high [ int [ x ]] 30 14 14 19 7,10 m [ x ] = max m [ left [ x ]] 10 Total I NSERT time = O (log n ); D ELETE similar. m [ right [ x ]] 3/2/06 13 3/2/06 14 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms New operations Example 1: I NTERVAL -S EARCH ([14,16]) 4. Develop new dynamic-set operations that use 17,19 x 23 the information. 14 16 I NTERVAL -S EARCH ( i ) 5,11 22,23 x ← root 18 23 while x ≠ NIL and ( low [ i ] > high [ int [ x ]] 4,8 15,18 or low [ int [ x ]] > high [ i ]) 8 18 do ? i and int [ x ] don’t overlap if left [ x ] ≠ NIL and low [ i ] ≤ m [ left [ x ]] 7,10 x ← root then x ← left [ x ] 10 [14,16] and [17,19] don’t overlap else x ← right [ x ] 14 ≤ 18 ⇒ x ← left [ x ] return x 3/2/06 15 3/2/06 16 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms
Example 1: I NTERVAL -S EARCH ([14,16]) Example 1: I NTERVAL -S EARCH ([14,16]) 17,19 17,19 23 23 14 16 14 16 5,11 22,23 5,11 22,23 x 18 23 18 23 4,8 15,18 4,8 15,18 x 8 18 8 18 7,10 7,10 10 10 [14,16] and [5,11] don’t overlap [14,16] and [15,18] overlap 14 > 8 ⇒ x ← right [ x ] return [15,18] 3/2/06 17 3/2/06 18 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms Example 2: I NTERVAL -S EARCH ([12,14]) Example 2: I NTERVAL -S EARCH ([12,14]) 17,19 17,19 x 23 23 12 14 12 14 5,11 22,23 5,11 22,23 x 18 23 18 23 4,8 15,18 4,8 15,18 8 18 8 18 7,10 7,10 x ← root 10 10 [12,14] and [17,19] don’t overlap [12,14] and [5,11] don’t overlap 12 ≤ 18 ⇒ x ← left [ x ] 12 > 8 ⇒ x ← right [ x ] 3/2/06 19 3/2/06 20 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms
Example 2: I NTERVAL -S EARCH ([12,14]) Example 2: I NTERVAL -S EARCH ([12,14]) 17,19 17,19 23 23 12 14 12 14 5,11 22,23 5,11 22,23 18 23 18 23 4,8 15,18 4,8 15,18 x 8 18 8 18 7,10 7,10 x 10 10 x = NIL ⇒ no interval that [12,14] and [15,18] don’t overlap 12 > 10 ⇒ x ← right [ x ] overlaps [12,14] exists 3/2/06 21 3/2/06 22 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms Analysis Correctness Theorem. Let L be the set of intervals in the Time = O ( h ) = O (log n ), since I NTERVAL - left subtree of node x , and let R be the set of S EARCH does constant work at each level as it intervals in x ’s right subtree. follows a simple path down the tree. • If the search goes right, then List all overlapping intervals: { i ′ ∈ L : i ′ overlaps i } = ∅ . • Search, list, delete, repeat. • If the search goes left, then • Insert them all again at the end. { i ′ ∈ L : i ′ overlaps i } = ∅ Time = O ( k log n ), where k is the total number ⇒ { i ′ ∈ R : i ′ overlaps i } = ∅ . of overlapping intervals. In other words, it’s always safe to take only 1 This is an output-sensitive bound. of the 2 children: we’ll either find something, Best algorithm to date: O ( k + log n ). or nothing was to be found. 3/2/06 23 3/2/06 24 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms
Correctness proof Proof (continued) Suppose that the search goes left, and assume that Proof. Suppose first that the search goes right. { i ′ ∈ L : i ′ overlaps i } = ∅ . • If left [ x ] = NIL , then we’re done, since L = ∅ . • Then, the code dictates that low [ i ] ≤ m [ left [ x ]] = • Otherwise, the code dictates that we must have high [ j ] for some j ∈ L. low [ i ] > m [ left [ x ]]. The value m [ left [ x ]] • Since j ∈ L , it does not overlap i , and hence corresponds to the right endpoint of some high [ i ] < low [ j ]. interval j ∈ L , and no other interval in L can • But, the binary-search-tree property implies that have a larger right endpoint than high ( j ). for all i ′ ∈ R , we have low [ j ] ≤ low [ i ′ ]. i L • But then { i ′ ∈ R : i ′ overlaps i } = ∅ . high ( j ) = m [ left [ x ]] low ( i ) i j • Therefore, { i ′ ∈ L : i ′ overlaps i } = ∅ . i ′ L 3/2/06 25 3/2/06 26 CS 5633 Analysis of Algorithms CS 5633 Analysis of Algorithms
Recommend
More recommend