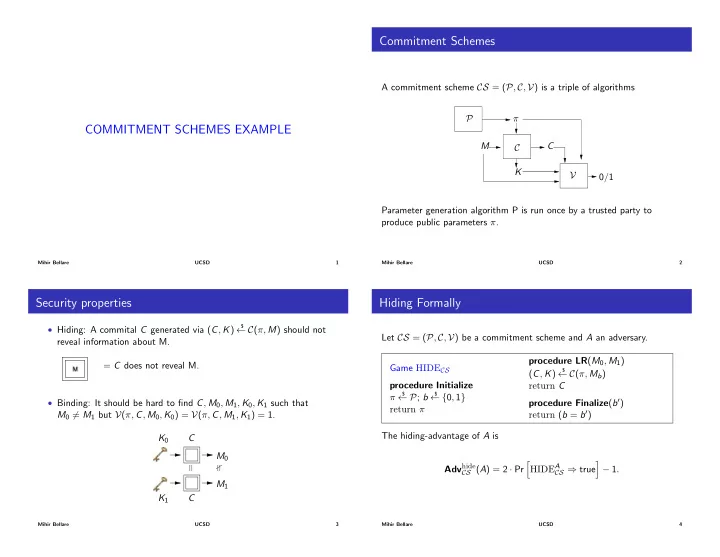

Commitment Schemes A commitment scheme CS = ( P , C , V ) is a triple of algorithms P π COMMITMENT SCHEMES EXAMPLE M C C K V 0/1 Parameter generation algorithm P is run once by a trusted party to produce public parameters π . Mihir Bellare UCSD 1 Mihir Bellare UCSD 2 Security properties Hiding Formally $ • Hiding: A commital C generated via ( C , K ) C ( π , M ) should not Let CS = ( P , C , V ) be a commitment scheme and A an adversary. reveal information about M. procedure LR ( M 0 , M 1 ) = C does not reveal M. Game HIDE CS $ ( C , K ) C ( π , M b ) procedure Initialize return C $ $ P ; b { 0 , 1 } π • Binding: It should be hard to find C , M 0 , M 1 , K 0 , K 1 such that procedure Finalize ( b 0 ) return π M 0 6 = M 1 but V ( π , C , M 0 , K 0 ) = V ( π , C , M 1 , K 1 ) = 1. return ( b = b 0 ) The hiding-advantage of A is K 0 C M 0 h i Adv hide HIDE A CS ( A ) = 2 · Pr CS ) true � 1 . M 1 K 1 C Mihir Bellare UCSD 3 Mihir Bellare UCSD 4
Binding Formally Recall: PS9 Let p be a prime of bit length k � 8 such that ( p � 1) / 2 is also prime. Let Let CS = ( P , C , V ) be a commitment scheme and A an adversary. g , h be two, di ff erent generators of the group G = Z ⇤ p . Let CS = ( P , C , V ) be the commitment scheme whose constituent algorithms are as follows, Game BIND CS procedure Finalize ( C , M 0 , M 1 , K 0 , K 1 ) where the message M is in Z p � 1 : v 0 V ( π , C , M 0 , K 0 ) procedure Initialize v 1 V ( π , C , M 1 , K 1 ) Alg P $ P π return ( v 0 = v 1 = 1 and M 0 6 = M 1 ) π ( g , h ) return π Alg V (( g , h ) , ( C 1 , C 2 ) , M , K ) Return π If ( { K , M } 6✓ Z p � 1 ) then return 0 The binding-advantage of A is 1 ( g K · h M ) mod p C 0 Alg C (( g , h ) , M ) C 0 2 ( M + K ) mod ( p � 1) $ If (( C 1 = C 0 1 ) and ( C 2 = C 0 2 )) h i K Z p � 1 Adv bind BIND A CS ( A ) = Pr CS ) true . C 1 ( g K · h M ) mod p then return 1 Return 0 C 2 ( M + K ) mod ( p � 1) Return (( C 1 , C 2 ) , K ) Mihir Bellare UCSD 5 Mihir Bellare UCSD 6 Recall: PS9 PS9 Solution For each of the following, clearly circle either YES or NO below: For each of the following, clearly circle either YES or NO below: • If your answer is YES, prove that any adversary A for the security • If your answer is YES, prove that any adversary A for the security game in question has advantage 0. game in question has advantage 0. • If it is NO, specify in pseudocode an O ( k 3 + T H )-time adversary A • If it is NO, specify in pseudocode an O ( k 3 + T H )-time adversary A achieving advantage 1 for the security game in question: achieving advantage 1 for the security game in question: 1. Does CS provide hiding security? 1. Does CS provide hiding security? YES NO YES NO 2. Does CS provide binding security? 2. Does CS provide binding security? YES NO YES NO Mihir Bellare UCSD 7 Mihir Bellare UCSD 8
The hiding adversary The binding adversary Alg V (( g , h ) , ( C 1 , C 2 ) , M , K ) Alg C (( g , h ) , M ) If ( { K , M } 6✓ Z p � 1 ) then return 0 Z p � 1 ; C 1 ( g K · h M ) mod p ; C 2 ( M + K ) mod ( p � 1) $ K 1 ( g K · h M ) mod p ; C 0 C 0 2 ( M + K ) mod ( p � 1) Return (( C 1 , C 2 ) , K ) If (( C 1 = C 0 1 ) and ( C 2 = C 0 2 )) then return 1 else return 0 adversary A (( g , h )) adversary A (( g , h )) / / q = ( p � 1) / 2 $ ( C 1 , C 2 ) LR (1 , 0) ; X MOD - EXP ( g , C 2 , p ) K 0 0 ; M 0 0 ; K 1 q ; M 1 q ; C 1 1 ; C 2 0 If ( X = C 1 ) then return 1 else return 0 Return (( C 1 , C 2 ) , M 0 , M 1 , K 0 , K 1 ) C 1 C 2 X This works because g K h 0 mod p g K mod p M 0 = 1 K g 0 h 0 mod p = 1 g K h 1 mod p g K +1 mod p M 1 = 0 ( K + 1) mod ( p � 1) g q h q mod p = ( � 1)( � 1) mod p = 1 (0 + 0) mod ( p � 1) = 0 In the second case X 6 = C 1 because g 6 = h . ( q + q ) mod ( p � 1) = 0 Mihir Bellare UCSD 9 Mihir Bellare UCSD 10 Recall: PS9 Exercise: Scheme Let p be a prime of bit length k � 8 such that ( p � 1) / 2 is also prime. Let Let p be a prime of bit length k � 8 such that ( p � 1) / 2 is also prime. Let g , h be two, di ff erent generators of the group G = Z ⇤ p . Let CS = ( P , C , V ) g , h be two, di ff erent generators of the group G = Z ⇤ p . Let CS = ( P , C , V ) be the commitment scheme whose constituent algorithms are as follows, be the commitment scheme whose constituent algorithms are as follows, where the message M is in Z p � 1 : where the message M is in Z p � 1 : Alg P Alg P π ( g , h ) Alg V (( g , h ) , ( C 1 , C 2 ) , M , K ) π ( g , h ) Return π Alg V (( g , h ) , C , M , K ) If ( { K , M } 6✓ Z p � 1 ) then return 0 Return π 1 ( g K · h M ) mod p If ( { K , M } 6✓ Z p � 1 ) then return 0 C 0 C 0 ( g K · h M ) mod p Alg C (( g , h ) , M ) C 0 2 ( M + K ) mod ( p � 1) Alg C (( g , h ) , M ) If ( C = C 0 ) then return 1 $ If (( C 1 = C 0 1 ) and ( C 2 = C 0 2 )) K Z p � 1 $ K Z p � 1 C 1 ( g K · h M ) mod p Return 0 then return 1 C ( g K · h M ) mod p Return 0 C 2 ( M + K ) mod ( p � 1) Return ( C , K ) Return (( C 1 , C 2 ) , K ) Mihir Bellare UCSD 11 Mihir Bellare UCSD 12
Exercise: Questions Exercise: Scheme For each of the following, clearly circle either YES or NO below: • If your answer is YES, prove that any adversary A for the security In the new scheme, the committing algorithm drops the C 2 part of the game in question has advantage 0. committal ( C 1 , C 2 ), leaving just C = C 1 . • If it is NO, specify in pseudocode an O ( k 3 + T H )-time adversary A Correspondingly, the verification algorithm drops the second check. achieving advantage 1 for the security game in question: Do these changes make it EASIER or HARDER to attack the two 1. Does CS provide hiding security? properties? YES NO • Attacking HIDING should get • Attacking BINDING should get 2. Does CS provide binding security? YES NO Mihir Bellare UCSD 13 Mihir Bellare UCSD 14 Exercise: Scheme Exercise: Binding, the answer For each of the following, clearly circle either YES or NO below: • If your answer is YES, prove that any adversary A for the security game in question has advantage 0. In the new scheme, the committing algorithm drops the C 2 part of the • If it is NO, specify in pseudocode an O ( k 3 + T H )-time adversary A committal ( C 1 , C 2 ), leaving just C = C 1 . achieving advantage 1 for the security game in question: Correspondingly, the verification algorithm drops the second check. Do these changes make it EASIER or HARDER to attack the two 1. Does CS provide hiding security? properties? YES NO • Attacking HIDING should get HARDER • Attacking BINDING should get EASIER 2. Does CS provide binding security? YES NO The same adversary strategy as before works except C 2 is not needed. Mihir Bellare UCSD 15 Mihir Bellare UCSD 16
Exercise: Hiding, the answer Hiding, intuition For each of the following, clearly circle either YES or NO below: Alg C (( g , h ) , M ) • If your answer is YES, prove that any adversary A for the security $ K Z p � 1 game in question has advantage 0. C ( g K · h M ) mod p • If it is NO, specify in pseudocode an O ( k 3 + T H )-time adversary A Return ( C , K ) achieving advantage 1 for the security game in question: Regardless of the choice of message M , the random choice of K means that C is a random element of the group Z ⇤ p . Does CS provide hiding security? 1. Since the distribution of C does not depend on M , seeing C does not give YES NO any information about M . This is a start, but is not a proof. Mihir Bellare UCSD 17 Mihir Bellare UCSD 18 Hiding, example Hiding, example Let p = 7. Let p = 7. Let g = 3 and h = 5, which are generators of Z ⇤ 7 = { 1 , 2 , 3 , 4 , 5 , 6 } . Let g = 3 and h = 5, which are generators of Z ⇤ 7 = { 1 , 2 , 3 , 4 , 5 , 6 } . Adversary A picks messages M 0 = 2 and M 1 = 4 in Z 6 = { 0 , 1 , 2 , 3 , 4 , 5 } . Adversary A picks messages M 0 = 2 and M 1 = 4 in Z 6 = { 0 , 1 , 2 , 3 , 4 , 5 } . Row M , column K entry of table is T [ M , K ] = g K h M mod p : Row M , column K entry of table is T [ M , K ] = g K h M mod p : 0 1 2 3 4 5 0 1 2 3 4 5 2 4 5 1 3 2 6 2 4 5 1 3 2 6 4 2 6 4 5 1 3 4 2 6 4 5 1 3 $ $ $ $ Hiding game picks b { 0 , 1 } and K Z 6 . Hiding game picks b { 0 , 1 } and K Z 6 . Adversary A gets C = T [ M b , K ] and asks, what is b ? Adversary A gets C = T [ M b , K ] and asks, what is b ? Suppose for example C = 5. Then • Either M = 2 ( b = 0) and K = 1 • Or M = 4 ( b = 1) and K = 3 and adversary has no idea which. Mihir Bellare UCSD 19 Mihir Bellare UCSD 20
Recommend
More recommend