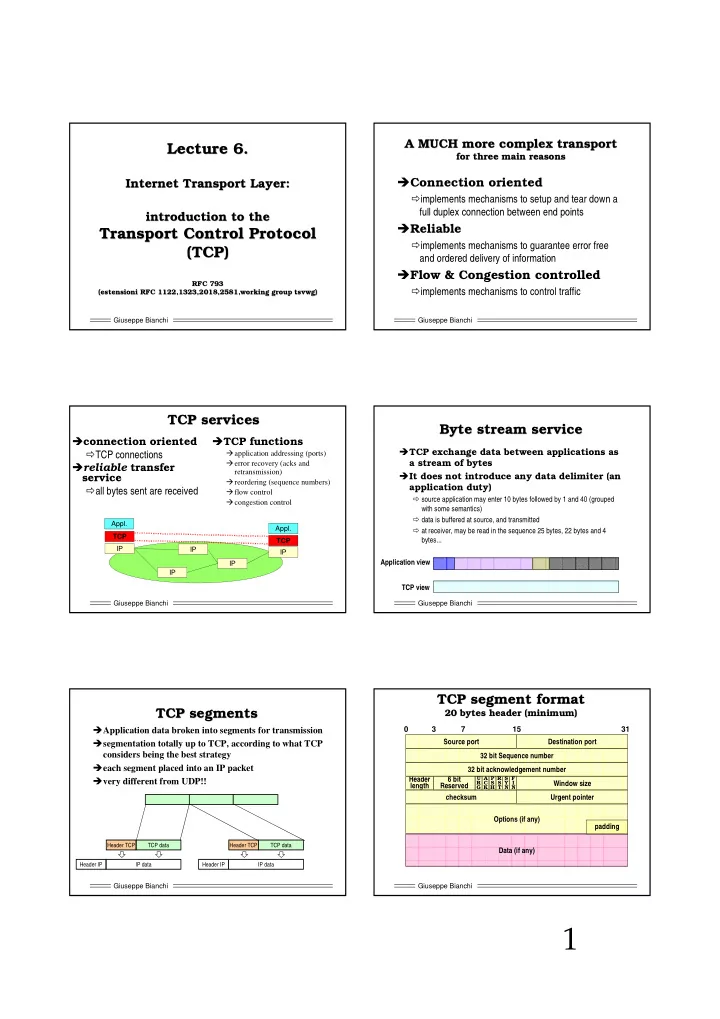

A MUCH more complex complex transport transport A MUCH more Lecture 6. Lecture 6. for for three three main main reasons reasons � Connection oriented Internet Transport Layer: Internet Transport Layer: � implements mechanisms to setup and tear down a full duplex connection between end points introduction to the introduction to the � Reliable Transport Control Protocol Transport Control Protocol � implements mechanisms to guarantee error free (TCP) (TCP) and ordered delivery of information � Flow & Congestion controlled RFC 793 RFC 793 � implements mechanisms to control traffic (estensioni estensioni RFC 1122,1323,2018,2581,working group RFC 1122,1323,2018,2581,working group tsvwg tsvwg) ) ( Giuseppe Bianchi Giuseppe Bianchi TCP services TCP services Byte stream Byte stream service service � connection oriented � TCP functions � TCP exchange data between applications as � TCP connections � application addressing (ports) � error recovery (acks and a stream of bytes � reliable transfer retransmission) � It does not introduce any data delimiter (an service � reordering (sequence numbers) application duty) � all bytes sent are received � flow control � source application may enter 10 bytes followed by 1 and 40 (grouped � congestion control with some semantics) � data is buffered at source, and transmitted Appl. Appl. � at receiver, may be read in the sequence 25 bytes, 22 bytes and 4 TCP bytes... TCP IP IP IP Application view IP IP TCP view Giuseppe Bianchi Giuseppe Bianchi TCP TCP segment segment format format TCP segments segments TCP 20 bytes bytes header header (minimum) (minimum) 20 � Application data broken into segments for transmission 0 3 7 15 31 � segmentation totally up to TCP, according to what TCP Source port Destination port considers being the best strategy 32 bit Sequence number � each segment placed into an IP packet 32 bit acknowledgement number � very different from UDP!! Header 6 bit U A P R S F R C S S Y I Window size length Reserved G K H T N N checksum Urgent pointer Options (if any) padding Header TCP TCP data Header TCP TCP data Data (if any) Header IP IP data Header IP IP data Giuseppe Bianchi Giuseppe Bianchi 1
Source port Destination port Source port Destination port 32 bit Sequence number 32 bit Sequence number 32 bit acknowledgement number 32 bit acknowledgement number Header 6 bit U A P R S F Header 6 bit U A P R S F Window size Window size R C S S Y I R C S S Y I length Reserved length Reserved G K H T N N G K H T N N checksum Urgent pointer checksum Urgent pointer � Source & destination port + source and Options (if any) 00000000 destination IP addresses � univocally determine TCP connection � Header length: 4 bits � specifies the header size (n*4byte words) for options � checksum as in UDP � maximum header size: 60 (15*4) � same calculation including same pseudoheader � option field size must be multiple of 32bits: zero padding � no explicit segment length specification when not. � Reserved: 000000 (still today!) Giuseppe Bianchi Giuseppe Bianchi Retransmission scenarios scenarios Retransmission Reliable data transfer: data transfer: issues issues Reliable referred to referred to as as ARQ ARQ schemes schemes ( (A Automatic utomatic R Repeat epeat re reQ Quest uest) ) COMPONENTS: a) error checking at receiver; b) feedback to sender; c) retx packet PROBLEMS: packet 1) Packet received with errors INTERNET SRC SRC 2) Packet not received at all DST DST DATA DATA Error Error Check: Check: Same problem considered at DATA LINK LAYER K C K A C OK N A corrupted (although it is less likely that a whole packet is lost at data link) Automatic retransmit DATA � mechanisms to guarantee correct reception: Basic ACK idea Basic NACK idea � Forward Error Correction (FEC) coding schemes � Powerful to correct bits affected by error, less effective in SRC SRC SRC DST DST DST case of packet loss DATA DATA DATA � Mostly used at link layer Retx Error � Retransmission – issues: C K Timeout A Check: (RTO) corrupted � ACK DATA DATA DATA � NACK � TIMEOUT Basic ACK/Timeout idea Giuseppe Bianchi Giuseppe Bianchi Why sequence Why sequence numbers numbers? ? Why Why sequence sequence numbers numbers? ? (on data) (on ack ack) ) (on data) (on Sender side: Receiver side: Sender side: Receiver side: DATA DATA 1 DATA K C RTO A Duplicated K A C ACK NETWORK DATA 2 Queueing (ACK lost) Delay rtx DATA K A C DATA New data? DATA 3 Old data? Data 2 lost !! With pathologically critical network (as the Internet!) Need to univocally “label” all packets circulating also need to univocally “label” all acks circulating in the network between two end points. in the network between two end points. 1 bit (0-1) enough for Stop-and-wait 1 bit (0-1) enough for Stop-and-wait Giuseppe Bianchi Giuseppe Bianchi 2
Source port Destination port TCP data transfer management TCP data transfer management 32 bit Sequence number � Full duplex connection 32 bit acknowledgement number � data flows in both directions, independently Header 6 bit U A P R S F Window size R C S S Y I length Reserved G K H T N N � To the application program these appear as two unrelated checksum Urgent pointer data streams � Impossible to build multicast connection � Sequence number: � each end point maintains a sequence � Sequence number of the first byte in the segment. � When reaches 2 32 -1, next wraps back to 0 number � Independent sequence numbers at both ends � Acknowledgement number: � Measured in bytes � valid only when ACK flag on � acks often carried on top of reverse � Contains the next byte sequence number that the host expects to receive (= last successfully received byte of data + 1) flow data segments (piggybacking) � grants successful reception for all bytes up to ack# - 1 (cumulative) � But ack packets alone are possible � When seq/ack reach 2 32 -1, next wrap back to 0 Giuseppe Bianchi Giuseppe Bianchi Byte- -oriented oriented Pipelining Byte Pipelining Example: 1024 bytes msg; seg_size = 536 bytes � 2 segments: 0-535; 536-1023 Example: 1 kbyte message – 1024 bytes 0 1 … … 100 … … 535 … … … 1023 0 1 … … 100 … … 535 … … … 1023 Example: segment size = 536 bytes � 2 segments: 0-535; 536-1023 sender receiver seq=0 � ����� ���� receiver sender seq=536 seq=0 � sliding window mechanisms � ����������� ������� ���� Ack=536 � ���������������� ��� �������������� ���������� � Go-Back-N and Selective Repeat Ack=1024 Ack=536 � ��� ������������������� seq=536 � ��������� ��� ������ ����� ������ ��� � ������� ���� ���������� Ack=1024 time time Why pipelining? Dramatic improvement in efficiency! time time Giuseppe Bianchi Giuseppe Bianchi Cumulative ack Cumulative ack Multiple acks acks; ; Piggybacking Piggybacking Multiple Example: 1024 bytes msg; seg_size = 536 bytes � 2 segments: 0-535; 536-1023 Bytes 100-199, seq=100, 0 1 … … 100 … … 535 … … … 1023 receiver sender seq=0 Immediate ack, EMPTY, Ack=200 � �������������� no payload Bytes 450-525, seq=450, ack=200 Data in reverse seq=536 � ������ ��� ����� �� ����� direction,carries � ������� �������!"� previous ack � E.g. ACK=1024: all bytes 0-1023 Ack=1024 received Bytes 200-249, seq=200, ack=526 � ����� ����� �������������� � Go-Back-N ARQ mechanisms � Sliding window mechanisms time time Next segment, CLIENT SERVER piggybacked ack Why pipelining? Dramatic improvement in efficiency! Giuseppe Bianchi Giuseppe Bianchi 3
Recommend
More recommend