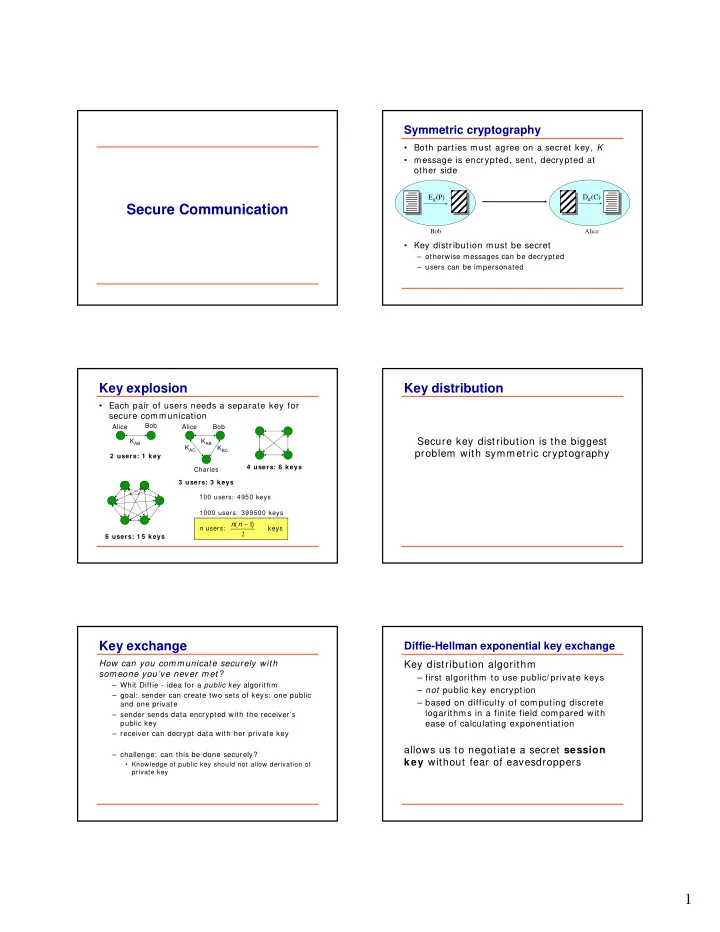

Symmetric cryptography • Both parties must agree on a secret key, K • message is encrypted, sent, decrypted at other side E K (P) D K (C) Secure Communication Bob Alice • Key distribution must be secret – otherwise messages can be decrypted – users can be impersonated Key explosion Key distribution • Each pair of users needs a separate key for secure comm unication Bob Alice Alice Bob Secure key distribution is the biggest K AB K AB K AC K BC problem with symmetric cryptography 2 users: 1 key 4 users: 6 keys Charles 3 users: 3 keys 100 users: 4950 keys 1000 users: 399500 keys − n ( n 1 ) n users: keys 2 6 users: 1 5 keys Key exchange Diffie-Hellman exponential key exchange How can you communicate securely with Key distribution algorithm someone you’ve never met? – first algorithm to use public/ private keys – Whit Diffie - idea for a public key algorithm – not public key encryption – goal: sender can create two sets of keys: one public – based on difficulty of computing discrete and one private logarithms in a finite field compared with – sender sends data encrypted with the receiver’s ease of calculating exponentiation public key – receiver can decrypt data with her private key allows us to negotiate a secret session – challenge: can this be done securely? key without fear of eavesdroppers • Knowledge of public key should not allow derivation of private key 1
Diffie-Hellman exponential key exchange Diffie-Hellman exponential key exchange • Alice has secret key • Bob has secret key • All arithmetic perform ed in X A X B field of integers modulo some large number • Alice has public key • Bob has public key • Both parties agree on Y A Y B – a large prim e num ber p – and a number α < p • Alice computes = X • Each party generates a public/ private key pair K Y A mod p B private key for user i : X i K = ( Bob’s public key) ( Alice’s private key) m od p X mod α public key for user i : Y i = i p Diffie-Hellman exponential key exchange Diffie-Hellman exponential key exchange • Alice has secret key • Bob has secret key • Alice has secret key • Bob has secret key X A X B X A X B • Alice has public key • Bob has public key • Alice has public key • Bob has public key Y A Y B Y A Y B • Alice computes • Bob computes • Alice computes • Bob computes = ' = = ' = X X X X K Y mod p K Y mod p K Y mod p K Y mod p A B A B B A B A • expanding: • expanding: K’ = ( Alice’s public key) ( Bob’s private key) m od p = = X X K Y A mod p K ' Y B mod p B A = α = α X X X X ( mod p ) mod p ( mod p ) mod p B A A B = α = α X X X X B A mod p A B mod p K = K’ K is a com m on key , known only to Bob and Alice Diffie-Hellman example Key distribution problem is solved! Suppose p = 31667, α = 7 • User maintains private key • Publishes public key in database (“phonebook”) • Bob picks • Alice picks X B = 27 X A = 18 • Bob’s public key is: • Communication begins with key exchange to • Alice’s public key is: Y B = 7 27 mod 31667 establish a com mon key Y A = 7 18 mod 31667 = 22184 = 6780 • Common key can be used to encrypt a session key • K = 6780 27 mod – increase difficulty of breaking common key by • K = 22184 18 mod reducing the amount of data we encrypt with it 31667 31667 – session key is valid only for one communication K = 1 4 2 6 5 K = 1 4 2 6 5 session 2
RSA RSA algorithm Generate keys • Ron Rivest, Adi Shamir, Leonard Adleman created a true public key encryption algorithm in 1977 – choose two random large prim e numbers p , q • Each user generates two keys – Compute the product n= pq – private key (kept secret) – random ly choose the encryption key, e , such – public key that • Data encrypted with the private key can only be e and ( p -1)( q -1) are relatively prime decrypted with the corresponding public key – use the extended Euclidean algorithm to – integrity, authentication compute the decryption key, d : • Data encrypted with the public key can only be ed = 1 m od (( p -1)( q -1)) decrypted with the corresponding private key d = e -1 mod (( p -1)( q -1)) – secure comm unication • difficulty of algorithm based on the difficulty of factoring – discard p , q large numbers – keys are functions of a pair of large (~ 200 digits) prime numbers RSA algorithm Communication with public key algorithms • encrypt Different keys for encrypting and – divide data into numerical blocks < n decrypting – encrypt each block: – no need to worry about key distribution c = m e m od n • decrypt: m = c d m od n Communication with public key algorithms Communication with public key algorithms Alice Bob Alice Bob Alice’s public key: K A Alice’s public key: K A Alice’s public key: K A Alice’s public key: K A Bob’s public Bob’s public Bob’s public key: K B Bob’s public key: K B key: K B key: K B exchange public keys E B (P) D b (C) (or look up in a directory/ DB) encrypt message with decrypt message with Bob’s private key Bob’s public key 3
Public key woes Communication with public key algorithms Alice Bob Public key cryptography is great but: Alice’s public key: K A Alice’s public key: K A – RSA about 100 times slower than DES in Bob’s public key: K B Bob’s public key: K B software, 1000 times slower in HW – Vulnerable to chosen plaintext attack E B (P) D b (C) • if you know the data is one of n messages, just encrypt each message with the recipient’s public key encrypt message with decrypt message with and compare Bob’s public key Bob’s private key – It’s a good idea to reduce the amount of data E A (P) D a (C) encrypted with any given key • but generating RSA keys is computationally very time consuming encrypt message with decrypt message with Alice’s private key Alice’s public key Hybrid cryptosystems Communication with a hybrid cryptosystem Alice Bob Use public key cryptography to encrypt a randomly generated symmetric key Bob’s public key: K B Bob’s public key: K B Get recipient’s public key session key (or fetch from directory/ database) Communication with a hybrid cryptosystem Communication with a hybrid cryptosystem Alice Bob Alice Bob Bob’s public key: K B Bob’s public key: K B Bob’s public key: K B Bob’s public key: K B E B ( K ) K = D b (E B ( K )) E B ( K ) Pick random session key, K Encrypt session key with Bob’s public key E K (P) D K (C) E B ( K ) K = D b (E B ( K )) E B ( K ) Bob decrypts K with his private key encrypt message using a decrypt message using a symmetric algorithm symmetric algorithm and key K and key K 4
Communication with a hybrid cryptosystem Alice Bob Bob’s public key: K B Bob’s public key: K B E B ( K ) K = D b (E B ( K )) E B ( K ) E K (P) D K (C) Digital Signatures E K (P’) D K (C’) decrypt message using a encrypt message using a symmetric algorithm symmetric algorithm and key K and key K Digital signatures Digital signatures We use signatures because a signature is: We use signatures because a signature is Authentic Unforgeable Authentic Unforgeable Not reusable Non repudiatable Not reusable Non repudiatable Renders docum ent unalterable Renders docum ent unalterable ALL UNTRUE! Can we do better with digital signatures? Digital signatures - arbitrated protocol Digital signatures - arbitrated protocol Arbitrated protocol using sym m etric encryption – turn to trusted third party (arbiter) to authenticate messages Trent Trent Trent is trusted P= D A (C) and has everyone’s keys C= E A (P) Alice Bob Alice Bob Trent receives Alice’s message and decrypts it with Alice’s key - this authenticates that it came from Alice - he may choose to log a hash of the message to Alice encrypts message for herself and sends it to Trent create a record of the transmission 5
Digital signatures - arbitrated protocol Digital signatures - arbitrated protocol Trent Trent C’= E B (P) P’= D B (C’) Bob Bob Alice Alice Bob receives the message and decrypts it - it must have come from Trent since only Trent and Bob have Bob’s key Trent now encrypts the message for Bob and sends it to Bob - if the message says it’s from Alice, it must be - we trust Trent Digital signatures with multiple parties Digital signatures with multiple parties Bob can forward the message to Charles in the same manner. Trent can validate stored hash to ensure that Bob did not alter the message Trent Charles Trent Charles P’’= D B (C’’) C’’= E B (P’) P’= D B (C’) Alice Bob Alice Bob Trent decrypts the message - knows it must be from Bob - looks up ID to match original hash from Alice’s message - validates that the message has not been modified Bob encrypts message with his key and sends it to Trent - adds a “signed by Bob” indicator to the message Digital signatures with multiple parties Digital signatures with multiple parties Charles Charles Trent Trent C’’’= E C (P’’) P’’’= D C (C’’’) Alice Bob Alice Bob Charles decrypts the message - knows the message must have come from Trent - trusts Trent’s assertion that the message originated with Alice Trent encrypts the new message for Charles and was forwarded through Bob 6
Recommend
More recommend